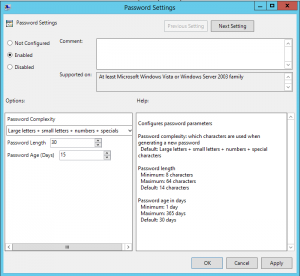
Over the years, there have been several methods attempted for managing local Administrator accounts: Scripted password change – Don’t do this. The password is exposed in SYSVOL. Group Policy Preferences. The credentials are exposed in SYSVOL. Password vault/safe product (Thycotic, CyberArk, Lieberman, Quest, Exceedium, etc). Microsoft Local Administrator Password Solution (LAPS). LAPS Overview Microsoft’s …
22 results for LAPS
May 29 2020
Attacking Active Directory Group Managed Service Accounts (GMSAs)
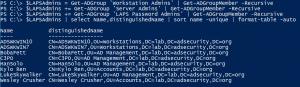
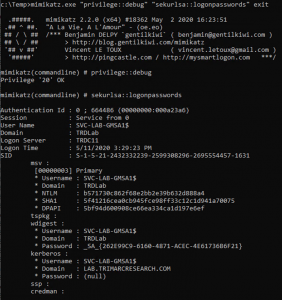
In May 2020, I presented some Active Directory security topics in a Trimarc Webcast called “Securing Active Directory: Resolving Common Issues” and included some information I put together relating to the security of AD Group Managed Service Accounts (GMSA). This post includes the expanded version of attacking and defending GMSAs I covered in the webcast.I …
Attack Defense & Detection
This page is meant to be a resource for Detecting & Defending against attacks. I provide references for the attacks and a number of defense & detection techniques. Active Directory & Windows Security ATTACK AD Recon Active Directory Recon Without Admin Rights SPN Scanning – Service Discovery without Network Port Scanning Beyond Domain Admins – …
Jan 01 2018
Attacking Read-Only Domain Controllers (RODCs) to Own Active Directory
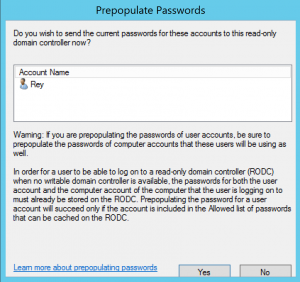
I have been fascinated with Read-Only Domain Controllers (RODCs) since RODC was released as a new DC promotion option with Windows Server 2008. Microsoft customers wanted a DC that wasn’t really a DC. – something that could be deployed in a location that’s not physically secure and still be able to authenticate users. This post …
Jul 06 2016
DEF CON 24 (2016) Talk – Beyond the MCSE: Red Teaming Active Directory
This August at DEF CON 24, I will be speaking about Active Directory security evaluation in my talk “Beyond the MCSE: Red Teaming Active Directory”. This talk is focused on the Red side of AD security, specifically how to best evaluate the security of AD and quickly identify potential security issues. Whether you perform “Red …
Mar 14 2016
Sneaky Active Directory Persistence #17: Group Policy
The content in this post describes a method through which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for about 5 minutes. Complete list of Sneaky Active Directory Persistence Tricks posts This post explores how an attacker could leverage the built-in Active Directory management capability called Group Policy …
Jan 27 2016
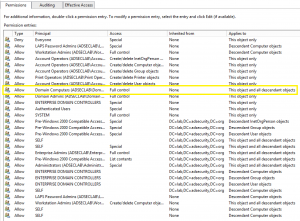
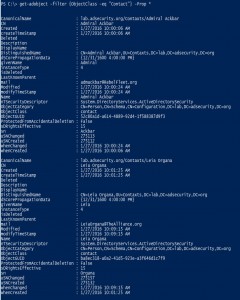
Active Directory Recon Without Admin Rights
A fact that is often forgotten (or misunderstood), is that most objects and their attributes can be viewed (read) by authenticated users (most often, domain users). The challenge is that admins may think that since this data is most easily accessible via admin tools such as “Active Directory User and Computers” (dsa.msc) or “Active Directory …


Recent Comments