MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works The folks at BeyondTrust have …
Category: Security
Nov 21 2014
Microsoft KB2871997: Back-Porting Windows 8.1/Win2012R2 Enhanced Security & Pass The Hash Mitigation to Windows 7, Windows 8, & Windows 2008R2
In June 2014, Microsoft released KB2871997 which takes many of the enhanced security protection mechanisms built into Windows 8.1 & Windows Server 2012 R2 and “back-ports” them to Windows 7, Windows 8, Windows Server 2008R2, and Windows Server 2012. The enhanced security features reduce the credential data stored in memory and supports modern authentication (Kerberos …
Nov 19 2014
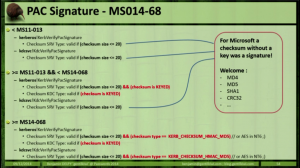
Kerberos Vulnerability in MS14-068 (KB3011780) Explained
Thanks to Gavin Millard (@gmillard on Twitter), we have a graphic that covers the issue quite nicely (wish I had of thought of it!) Exploit Code is now on the net! As of December 4th, 2014, there is Proof of Concept (POC) code posted that exploits MS14-068 by Sylvain Monné by using Python to interact with …
Nov 18 2014
MS14-068: Vulnerability in (Active Directory) Kerberos Could Allow Elevation of Privilege
Active Directory leverages the Kerberos protocol for authentication. The vulnerability patches an issue with how the Domain Controller validates group membership in Kerberos tickets (hint: the ticket is always validated by the DC if the checksum is set to certain values). Microsoft KB3011780 patches this issue. According to Microsoft: “When this security bulletin was issued, …
Nov 15 2014
Owning Networks and Evading Incident Response with PowerShell
PowerShell provides an easy method to bypass antivirus and other protection methods: Up until several months ago, I was a member of a penetration test team tasked with compromising data centers and evading detection. Industry standard tools such as Metasploit (an attack toolkit that includes a backdoor named Meterpreter) and Mimikatz (a password dumper) …
Nov 13 2014
EMET v5.1 Released
This week, Microsoft released version 5.1 of their Enhanced Mitigation Experience Toolkit (EMET). EMET 5.1 can be download from the Microsoft EMET website. Microsoft Security Research and Defense Blog describes the update: Today, we’re releasing the Enhanced Mitigation Experience Toolkit (EMET) 5.1 which will continue to improve your security posture by providing increased application compatibility …
Nov 12 2014
Microsoft’s HeartBleed: The Schannel SSL/TLS vulnerability (MS14-066)
Earlier this year, Unix/Linux/*nix systems dealt with the “Hearbleed” OpenSSL vulnerability which affected a large portion of the web. There is a major vulnerability in Microsoft’s Schannel which was recently patched in MS14-066 (KB2992611). What is SChannel? The Secure Channel (Schannel) security package is a Security Support Provider (SSP) that implements the Secure Sockets Layer …
Nov 11 2014
Another SSL Attack: POODLE
SSL used to be the foremost method for securing web communications until around 1999 when TLS 1.0 was released. BEAST demonstrated inherent flaws in the aging SSL 3 protocol (RC4!). Now, POODLE demonstrates that SSL3 needs to be disabled on the client AND server side. Note that the chance of this specific issue being the …
Nov 10 2014
Kerberos & KRBTGT: Active Directory’s Domain Kerberos Service Account
Every Domain Controller in an Active Directory domain runs a KDC (Kerberos Distribution Center) service which handles all Kerberos ticket requests. AD uses the KRBTGT account in the AD domain for Kerberos tickets. The KRBTGT account is one that has been lurking in your Active Directory environment since it was first stood up. Each Active …
Nov 09 2014
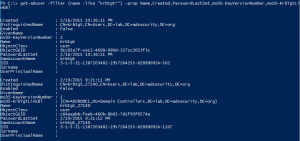
PowerShell Code: Check KRBTGT Domain Kerberos Account Last Password Change
From my GitHub Repo: Get-PSADForestKRBTGTInfo This function discovers all of the KRBTGT accounts in the forest using ADSI and returns the account info, specifically the last password change. Currently, the script performs the following actions: * Queries a Global Catalog in the Active Directory root domain for all KRBTGT accounts in the forest by querying …


Recent Comments