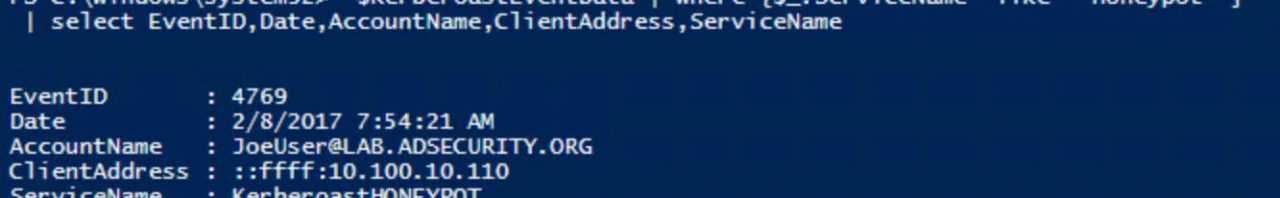
Detecting Kerberoasting Activity Part 2 – Creating a Kerberoast Service Account Honeypot
In my previous post, “Detecting Kerberoasting Activity” I explain how Kerberoasting works and describe how to detect potential Kerberoasting activity. The trick to this is understanding what activity is normal in order to filter out the noise and increase the fidelity of the alert. This post describes how to filter from millions of events to … Continue reading Detecting Kerberoasting Activity Part 2 – Creating a Kerberoast Service Account Honeypot