In my previous post, “Detecting Kerberoasting Activity” I explain how Kerberoasting works and describe how to detect potential Kerberoasting activity. The trick to this is understanding what activity is normal in order to filter out the noise and increase the fidelity of the alert. This post describes how to filter from millions of events to …
Category: Technical Reference
Feb 05 2017
Detecting Kerberoasting Activity
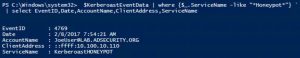
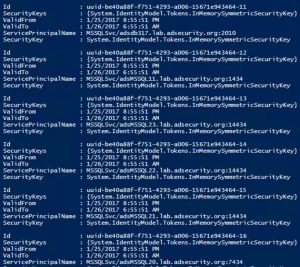
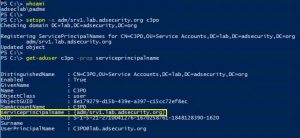
Introduction Kerberoasting can be an effective method for extracting service account credentials from Active Directory as a regular user without sending any packets to the target system. This attack is effective since people tend to create poor passwords. The reason why this attack is successful is that most service account passwords are the same length …
Nov 03 2016
Securing Domain Controllers to Improve Active Directory Security
Active Directory security effectively begins with ensuring Domain Controllers (DCs) are configured securely. At BlackHat USA this past Summer, I spoke about AD for the security professional and provided tips on how to best secure Active Directory. This post focuses on Domain Controller security with some cross-over into Active Directory security. The blog is called …
Aug 15 2016
Microsoft LAPS Security & Active Directory LAPS Configuration Recon
Over the years, there have been several methods attempted for managing local Administrator accounts: Scripted password change – Don’t do this. The password is exposed in SYSVOL. Group Policy Preferences. The credentials are exposed in SYSVOL. Password vault/safe product (Thycotic, CyberArk, Lieberman, Quest, Exceedium, etc). Microsoft Local Administrator Password Solution (LAPS). LAPS Overview Microsoft’s …
Aug 13 2016
PowerShell Security: PowerShell Attack Tools, Mitigation, & Detection
This post is a follow-up of sorts from my earlier posts on PowerShell, my PowerShell presentation at BSides Baltimore, and my presentation at DEF CON 24. Hopefully this post provides current information on PowerShell usage for both Blue and Red teams. Related posts: BSides Charm Presentation Posted: PowerShell Security: Defending the Enterprise from the Latest …
Mar 25 2016
DarkOperator.com: Using PowerShell to Gather Information from Active Directory
Carlos Perez (@DarkOperator) recently posted on DarkOperator.com how to use PowerShell to get data from Active Directory. He is working on an Active Directory audit PowerShell project and is documenting most of the work put into it. He also covers leveraging functions for portability and using Pester to write better PowerShell code (as well as …
Mar 14 2016
Sneaky Active Directory Persistence #17: Group Policy
The content in this post describes a method through which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for about 5 minutes. Complete list of Sneaky Active Directory Persistence Tricks posts This post explores how an attacker could leverage the built-in Active Directory management capability called Group Policy …
Mar 09 2016
Sneaky Active Directory Persistence #16: Computer Accounts & Domain Controller Silver Tickets
The content in this post describes a method by which an attacker could persist administrative access to Active Directory after having Domain Admin level rights for about 5 minutes. All posts in my Sneaky Active Directory Persistence Tricks series This post explores how an attacker could leverage computer account credentials to persist in an enterprise …

Recent Comments