Introduction There are several methods for identifying unusual or anomalous user activity. Traditionally these methods have required certain events be logged to the Windows event logs on workstations, servers, and Domain Controllers (DCs) and these events need to be forwarded to a central collection system. The drawback to this approach is numerous: the data logged …
29 results for Golden Ticket
Presentations
Interested in securing your enterprise and Active Directory environment? Please visit TrimarcSecurity.com. Sean Metcalf, founder and Principal Consultant for Trimarc, has presented on security attack and defense at several major security conferences including: Black Hat USA (2015, 2016, 2018, 2019) BSides Charm (2015, 2016, 2017, 2018, 2019) BSides DC (2016) BSides PR (2019) DEF CON …
Jan 19 2015
Attackers Can Now Use Mimikatz to Implant Skeleton Key on Domain Controllers & BackDoor Your Active Directory Forest
Once an attacker has gained Domain Admin rights to your Active Directory environment, there are several methods for keeping privileged access. Skeleton Key is an ideal persistence method for the modern attacker. More information on Skeleton Key is in my earlier post. Note that the behavior documented in this post was observed in a lab …
Nov 22 2014
Mimikatz and Active Directory Kerberos Attacks
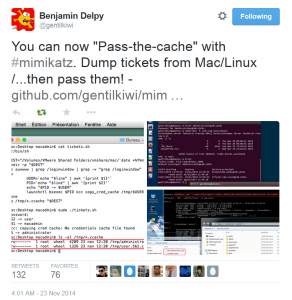
NOTE: While this page will remain, the majority of the Mimikatz information in this page is now in the “Unofficial Mimikatz Guide & Command Reference” which will be updated on a regular basis. Mimikatz is the latest, and one of the best, tool to gather credential data from Windows systems. In fact I consider Mimikatz …
Nov 19 2014
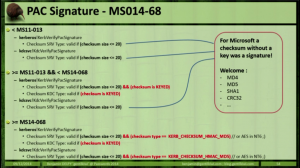
Kerberos Vulnerability in MS14-068 (KB3011780) Explained
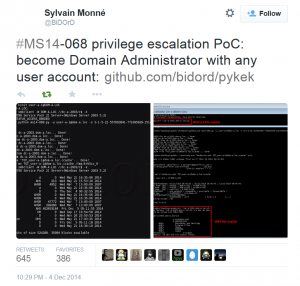
Thanks to Gavin Millard (@gmillard on Twitter), we have a graphic that covers the issue quite nicely (wish I had of thought of it!) Exploit Code is now on the net! As of December 4th, 2014, there is Proof of Concept (POC) code posted that exploits MS14-068 by Sylvain Monné by using Python to interact with …
Nov 18 2014
MS14-068: Vulnerability in (Active Directory) Kerberos Could Allow Elevation of Privilege
Active Directory leverages the Kerberos protocol for authentication. The vulnerability patches an issue with how the Domain Controller validates group membership in Kerberos tickets (hint: the ticket is always validated by the DC if the checksum is set to certain values). Microsoft KB3011780 patches this issue. According to Microsoft: “When this security bulletin was issued, …
Nov 10 2014
Kerberos & KRBTGT: Active Directory’s Domain Kerberos Service Account
Every Domain Controller in an Active Directory domain runs a KDC (Kerberos Distribution Center) service which handles all Kerberos ticket requests. AD uses the KRBTGT account in the AD domain for Kerberos tickets. The KRBTGT account is one that has been lurking in your Active Directory environment since it was first stood up. Each Active …
Security Resources
This page is a reference with security documents, posts, videos and presentations I find useful for staying up to date on current security issues and exploits. Last Updated: May 2016 Note that this page isn’t actively updated. Visit the Attack, Defense, & Detection page for updated content. Microsoft Enterprise & Active Directory Security Documents (& Blog …


Recent Comments