Over the last 6 months, I have been researching forged Kerberos tickets, specifically Golden Tickets, Silver Tickets, and TGTs generated by MS14-068 exploit code (a type of Golden Ticket). I generated forged Kerberos tickets using Mimikatz (Mimikatz Command Reference) and MS14-068 exploits and logged the results. Over the course of several weeks, I identified anomalies …
Tag: ActiveDirectory
Feb 18 2015
Interesting KRBTGT Password Reset Behavior
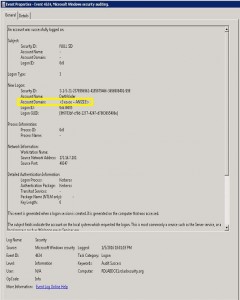
Following up on Twitter conversations (@passingthehash, @scriptjunkie1, gentilkiwi, etc) on the new KRBTGT Password Reset Script and Skip Duckwall’s (@passingthehash) blog post on how KRBTGT password changes work. Microsoft KB2549833 states that the KRBTGT password is set automatically to a random string when a new password is entered. This occurs because there is special logic …
Feb 11 2015
MS15-011 & MS15-014: Microsoft Active Directory Group Policy (GPO) Vulnerabilities Patched
On February’s Patch Tuesday (2/11/2015), Microsoft released two patches that fix issues with the way Group Policy is processed by the client. Interestingly enough, one of these vulnerabilities (MS15-014) makes the other one (MS15-011) not only feasible, but quite capable. The Attack Scenario: An attacker leverages the vulnerability described in MS15-014 to prevent/stop Group Policy …
Jan 19 2015
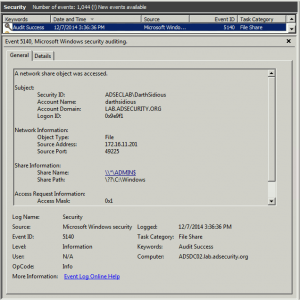
Attackers Can Now Use Mimikatz to Implant Skeleton Key on Domain Controllers & BackDoor Your Active Directory Forest
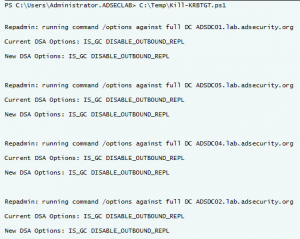
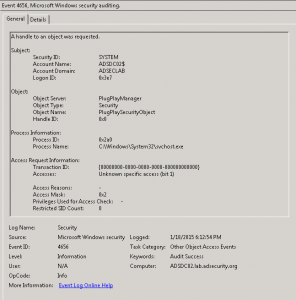
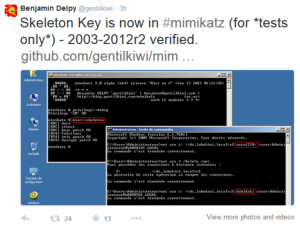
Once an attacker has gained Domain Admin rights to your Active Directory environment, there are several methods for keeping privileged access. Skeleton Key is an ideal persistence method for the modern attacker. More information on Skeleton Key is in my earlier post. Note that the behavior documented in this post was observed in a lab …
Jan 16 2015
Active Directory Domain Controller Skeleton Key Malware & Mimikatz
Dell SecureWorks posted about the Skeleton Key malware discovered at a customer site. The Skeleton Key malware is installed on one or multiple Domain Controllers running a supported 64bit OS. The malware “patches” the security system enabling a new master password to be accepted for any domain user, including admins. This enables the attacker to …
Jan 14 2015
Windows Server 2012 & Windows Server 2012 R2 Complete Documentation
Microsoft took all the Windows Server 2012 (& 2012 R2) documentation and posted it as a single PDF! Version: 1.0 File Name: WS12_R2_and_WS12_TechNet.pdf Date Published: 2/18/2014 File Size: 125.9 MB This download is an Adobe® PDF of the entire contents of the Windows Server 2012 R2 and Windows Server 2012 section of the Microsoft TechNet …
Dec 15 2014
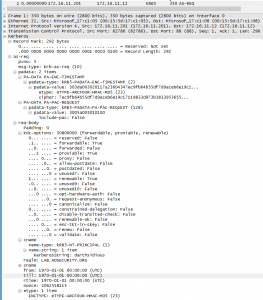
Detecting MS14-068 Kerberos Exploit Packets on the Wire aka How the PyKEK Exploit Works
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) This post shows the packet captures I performed using WireShark on the Domain Controllers during stage 1 and …
Dec 07 2014
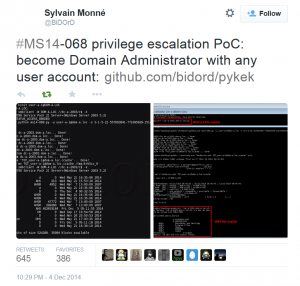
Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK)
MS14-068 References: AD Kerberos Privilege Elevation Vulnerability: The Issue Detailed Explanation of MS14-068 MS14-068 Exploit POC with the Python Kerberos Exploitation Kit (aka PyKEK) Detecting PyKEK Kerberos Packets on the Wire aka How the MS14-068 Exploit Works After re-working my lab a bit, I set about testing the MS14-068 POC that Sylvain Monné posted to …
Dec 05 2014
Windows Computer Primary Group IDs
Primary Group IDs are the RIDs for the Domain groups. The full list is here: Interesting Windows Computer & Active Directory Well-Known Security Identifiers (SIDs). 515 – Domain Computers 516 – Domain Controllers (writable) 521 – Domain Controllers (Read-Only) This information helps filter computer objects to return only the desired computer type. Domain Computers (Workstation …

Recent Comments