There are times when you want to know how long it takes for a script to run. One of the Measure-* cmdlets can be useful, but there is a simpler way to time how long it takes to run a script (or piece of code). The StopWatch .NET method is an ideal method for script …
Category: PowerShell
Nov 15 2014
Owning Networks and Evading Incident Response with PowerShell
PowerShell provides an easy method to bypass antivirus and other protection methods: Up until several months ago, I was a member of a penetration test team tasked with compromising data centers and evading detection. Industry standard tools such as Metasploit (an attack toolkit that includes a backdoor named Meterpreter) and Mimikatz (a password dumper) …
Nov 10 2014
Kerberos & KRBTGT: Active Directory’s Domain Kerberos Service Account
Every Domain Controller in an Active Directory domain runs a KDC (Kerberos Distribution Center) service which handles all Kerberos ticket requests. AD uses the KRBTGT account in the AD domain for Kerberos tickets. The KRBTGT account is one that has been lurking in your Active Directory environment since it was first stood up. Each Active …
Nov 09 2014
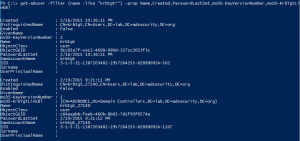
PowerShell Code: Check KRBTGT Domain Kerberos Account Last Password Change
From my GitHub Repo: Get-PSADForestKRBTGTInfo This function discovers all of the KRBTGT accounts in the forest using ADSI and returns the account info, specifically the last password change. Currently, the script performs the following actions: * Queries a Global Catalog in the Active Directory root domain for all KRBTGT accounts in the forest by querying …
Nov 08 2014
Hack Attack Method Whitepapers
The best way to develop the best defense is to study the offense’s methods. Here are several recent reports that detail current modern network attacks: Mandiant APT Whitepaper Microsoft Security Intelligence Report Verizon Enterprise DBIR 2014
Nov 06 2014
How Attackers Pull the Active Directory Database (NTDS.dit) from a Domain Controller
I performed extensive research on how attackers dump AD credentials, including pulling the Active Directory database (ntds.dit) remotely. This information is covered in two newer and greatly expanded posts: How Attackers Dump Active Directory Database Credentials Attack Methods for Gaining Domain Admin Rights in Active Directory The original post data follows: How Attackers Pull …
Nov 03 2014
PowerShell Code: ADSI Convert Domain Distinguished Name to Fully Qualified Domain Name
Convert Domain Distinguished Name to Fully Qualified Domain Name: $ADObjectDN = “CN=Object1,OU=OrgUnit1,DC=child,DC=domain,DC=com” [array]$ADObjectDNArray = $ADObjectDN -Split(“,DC=”) [int]$DomainNameFECount = 0 ForEach ($ADObjectDNArrayItem in $ADObjectDNArray) { IF ($DomainNameFECount -gt 0) …
Nov 03 2014
PowerShell for Pentesters
PowerShell is extremely useful for admins. This power is also extremely useful for attackers. There are several PowerShell tools specifically for increasing access on a network: PowerSploit PowerSploit – PowerShell based pentest tool set developed by Mattifestation. PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid reverse engineers, forensic analysts, …
Nov 02 2014
Windows 8: Using PowerShell to Decrypt Wireless SSID Passwords with NetSH
Show the saved password for SSID named “SSID_NAME” in Windows 8. ((netsh wlan show profiles name=”SSID_NAME” key=clear | select-string “Key Content” ) -split(” Key Content : “))[1]
Oct 31 2014
PowerShell Data Types
Useful table with Powershell’s data types and descriptions: [string] Fixed-length string of Unicode characters [array] Array of values [xml] Xml object [int] 32-bit signed integer [DateTime] Date and Time [long] 64-bit signed integer [decimal] 128-bit decimal value [single] Single-precision 32-bit floating point number [double] Double-precision 64-bit floating point number [char] A Unicode 16-bit character [byte] …

Recent Comments