There are times when you want to know how long it takes for a script to run. One of the Measure-* cmdlets can be useful, but there is a simpler way to time how long it takes to run a script (or piece of code). The StopWatch .NET method is an ideal method for script …
November 2014 archive
Nov 15 2014
Owning Networks and Evading Incident Response with PowerShell
PowerShell provides an easy method to bypass antivirus and other protection methods: Up until several months ago, I was a member of a penetration test team tasked with compromising data centers and evading detection. Industry standard tools such as Metasploit (an attack toolkit that includes a backdoor named Meterpreter) and Mimikatz (a password dumper) …
Nov 15 2014
Active Directory Replication Overview & USN Rollback: What It Is & How It Happens
If you have experienced event id #2095, then you understand how a USN Rollback can negatively affect AD consistency. What is a USN? The USN (Update Sequence Number) is an Active Directory database instance counter that increments every time a single change is committed to the AD database on a Domain Controller. The USN is …
Nov 14 2014
Group Policy Settings Reference Guide for Windows 8.1 | 7 | Server
The Group Policy is an integral part of the Windows operating system, on which many a IT Pro, Beginners and Tweak enthusiasts count on to customize and enforce settings on their computers. The Group Policy Editor (Gpedit.msc) is one of the most useful tools for administering policy on Windows. The Group Policy Editor, however …
Nov 13 2014
EMET v5.1 Released
This week, Microsoft released version 5.1 of their Enhanced Mitigation Experience Toolkit (EMET). EMET 5.1 can be download from the Microsoft EMET website. Microsoft Security Research and Defense Blog describes the update: Today, we’re releasing the Enhanced Mitigation Experience Toolkit (EMET) 5.1 which will continue to improve your security posture by providing increased application compatibility …
Nov 12 2014
Microsoft’s HeartBleed: The Schannel SSL/TLS vulnerability (MS14-066)
Earlier this year, Unix/Linux/*nix systems dealt with the “Hearbleed” OpenSSL vulnerability which affected a large portion of the web. There is a major vulnerability in Microsoft’s Schannel which was recently patched in MS14-066 (KB2992611). What is SChannel? The Secure Channel (Schannel) security package is a Security Support Provider (SSP) that implements the Secure Sockets Layer …
Nov 11 2014
Another SSL Attack: POODLE
SSL used to be the foremost method for securing web communications until around 1999 when TLS 1.0 was released. BEAST demonstrated inherent flaws in the aging SSL 3 protocol (RC4!). Now, POODLE demonstrates that SSL3 needs to be disabled on the client AND server side. Note that the chance of this specific issue being the …
Nov 10 2014
Kerberos & KRBTGT: Active Directory’s Domain Kerberos Service Account
Every Domain Controller in an Active Directory domain runs a KDC (Kerberos Distribution Center) service which handles all Kerberos ticket requests. AD uses the KRBTGT account in the AD domain for Kerberos tickets. The KRBTGT account is one that has been lurking in your Active Directory environment since it was first stood up. Each Active …
Nov 09 2014
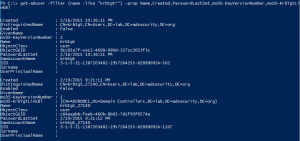
PowerShell Code: Check KRBTGT Domain Kerberos Account Last Password Change
From my GitHub Repo: Get-PSADForestKRBTGTInfo This function discovers all of the KRBTGT accounts in the forest using ADSI and returns the account info, specifically the last password change. Currently, the script performs the following actions: * Queries a Global Catalog in the Active Directory root domain for all KRBTGT accounts in the forest by querying …
Nov 08 2014
Mandiant MIRCon 2014 Presentation Slides
Using some Google-Fu, I was able to find some MIRCon 2014 presentation slides (sorry, no videos yet). Mandiant MIRCon 2014 Presentation Slides: R&D Track: An Insight into Symbiotic APT Groups IR Track: The Best and Worst APT Malware OSX Malware Plists, Shell Scripts and Object-C Oh-My! APT Detection with Whitelisting and Log Monitoring Management Track: …

Recent Comments