There are many ways an attacker can gain Domain Admin rights in Active Directory. This post is meant to describe some of the more popular ones in current use. The techniques described here “assume breach” where an attacker already has a foothold on an internal system and has gained domain user credentials (aka post-exploitation). The …
14 results for kerberoasting
Dec 31 2015
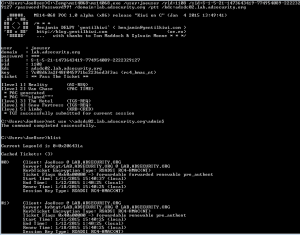
Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain
Microsoft’s Kerberos implementation in Active Directory has been targeted over the past couple of years by security researchers and attackers alike. The issues are primarily related to the legacy support in Kerberos when Active Directory was released in the year 2000 with Windows Server 2000. This legacy support is enabled when using Kerberos RC4 encryption …
Sep 26 2015
Sneaky Active Directory Persistence Tricks
The content in this post links to several methods through which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. While there are an infinite number of actions an attacker can perform after compromising an enterprise, there are a finite number of pathways. In this series, …
Presentations
Interested in securing your enterprise and Active Directory environment? Please visit TrimarcSecurity.com. Sean Metcalf, founder and Principal Consultant for Trimarc, has presented on security attack and defense at several major security conferences including: Black Hat USA (2015, 2016, 2018, 2019) BSides Charm (2015, 2016, 2017, 2018, 2019) BSides DC (2016) BSides PR (2019) DEF CON …
- 1
- 2

Recent Comments