I improve security for enterprises around the world working for TrimarcSecurity.com Read the About page (top left) for information about me. :) https://adsecurity.org/?page_id=8
Author's posts
May 20 2018
NolaCon (2018) Active Directory Security Talk Slides Posted
I recently presented my talk “Active Directory Security: The Journey” at Nolacon in New Orleans, LA. Slides are now posted here. On Sunday, May 19th, 2018, I spoke at NolaCon at 11am. Here’s the talk description: Active Directory is only the beginning. Attackers have set their sights squarely on Active Directory when targeting a company, though …
Jan 01 2018
Attacking Read-Only Domain Controllers (RODCs) to Own Active Directory
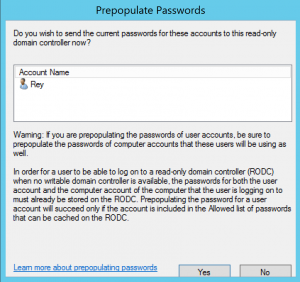
I have been fascinated with Read-Only Domain Controllers (RODCs) since RODC was released as a new DC promotion option with Windows Server 2008. Microsoft customers wanted a DC that wasn’t really a DC. – something that could be deployed in a location that’s not physically secure and still be able to authenticate users. This post …
Nov 24 2017
Securing Microsoft Active Directory Federation Server (ADFS)
Many organizations are moving to the cloud and this often requires some level of federation. Federation, put simply, extends authentication from one system (or organization) to another. Gerald Steere (@Darkpawh) and I spoke about cloud security at DEF CON in July 2017. Presentation slides and video are here: “Hacking the Cloud” One of the key …
May 30 2017
AD Reading: Windows Server 2016 Active Directory Features
The following are useful resources for Windows Server 2016 Active Directory Features. Windows 2016 Features What’s New in Windows 2016 Active Directory Windows Server 2016 AD Functional Level Privileged Access Management (PAM) Windows 2016 PAM Shadow Security Principals (temporary group membership) Azure AD Join Windows 2016 Azure AD Join Microsoft Hello …
May 01 2017
BSides Charm (2017) Talk Slides Posted – Detecting the Elusive: Active Directory Threat Hunting
I recently presented my talk “Detecting the Elusive: Active Directory Threat Hunting” at BSides Charm in Baltimore, MD. Slides are now posted in the Presentations section. I cover some of the information I’ve posted here before: PowerShell Security Detecting Kerberoasting: Part 1 and Part 2 On Sunday, April 30th, 2017, I spoke at BSides Charm in …
Feb 08 2017
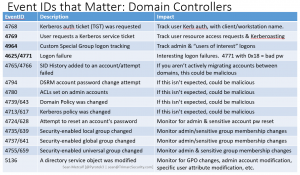
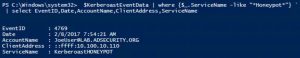
Detecting Kerberoasting Activity Part 2 – Creating a Kerberoast Service Account Honeypot
In my previous post, “Detecting Kerberoasting Activity” I explain how Kerberoasting works and describe how to detect potential Kerberoasting activity. The trick to this is understanding what activity is normal in order to filter out the noise and increase the fidelity of the alert. This post describes how to filter from millions of events to …


Recent Comments