The past couple of years of meeting with customers is enlightening since every environment, though unique, often has the same issues. These issues often boil down to legacy management of the enterprise Microsoft platform going back a decade or more. I spoke about Active Directory attack and defense at several security conferences this year including …
Category: ActiveDirectorySecurity
Sep 26 2015
Sneaky Active Directory Persistence Tricks
The content in this post links to several methods through which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. While there are an infinite number of actions an attacker can perform after compromising an enterprise, there are a finite number of pathways. In this series, …
Sep 25 2015
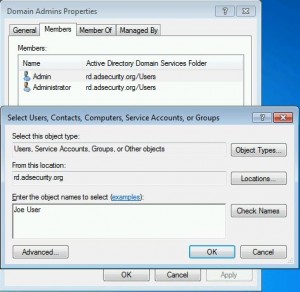
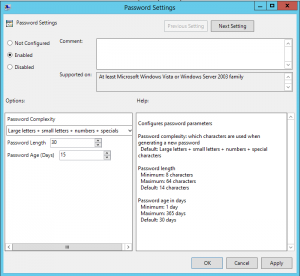
Sneaky Active Directory Persistence #15: Leverage AdminSDHolder & SDProp to (Re)Gain Domain Admin Rights
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method at DerbyCon (2015). Complete list of Sneaky Active Directory Persistence Tricks posts AdminSDHolder Overview AdminSDHolder is an object located in …
Sep 25 2015
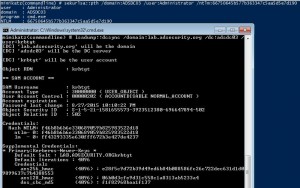
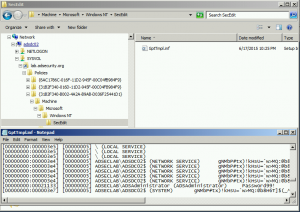
Sneaky Active Directory Persistence #13: DSRM Persistence v2
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method at DerbyCon (2015). I also presented and posted on DSRM as a persistence method previously. Complete list of Sneaky Active …
Sep 25 2015
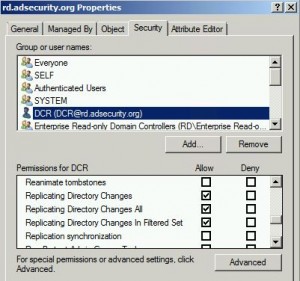
Mimikatz DCSync Usage, Exploitation, and Detection
Note: I presented on this AD persistence method at DerbyCon (2015). A major feature added to Mimkatz in August 2015 is “DCSync” which effectively “impersonates” a Domain Controller and requests account password data from the targeted Domain Controller. DCSync was written by Benjamin Delpy and Vincent Le Toux. The exploit method prior to DCSync was …
Sep 19 2015
Sneaky Active Directory Persistence #14: SID History
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts SID History is …
Sep 16 2015
Sneaky Active Directory Persistence #12: Malicious Security Support Provider (SSP)
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts The Security …
Sep 10 2015
DerbyCon V (2015): Red vs. Blue: Modern Active Directory Attacks & Defense Talk Detail
In a couple of weeks, I will be speaking at DerbyCon about Active Directory attack & defense in my talk Red vs. Blue: Modern Active Directory Attacks & Defense”. This is the 5th iteration of this talk and includes the latest updates to attack methods and defensive strategies. This DerbyCon version is a blend of …
Sep 10 2015
Sneaky Active Directory Persistence #11: Directory Service Restore Mode (DSRM)
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for 5 minutes. I presented on this AD persistence method in Las Vegas at DEF CON 23 (2015). Complete list of Sneaky Active Directory Persistence Tricks posts The Directory …

Recent Comments